The Sandworm Russian military cyber-espionage group is targeting Windows users in Ukraine with trojanized Microsoft Key Management Service (KMS) activators and fake Windows updates.
These attacks likely started in late 2023 and have now been linked by EclecticIQ threat analysts with Sandworm hackers based on overlapping infrastructure, consistent Tactics, Techniques and Procedures (TTPs), and frequently used ProtonMail accounts to register domains used in the attacks.
The attackers also used a BACKORDER loader to deploy DarkCrystal RAT (DcRAT) malware (used in previous Sandworm attacks) and debug symbols referencing a Russian-language build environment, further reinforcing the researchers’ confidence that Russian military hackers were involved.
EclecticIQ identified seven malware distribution campaigns tied to the same malicious activity cluster, each using similar lures and TTPs. Most recently, on 12 January 2025, the analysts observed the attacks infecting victims with the DcRAT remote access Trojan in data exfiltration attacks using a typo-squatted domain.
Once deployed on a victim’s device, the fake KMS activation tool displays a fake Windows activation interface, installs the malware loader, and disables Windows Defender in the background before delivering the final RAT payload.
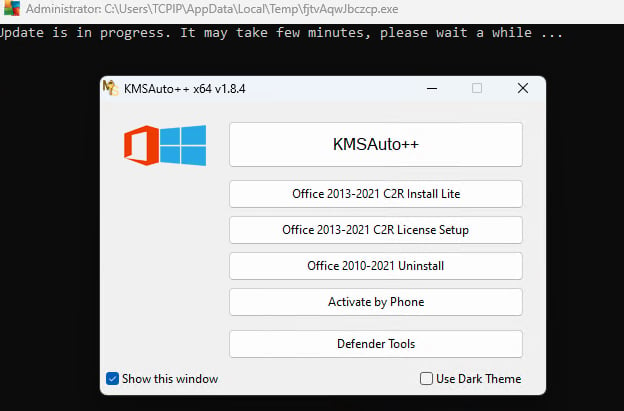
The attacks’ end goal is to collect sensitive information from infected computers and send it to attacker-controlled servers. The malware steals keystrokes, browser cookies, browser history, saved credentials, FTP credentials, system information, and screenshots.
Sandworm’s use of malicious Windows activators was likely prompted by the vast attack surface opened by the heavy use of pirated software in Ukraine, which also plagues the country’s government sector.
“Many users, including businesses and critical entities, have turned to pirated software from untrusted sources, giving adversaries like Sandworm (APT44) a prime opportunity to embed malware in widely used programs,” EclecticIQ said.
“This tactic enables large-scale espionage, data theft, and network compromise, directly threatening Ukraine’s national security, critical infrastructure, and private sector resilience.”
Sandworm (also tracked as UAC-0113, APT44, and Seashell Blizzard) is a hacking group active since at least 2009 and part of the Military Unit 74455 of the Main Intelligence Directorate (GRU), Russia’s military intelligence service, primarily focused on carrying out disruptive and destructive attacks targeting Ukraine.




