RELATED NEWS
- Telekopye Toolkit Unveiled: ESET research exposes a potent phishing toolkit named Telekopye, designed by Russian hackers, enabling even inexperienced scammers to carry out phishing attacks without technical expertise.
- E-commerce Under Siege: Scammers leverage Telekopye to target popular Russian and non-Russian online marketplaces like OLX, Yula, JOFOGAS, BlaBlaCarm Sbazar, and eBay, causing concerns for both platforms and users.
- Neanderthal Scammers: ESET researchers have named the scammers utilizing Telekopye as Neanderthals, who employ deceptive tactics and social engineering to persuade victims into sharing sensitive information.
- Cryptocurrency Laundering: Once scammers acquire sensitive data, they employ it to launder cryptocurrency through cryptomixers, masking their stolen gains and complicating the tracking of funds.
- Hierarchical Scammer System: Telekopye’s unique shared account structure assigns different roles like administrators, moderators, and workers, each with distinct commission fees, creating a layered payment ecosystem for scammers.
According to the latest research from ESET, Russian hackers have come up with a new toolkit dubbed Telekopye allowing even novice scammers to conduct phishing attacks without any technical expertise.
Telekopye toolkit allows scammers to create phishing websites, send fraudulent SMS messages and emails, and target popular Russian and non-Russian online marketplaces, including OLX, Yula, JOFOGAS, BlaBlaCarm Sbazar, and eBay.
E-commerce platforms and users of these services have long been the targets of scammers and fraudsters. Radek Jizba, security researcher and the author of ESET’s blog post on Telekopye, wrote that the toolkit is named after its targeted platform Telegram, and Kopye is a Russian term for spear. Victims of Telekopye are referred to as Mammoths by the scammers, therefore, ESET researchers named the scammers as Neanderthals.
“We discovered the source code of a toolkit that helps scammers so much in their endeavours that they don’t need to be particularly well-versed in IT. Instead, they only need a silver tongue to persuade their victims.”
Radek Jizba -ESET
It is worth noting that researchers have detected various versions of this toolkit, the latest one seen in April 2023. Researchers believe that this toolkit has been available since 2015 and the language used in the comments in the code hints that its primary user base is in Russia, Uzbekistan, and Ukraine. Some of its versions can store sensitive user data such as payment card details or email addresses stored on the targeted system’s disk.
It is designed as a Telegram bot, which is added to a Telegram group chat and features several “easy to navigate” menus as clickable buttons to facilitate multiple Neanderthals. The information obtained from Telekopye is uploaded to VirusTotal. The toolkit comes with predesigned templates to create phishing pages, which further makes the job easier for the scammers.
Regarding how Mammoths are hunted by Telekopye operators, in their blog post, ESET researchers noted that the Neanderthals first gained the victim’s trust by claiming to be a legitimate entity and compelling them to visit a genuine-looking phishing web page sent to them via SMS or email. Victims are then tricked into entering sensitive data such as credentials or credit card details.
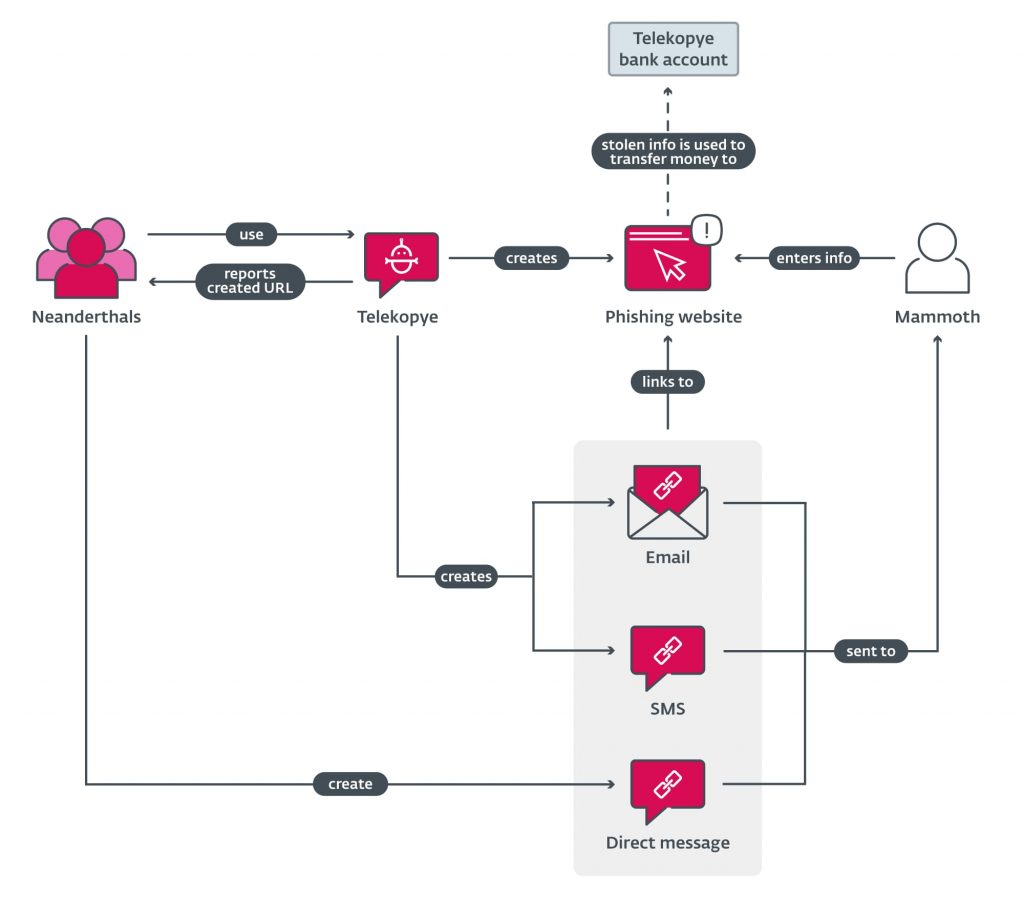
Once the information is obtained, the scammers can use it to launder cryptocurrency through cryptomixers to hide stolen money. However, researchers couldn’t determine how the scammers find their victims. They did note that stolen funds aren’t directly transferred to the scammers’ accounts because they use a shared Telekopye account, which is owned by the Telekopye administrator.
They also noted that Telekopye tracks every scammer’s success by featuring their individual contributions to the shared account and they are paid by the administrator accordingly. Interestingly, the shared account serves as a payment system for the scammers and there’s a hierarchical system in place where scammers are divided into different classes (administrators, moderators, good workers/support bots, workers, and blocked) with varying commission fees and perks.
The only way to prevent financial loss is to stay vigilant and avoid spending money to buy goods from online marketplaces unless fully confident about their legitimacy.
RELATED NEWS
- RIG Exploit Toolkit Distributing CeidPageLock Malware
- New credit card skimmers channel funds through Telegram
- New Phishing Attack Spoofs Microsoft 365 Authentication System
