Russia-aligned threat actor Sandworm has intensified its destructive cyber operations against Ukrainian organizations, deploying data wiper malware to cripple critical infrastructure and weaken the nation’s economy.
Unlike other Russia-aligned advanced persistent threat groups that primarily engage in cyberespionage activities, Sandworm’s operations are characterized by their explicitly destructive intent.
According to the latest ESET APT Activity Report covering Q2 2025 through Q3 2025, the notorious hacking group has launched targeted attacks against governmental entities, energy companies, logistics providers, and notably, the grain sector, using sophisticated data wipers identified as ZEROLOT and Sting.
The group’s focus on data destruction rather than intelligence gathering underscores the strategic objective of causing maximum disruption to Ukraine’s economic and operational capabilities during the ongoing conflict.
The data wipers deployed by Sandworm represent a significant escalation in cyber warfare tactics. ZEROLOT and Sting are explicitly designed to irreversibly destroy data on compromised systems, rendering them inoperable and causing substantial operational disruption to targeted organizations.
These malware families function by overwriting critical files and system data, making recovery extremely difficult or impossible without comprehensive backup systems in place.
The deployment of these wipers demonstrates Sandworm’s sophisticated operational capabilities and their strategic approach to cyber warfare.
Rather than maintaining persistent access for long-term espionage, the group prioritizes immediate, catastrophic damage to critical systems.
This destructive approach aligns with the broader pattern of Russia-aligned threat actors maintaining their focus on Ukraine and countries with strategic ties to Ukraine, as documented throughout the April to September 2025 monitoring period.
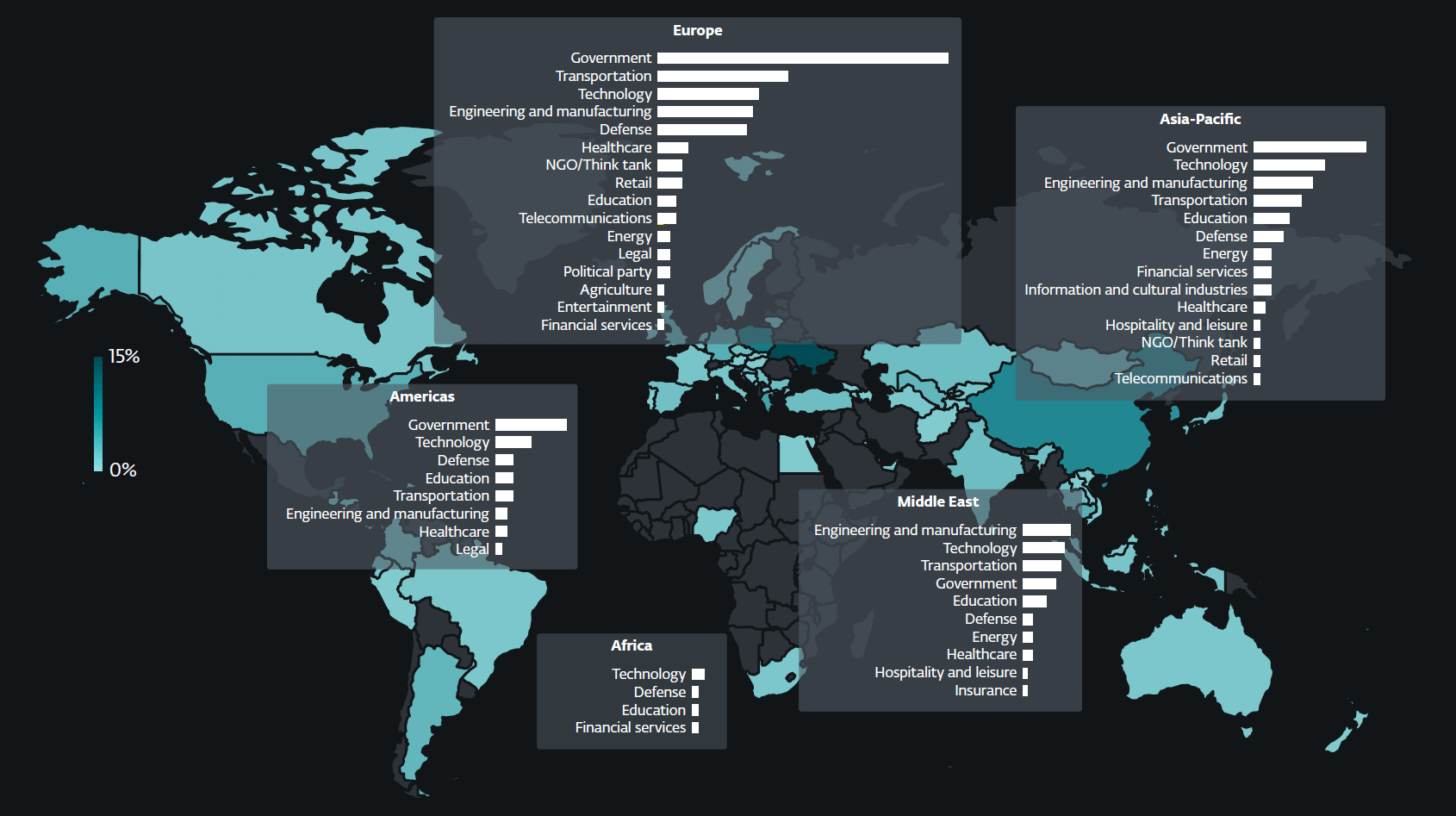
Strategic Targeting of Critical Sectors
Sandworm’s targeting strategy reveals a calculated approach aimed at undermining Ukraine’s economic stability and operational resilience.

