Threat actors often make use of weaponized PDF files as they enable them to deliver malware and execute attacks through phishing schemes.
These PDFs can contain embedded malicious code, links, and scripts that exploit vulnerabilities in PDF readers, making them a preferred method for evading traditional security measures.

Kaspersky Lab researchers recently discovered that SambaSpy has been actively attacking Windows users with weaponized PDF files.
SambaSpy Attacking Windows Users
In May 2024, cybersecurity researchers uncovered a highly targeted malware campaign focusing primarily on Italian users.
This campaign employed a sophisticated infection chain, and this chain begins with phishing emails purportedly from a legitimate “Italian real estate company.”
Decoding Compliance: What CISOs Need to Know – Join Free Webinar
These emails contained links redirecting victims through multiple stages like legitimate sites (“FattureInCloud”) and malicious servers using “ngrok.”
Threat actors implemented strict checks at various points to ensure only Italian-language users on specific browsers (Edge, Firefox, and Chrome) were infected.
The final payload is a Java-based RAT dubbed “SambaSpy,” and it was delivered via a JAR file hosted on MediaFire.


SambaSpy is obfuscated using Zelix KlassMaster, and it offers an extensive range of malicious capabilities that we have mentioned below:-
- File system manipulation
- Process management
- Keylogging (using JNativeHook)
- Clipboard control
- Webcam access
- Screen capture
- Remote desktop functionality
- Browser credential theft (targeting Chrome, Edge, Opera, Brave, Iridium, and Vivaldi)
- Ability to load additional plugins at runtime
Besides this, the RAT also implemented anti-VM techniques to evade detection, and for dynamic plugin loading, it utilized Java’s URLClassLoader.
This campaign’s focus and technical sophistication highlight an evolving trend in targeted cyberattacks.
The malicious actor took a complex approach by employing multiple stages of infection, including language checks to detect Italian scope and parameters.
They also made use of a legitimate invoice that acted as a vector to spread malware.

The campaign made use of a custom downloader with code comments and error messages in Brazilian Portuguese.
Here the threat actors often changed their strategies like obfuscation methods, phishing email content, and command-and-control (C2) endpoints.
Besides this, the attackers consistently reused second-level domains by providing insight into their infrastructure.
This pattern of infrastructure reuse, combined with language artifacts and targeting strategies, offers valuable indicators for attribution and enhances malware detection capabilities, Kaspersky said.
The campaign illustrates a trend of Latin American attackers targeting European countries with linguistically similar backgrounds.
Multiple language verification steps were implemented throughout the infection chain, which shows a focused approach to victim selection.
The rapidly evolving nature of attackers and their tactics creates challenges for cybersecurity researchers in tracking and mitigating such evolving threats.
IoCs
e6be6bc2f8e27631a7bfd2e3f06494aa Malicious PDF
1ec21bd711b491ad47d5c2ef71ff1a10 Downloader
d153006e00884edf7d48b9fe05d83cb4 Dropper
0f3b46d496bbf47e8a2485f794132b48 SambaSpy
Domain names embedded in email messages
officediraccoltaanabelacosta[.]net
belliniepecuniaimmobili[.]com
immobilibelliniepecunia[.]xyz
immobilibelliniepecunia[.]online
immobilibelliniepecunia[.]site
bpecuniaimmobili[.]online
bpecuniaimmobili[.]info
belliniepecuniaimmobilisrl[.]shop
belliniepecuniaimmobilisrl[.]online
belliniepecuniaimmobilisrl[.]xyz
belliniepecuniaimmobili.com[.]br
bpecuniaimmobili[.]xyz
immobilibelliniepecunia[.]shop
immobilibelliniepecunia[.]me
immobiliarebelliniepecunia[.]info
immobiliarebelliniepecunia[.]online
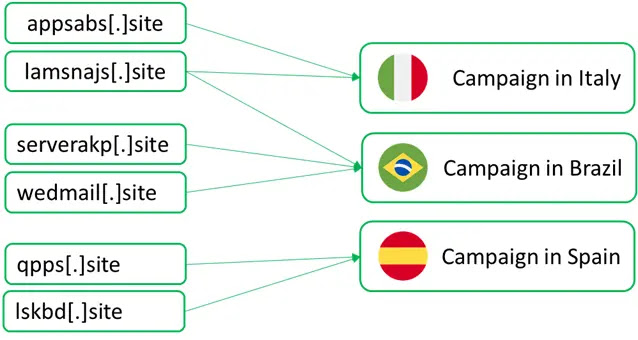
Domain names used to distribute malware
lamsnajs[.]site
appsabs[.]site
qpps[.]site
lskbd[.]site
serverakp[.]site
wedmail[.]site66d68ce73c83226a.ngrok[.]app
hxxps://1drv[.]ms/b/s!AnMKZoF8QfODa92x201yr0GDysk?e=ZnX3Rm PDF hosted on OneDrive
hxxps://moduloj.lamsnajs[.]site/Modulo32.jpg URL embedded in downloader
Are You From SOC/DFIR Teams? - Try Advanced Malware and Phishing Analysis With ANY.RUN - 14-day free trial





