Salesforce today unveiled its comprehensive Forensic Investigation Guide, equipping organizations with best practices, log analysis techniques, and automation workflows to detect and respond to sophisticated security breaches rapidly.
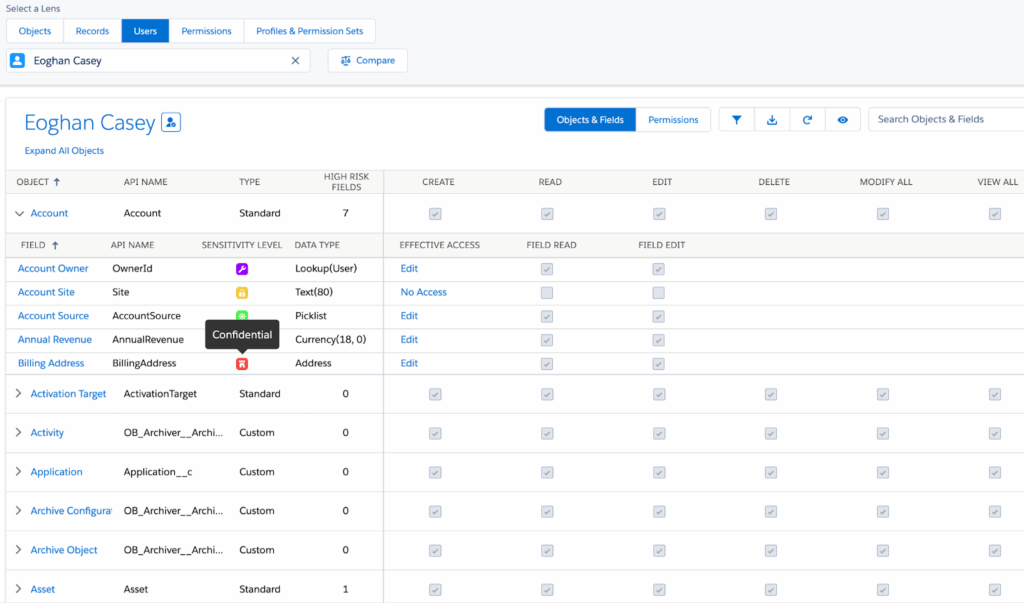
To reconstruct attack timelines and assess data exposure, the guide emphasizes three primary information sources: Activity Logs, User Permissions, and Backup Data.
Key Takeaways
1. Salesforce’s new Forensic Investigation Guide outlines how to leverage Holistic log and backup use for incident reconstruction.
2. Granular API event details to pinpoint data exfiltration.
3. Real-time security policies for automated threat containment.
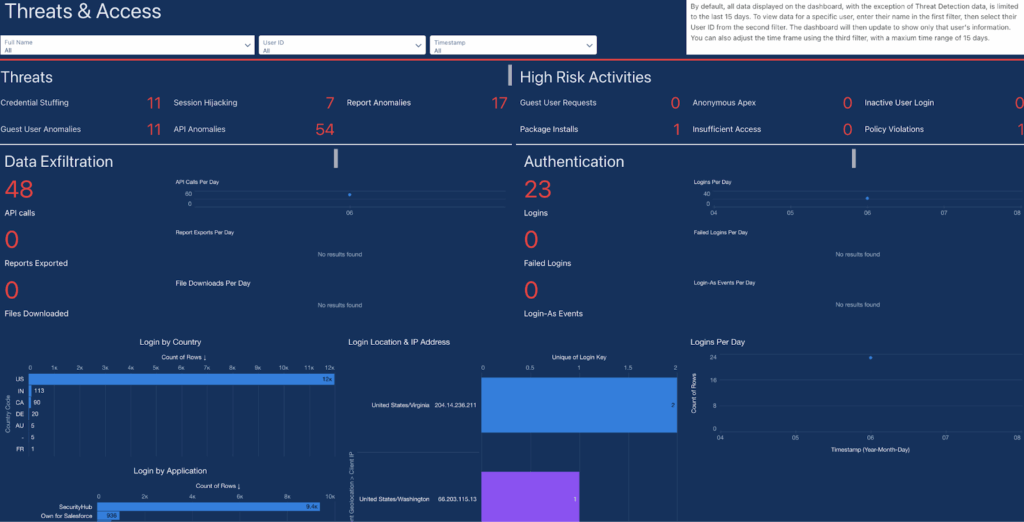
Administrators should enable Shield Event Monitoring for real-time visibility into API calls, report exports, and file downloads.
The guide highlights three Event Monitoring sources:
- Real Time Event Monitoring (RTEM) – streams threat detection alerts using statistical and machine learning methods to flag anomalies
- Event Log Objects (ELO) – delivers low-latency records via Platform APIs for near real-time queries
- Event Log Files (ELF) – provides comprehensive logs in CSV format for historic analysis
By comparing ELF.ReportExport, ELO.ReportEventLog, and RTEM.ReportEventStream fields, investigators can pinpoint exactly which records and fields were accessed, with RTEM providing the most detailed context on queried entities and session parameters.
Automated Response with Transaction Security Policies
The guide also details how to leverage Enhanced Transaction Security Policies (TSP) to enact real-time countermeasures.

Security teams can define policy rules to automatically block sensitive report downloads, trigger multi-factor authentication challenges, or create incident cases via workflow. For example, a Guest User Anomaly alert on a Digital Experience portal can activate a TSP that:
- Blocks unauthorized AuraRequest events
- Sends an immediate Slack notification
- Requires MFA for any subsequent data access
Such automation ensures that suspicious actions like abnormal API volumes or unexpected file exports are halted before data exfiltration can escalate.
Organizations following the principle of least privilege across Profiles, Permission Sets, Sharing Rules, and Role Hierarchies will find forensic readiness significantly enhanced.
The guide recommends regular comparative analysis of backup snapshots using Backup & Recover, and continuous log streaming to centralized SIEM platforms for early anomaly detection.
With the Salesforce Forensic Investigation Guide, enterprises are now armed to accelerate root-cause analysis, minimize downtime, and uphold data integrity in the face of evolving cloud-native threats.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.