The attacks against governmental entities threaten essential public services and administrative functions, while compromises in the energy and logistics sectors can cascade into broader economic disruption affecting millions of citizens.
The group’s particular focus on the grain sector represents a strategic effort to target one of Ukraine’s most significant economic assets.
As a major global grain exporter, disruptions to Ukraine’s agricultural industry have far-reaching implications not only for the national economy but also for global food security.
By deploying data wipers against grain sector organizations, Sandworm aims to destabilize supply chains, disrupt export capabilities, and inflict economic damage that extends beyond Ukraine’s borders.
Broader Threat Landscape
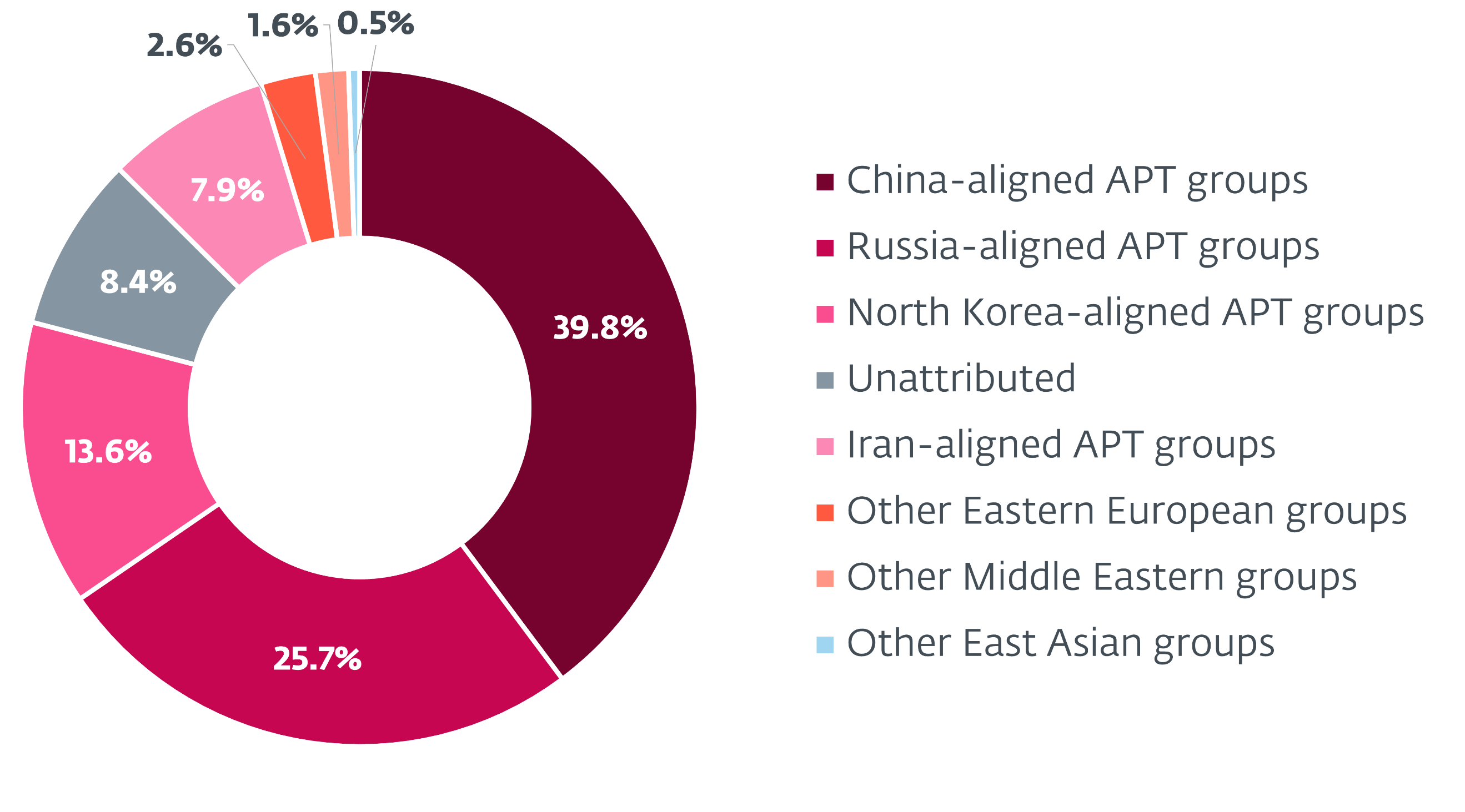
Sandworm’s activities occur within a broader context of intensified cyber operations by Russia-aligned groups.
While Sandworm concentrates on destructive attacks, other groups like Gamaredon have maintained high-intensity cyberespionage operations against Ukraine, with spearphishing remaining the primary method of initial compromise across these threat actors.
The ESET report documents an unprecedented surge in activity by Gamaredon, which included a rare instance of cooperation between Russia-aligned APT groups when Gamaredon selectively deployed one of Turla’s backdoors.
This collaboration highlights the increasingly sophisticated and coordinated nature of state-sponsored cyber threats targeting Ukraine.
As these groups continue to expand their operations to European entities and countries with strategic ties to Ukraine, organizations must maintain robust cybersecurity postures, implement comprehensive backup strategies, and remain vigilant against evolving wiper malware threats that can cause irreversible damage within minutes of deployment.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
