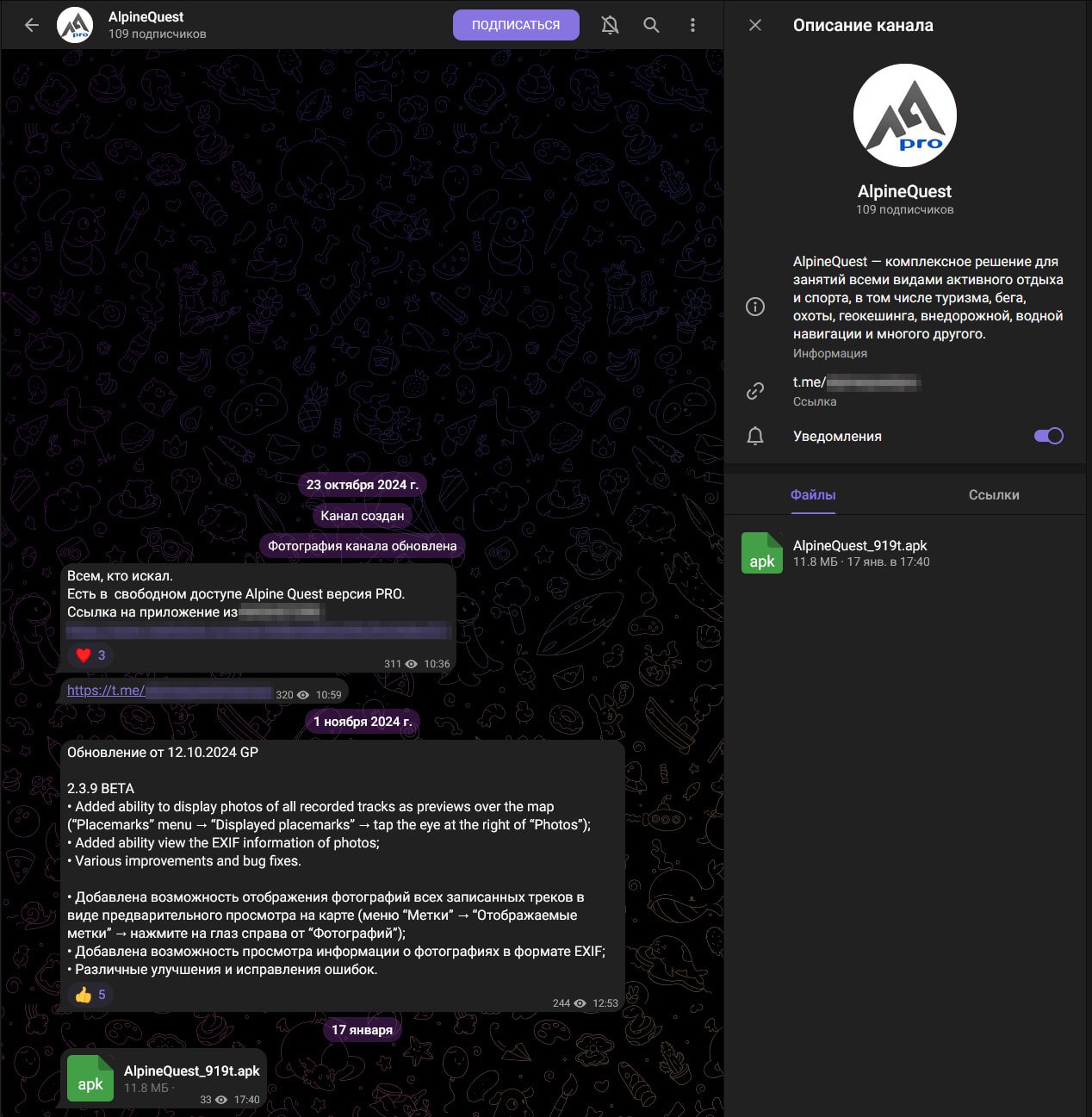
A new Android malware has been discovered hidden inside trojanized versions of the Alpine Quest mapping app, which is reportedly used by Russian soldiers as part of war zone operational planning.
Attackers promote the trojanized app as a free, cracked version of the premium Alpine Quest Pro, using Telegram channels and Russian app catalogs for distribution.
AlpineQuest is a legitimate GPS and topographic mapping app for Android used by adventurers, athletes, search-and-rescue teams, and military personnel, valued for its offline capabilities and precision.
The app has two versions: a free Lite version with limited features and a paid Pro version that is free of tracking libraries, analytics, and advertisements.
The spyware, which was discovered by researchers at Russian mobile antivirus company Doctor Web, hides inside a fully working Alpine Quest app, reducing suspicion and creating valuable data theft opportunities.
Once launched, it attempts to steal communication data and sensitive documents from the device, potentially revealing details about army operations. Specifically, the spyware performs the following actions:
- Sends the user’s phone number, contacts, geolocation, file info, and app version to attackers.
- Monitors location changes in real-time and sends updates to a Telegram bot.
- Downloads additional modules to steal confidential files, especially those sent via Telegram and WhatsApp.
- Seeks the ‘locLog’ file from Alpine Quest, which contains location history logs.
Doctor Web tracks the previously undocumented spyware as ‘Android.Spy. 1292.origin’ but did not make any attributions about its origin in its report. Indicators of compromise are available here.
Source: Doctor Web
Turning the tables
The tactic of targeting soldiers was previously associated with Russian hacking operations, often linked to state-sponsored threat groups collecting intelligence for the Russian army.
In December 2022, hackers using a compromised Ukrainian Ministry of Defense email account attempted subsequent infections by using DELTA, a Ukrainian intelligence collection and management system as bait.
In October 2024, the Russian threat group ‘UNC5812’ targeted Ukrainian conscripts with Windows and Android malware via a fake agency named ‘Civil Defense.’
More recently, in February 2025, Google researchers revealed that Russian threat actors of the APT44 group used malicious QR codes to trick targets into syncing their Signal accounts with unauthorized devices.
The discovery of the trojanized AlpineQuest app shows that these sneaky attacks are orchestrated from both ends of the conflict, as intelligence collection remains crucial in gaining battlefield advantage.
