The mayor of Saint Paul, Minnesota’s capital city, has confirmed that the Interlock ransomware gang is responsible for a cyberattack that disrupted many of the city’s systems and services in July.
On July 29th, Minnesota Governor Tim Walz activated the National Guard in response to the crippling cyberattack that had affected St. Paul’s digital services and critical systems.
The city requested Minnesota National Guard’s cyber protection support due to the cyberattack’s impact exceeding St. Paul’s incident response capacity.
“While many city services remain available, some may be temporarily delayed or disrupted due to limited system access. We appreciate your patience and understanding as we work to bring systems fully back online,” the city says.
“Online payments are currently unavailable. No late fees will be assessed during this period. Additional billing and service updates will be shared once systems are restored.”
The city is still working with local, state, and federal partners to investigate the late July attack and restore full system functionality, but says that emergency services have been unaffected.
On Monday, Mayor Malvin Carter confirmed that the Interlock ransomware group was behind the attack, adding that the incident doesn’t affect residents’ personal or financial information and that the city refused to pay the gang’s ransom demand.
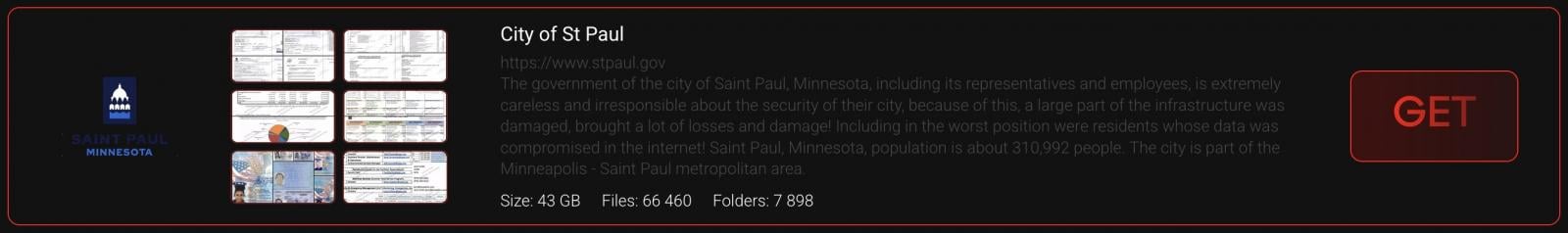
The ransomware gang added the City of Saint Paul to its dark web portal earlier this week, claiming that they had stolen over 66,000 files or 43 GB worth of data, some of which has now been published on the group’s leak site.
“A large part of the infrastructure was damaged, brought a lot of losses and damage! Including in the worst position were residents whose data was compromised,” the gang claimed.
Interlock surfaced in September 2024 and has since breached victims worldwide across various industry sectors, with a focus on healthcare organizations.
This ransomware gang was previously linked to ClickFix attacks and malware attacks in which they deployed a remote access trojan called NodeSnake on the networks of multiple U.K. universities.
More recently, Interlock also claimed responsibility for breaching and stealing 1.5 terabytes of data from DaVita, a Fortune 500 company specializing in kidney care, and for hacking Kettering Health, a healthcare giant with over 120 outpatient facilities and more than 15,000 employees.
Days before the St. Paul ransomware attack, CISA and the FBI warned about increased Interlock ransomware activity targeting critical infrastructure organizations in double extortion attacks, sharing mitigation measures to defend against this ransomware gang’s attacks.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
