Microsoft warns that a cyber-espionage group linked to Russia’s Federal Security Service (FSB) is targeting diplomatic missions in Moscow using local internet service providers.
The hacking group tracked by Microsoft as Secret Blizzard (also known as Turla, Waterbug, and Venomous Bear) has been observed exploiting its adversary-in-the-middle (AiTM) position at the internet service provider (ISP) level to infect the systems of diplomatic missions with custom ApolloShadow malware.
To do this, they redirect targets to captive portals, tricking them into downloading and executing a malware payload disguised as a Kaspersky antivirus installer.
Once deployed, ApolloShadow installs a trusted root certificate disguised as Kaspersky Anti-Virus, which helps trick compromised devices into recognizing malicious websites as legitimate, allowing threat actors to maintain long-term access for intelligence gathering after infiltrating diplomatic systems.
“This is the first time Microsoft can confirm Secret Blizzard’s capability to conduct espionage at the ISP level, meaning diplomatic personnel using local internet providers and telecommunications in Russia are at high risk of being targets of Secret Blizzard’s AiTM position within those services,” Microsoft said.
“This campaign, which has been ongoing since at least 2024, poses a high risk to foreign embassies, diplomatic entities, and other sensitive organizations operating in Moscow, particularly to those entities who rely on local internet providers.”
While Microsoft first detected the attacks in February 2025, the company believes this cyber-espionage campaign has been active since at least 2024.
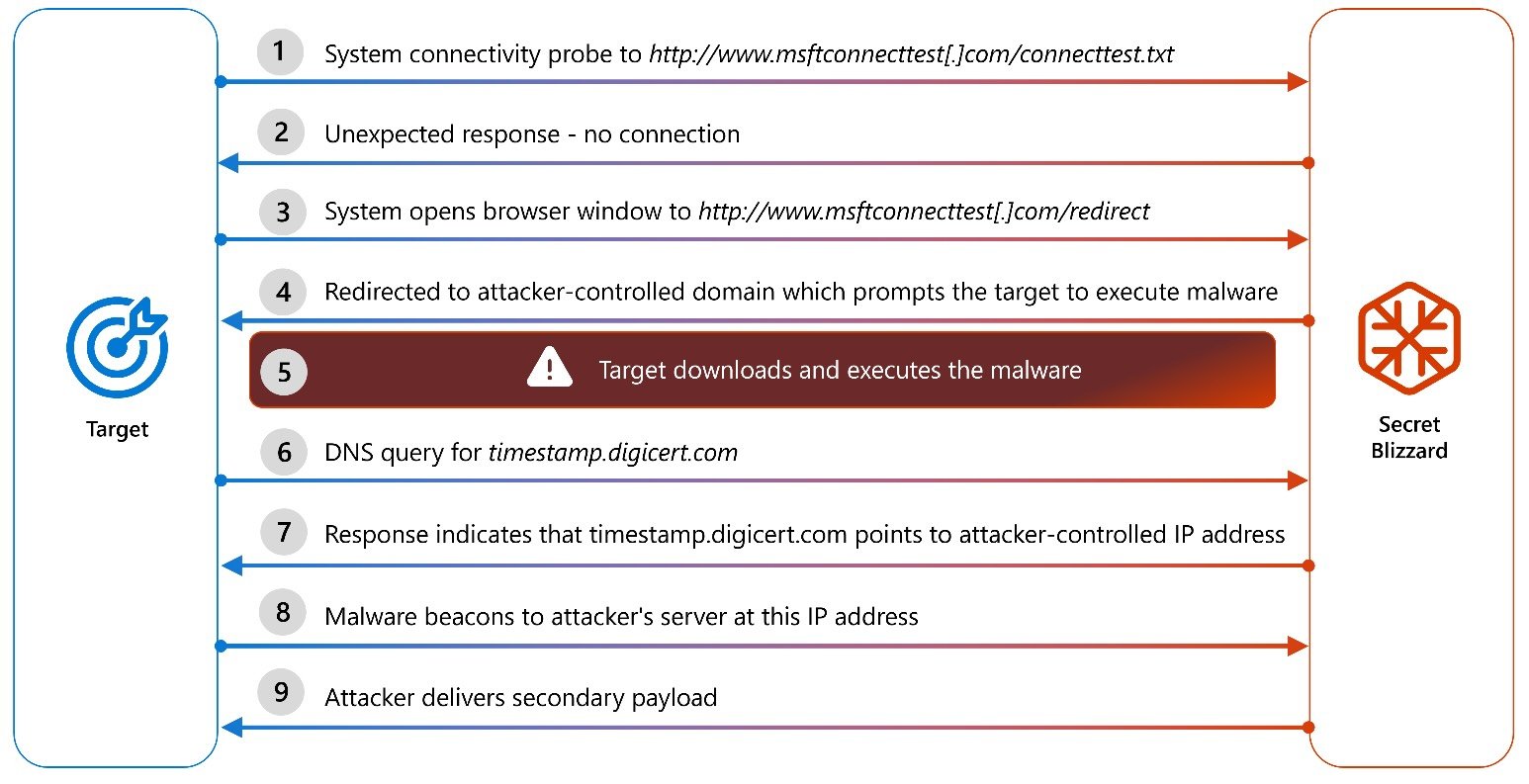
Secret Blizzard hackers are also taking advantage of Russia’s domestic interception systems, including the System for Operative Investigative Activities (SORM), to carry out their large-scale AiTM campaigns.
Unorthodox cyberspies focused on high-profile targets
Turla has been orchestrating cyber-espionage and information theft campaigns targeting embassies, governments, and research facilities across over 100 countries since at least 1996.
Two years ago, CISA linked the group to Center 16 of Russia’s Federal Security Service (FSB) and a peer-to-peer (P2P) network of computers infected with Snake cyber-espionage malware that was later taken down in a joint action involving Five Eyes cybersecurity and intelligence agencies.
These Russian state-backed hackers are also the primary suspects behind attacks targeting the U.S. Central Command, NASA, the Pentagon, multiple Eastern European Ministries of Foreign Affairs, the Finnish Foreign Ministry, and EU governments and embassies.
This threat group is known for its unconventional tactics, including the control of malware through comments on Britney Spears’ Instagram photos and the use of backdoor trojans with their own APIs.
Turla also utilized the hijacked infrastructure and malware of the Iranian APT OilRig in their own campaigns to mislead and deceive defenders into attributing their attacks to Iranian state hackers.
Most recently, they’ve also been spotted hijacking the infrastructure of Pakistani threat actor Storm-0156 to target Ukrainian military devices connected via Starlink.

Contain emerging threats in real time – before they impact your business.
Learn how cloud detection and response (CDR) gives security teams the edge they need in this practical, no-nonsense guide.




