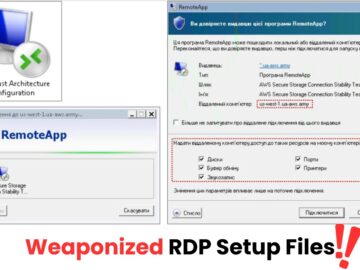
The Russia-aligned Sandworm threat group has intensified its destructive cyberattacks against Ukrainian organizations, deploying sophisticated data wiper malware designed to cripple critical infrastructure and economic operations.
Unlike traditional cyberespionage campaigns, Sandworm’s recent operations focus exclusively on destruction, targeting governmental entities, energy providers, logistics companies, and the grain sector with malicious tools named ZEROLOT and Sting.
These attacks aim to weaken Ukraine’s economic stability during an ongoing geopolitical conflict, demonstrating the group’s strategic shift from intelligence gathering to causing maximum disruption.
The campaign specifically targets critical sectors vital to Ukraine’s economy and national security.
The threat actor has concentrated efforts on governmental organizations responsible for administrative functions, energy companies managing power infrastructure, logistics operations supporting supply chains, and agricultural entities within the grain sector.
Welivesecurity security researchers identified this coordinated assault as part of Sandworm’s broader strategy to destabilize Ukrainian operations through permanent data loss.
The deployment of data wipers represents a dangerous escalation in cyber warfare tactics, as these tools are designed to render systems completely inoperable by permanently erasing data and corrupting file systems.
.webp)
The malware operates by exploiting vulnerabilities in target networks through spearphishing campaigns and compromised credentials.
Once inside the network, ZEROLOT and Sting execute destructive routines that overwrite critical system files, partition tables, and stored data with random values, making recovery virtually impossible without offline backups.
Wiper Deployment
The data wipers employ advanced techniques to maximize damage before detection.
ZEROLOT specifically targets Master Boot Records and file allocation tables, ensuring that operating systems cannot boot after the attack completes.
The malware includes anti-forensic capabilities that delete event logs and system restore points, eliminating evidence of the intrusion.
Sting operates with elevated privileges obtained through credential theft and privilege escalation exploits, allowing unrestricted access to protected system areas.
Both wipers incorporate timing mechanisms that delay execution until achieving maximum network propagation, ensuring widespread impact across connected infrastructure before security teams can respond effectively to the threat.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.