Salat Stealer has emerged as a pervasive threat targeting Windows endpoints with a focus on harvesting browser-stored credentials and cryptocurrency wallet data.
First detected in August 2025, this Go-based infostealer leverages a range of evasion tactics, including UPX packing and process masquerading, to slip past conventional defenses.
Its operators advertise the malware through social engineering campaigns on mainstream platforms, promoting fake software cracks and game cheats that deliver the initial payload.
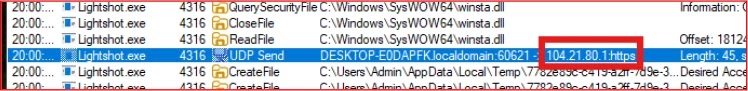
Upon execution, Salat Stealer silently injects itself into trusted directories under names like Lightshot.exe and Procmon.exe, blending with legitimate processes to avoid suspicion.
Cyfirma researchers identified the malware’s multi-layered approach within days of its initial sightings.
The threat employs both registry run keys and scheduled tasks to maintain persistence, creating entries under names such as RuntimeBroker and Lightshot that execute at logon and repeat every three minutes for an extended period.
Packed with UPX 4.1.0, the binary’s high entropy value of 7.999 disguises its true behavior until runtime.
Dynamic analysis revealed that child processes spawn under familiar file paths—C:Program Files (x86)Windows NTLightshot.exe, for example—making detection by endpoint agents more challenging.
Cyfirma analysts noted that Salat Stealer’s communication with its command-and-control (C2) infrastructure is both resilient and covert.
Initial contact uses lightweight UDP packets of approximately 45 bytes sent to IP 104.21.80.1, likely serving as keep-alive beacons.
In parallel, the stealer establishes an encrypted HTTPS channel to salat.cn/salat, with DNS resolutions pointing to 172.67.194.254 and 104.21.60.88.
When this primary domain is unreachable, a built-in JavaScript routine fetches a list of fallback domains—‘webrat.in’, ‘webrat.top’, and others—from sniff_domain_list.txt, iterating through each via calls to /alive.php until it locates an active panel for redirection.
The impact of Salat Stealer extends beyond simple credential theft, as it also targets browser extensions for cryptocurrency wallets such as MetaMask, Trust Wallet, and Phantom.
.webp)
By scanning the Chrome extension settings directory, the malware extracts seed phrases and private keys, putting users at risk of irreversible financial loss.
A similar approach applied to desktop wallet applications—including Electrum, Exodus, and Coinomi—allows the stealer to harvest wallet databases and configuration files.
All exfiltrated data is temporarily stored in the Temp folder under randomized filenames before transmission to the C2 panel.
Infection and Persistence Mechanisms
Salat Stealer’s infection chain begins with a social engineering lure that convinces the victim to execute a malicious archive.
Upon launch, the executable unpacks itself using UPX and immediately spawns child processes that masquerade as legitimate utilities.
.webp)
Persistence is achieved through dual mechanisms: registry run keys and scheduled tasks.
The following code snippet, part of the “Defender Excluder” script module available in the C2 panel, exemplifies how the malware hardens its foothold:-
if (Get-Command Add-MpPreference -ErrorAction SilentlyContinue) {
$ProgramFilesX86 = [System.Environment]::GetFolderPath("ProgramFilesX86")
Add-MpPreference -ExclusionPath $ProgramFilesX86
$AppData = [System.Environment]::GetFolderPath("ApplicationData")
Add-MpPreference -ExclusionPath $AppData
$LocalAppData = [System.Environment]::GetFolderPath("LocalApplicationData")
Add-MpPreference -ExclusionPath $LocalAppData
}This script quietly adds critical directories to Windows Defender’s exclusion list, ensuring that neither the main payload nor its auxiliary tools are scanned.
.webp)
Simultaneously, tasked entries named Lightshot and RuntimeBroker are configured to trigger at every logon and at scheduled intervals.
By combining registry and task scheduler techniques, Salat Stealer sustains long-term access and evasion, demonstrating the growing sophistication of modern MaaS operations.
Boost your SOC and help your team protect your business with free top-notch threat intelligence: Request TI Lookup Premium Trial.
