Cybersecurity researchers at Rapid7 Labs have uncovered a sophisticated new threat: SantaStealer, a malware-as-a-service information stealer actively promoted on Telegram channels and underground hacker forums.
The malware, which recently rebranded from “BluelineStealer,” is scheduled for release before the end of 2025 and represents a growing threat to users worldwide due to its ability to exfiltrate sensitive data while operating entirely in memory to evade detection.
SantaStealer is designed to collect and exfiltrate a comprehensive range of sensitive information including documents, credentials, cryptocurrency wallets, and data from numerous applications.
The stolen data is compressed, divided into 10 MB chunks, and transmitted to command-and-control servers over unencrypted HTTP connections.
The malware operators advertise their product as “fully written in C” with a “custom C polymorphic engine” that claims to be “fully undetected,” though Rapid7’s analysis reveals a different picture.
The discovery occurred in early December 2025 when Rapid7 identified a Windows executable that triggered generic infostealer detection rules typically associated with the Raccoon stealer family.
Analysis of the sample revealed a 64-bit DLL containing over 500 exported symbols with descriptive names such as “payload_main,” “check_antivm,” and “browser_names,” along with numerous unencrypted strings indicating credential-stealing capabilities.
Technical Architecture
The malware exhibits a modular, multi-threaded design featuring 14 different specialized modules.
These include generic modules for reading environment variables and taking screenshots, as well as specialized modules targeting Telegram desktop, Discord, Steam, browser extensions, browsing histories, and passwords.
For Chromium-based browsers, SantaStealer employs techniques to bypass AppBound Encryption by embedding an additional executable that appears to be based on the ChromElevator project, which uses direct syscall-based reflective process hollowing to hijack legitimate browser processes.
The statically linked libraries identified in the malware include cJSON for JSON parsing, miniz as a zlib-replacement library, and sqlite3 for interfacing with SQLite databases.
SantaStealer incorporates several anti-analysis features that vary across samples, suggesting ongoing development.
These include checks for blocked processes through custom rolling checksums, suspicious computer names, hard-coded analysis environment directories, system uptime verification, and time-based debugger detection.
Interestingly, the malware includes an optional check for Commonwealth of Independent States countries, where it detects Russian keyboard layouts using the GetKeyboardLayoutList API and terminates execution if configured to avoid CIS targets.
Pricing and Commercial Model
The threat actors behind SantaStealer operate a sophisticated affiliate program accessible through a web panel where users can register accounts and access feature lists, pricing models, and build configuration options.
The malware configuration is stored as JSON-encoded data and consists of a banner with Unicode art spelling “SANTA STEALER” and a link to the stealer’s Telegram channel.
The basic variant is priced at $175 per month, while a premium variant costs $300 per month.
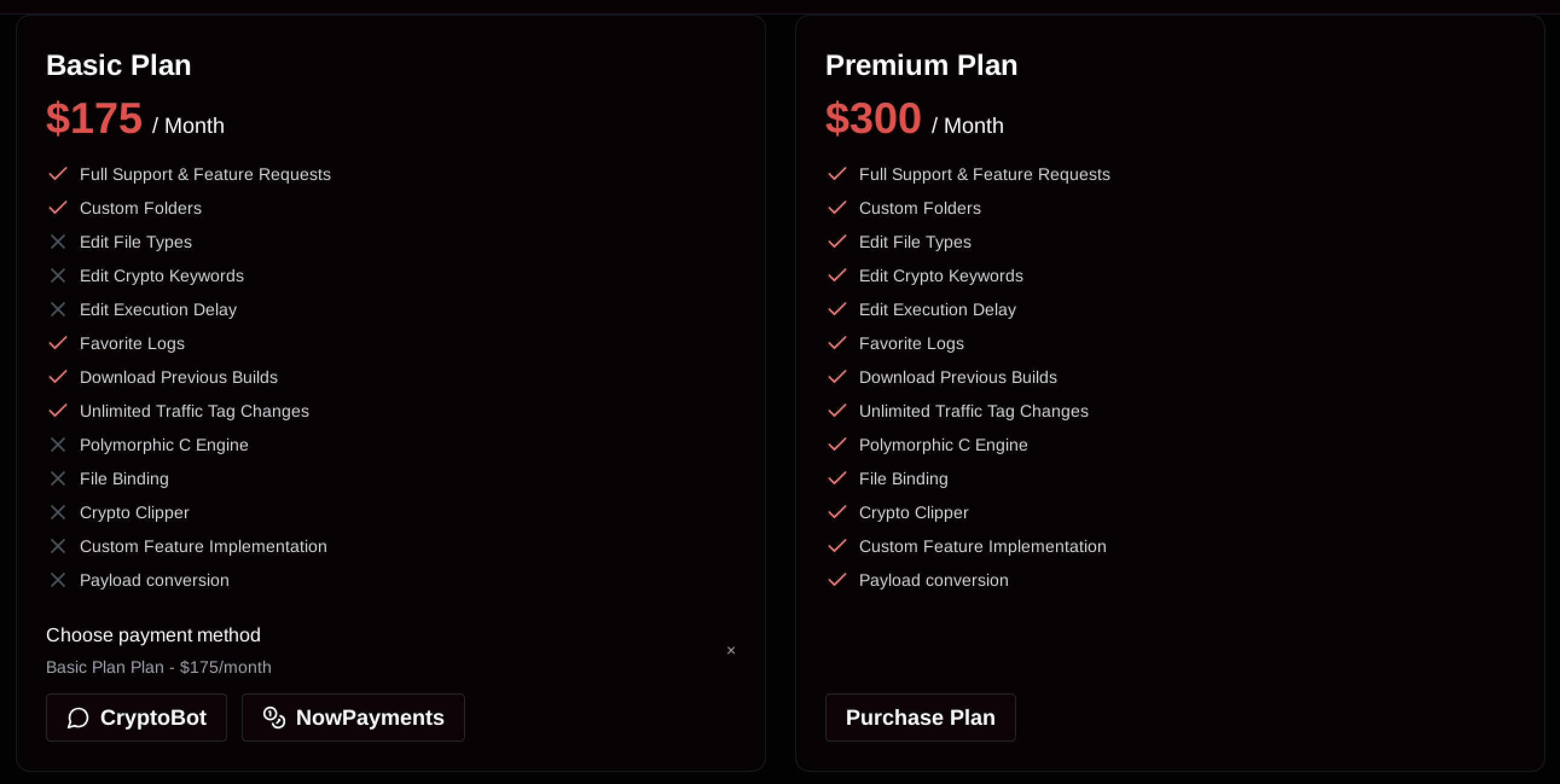
The operators advertise ambitious capabilities including anti-analysis techniques, antivirus bypasses, and deployment capabilities in government agencies and corporate networks.
The malware is promoted on both Telegram and the Russian-speaking Lolz hacker forum, with indicators suggesting Russian citizenship of the operators based on the use of Soviet Union country code domains and CIS targeting options.
Despite the bold claims made by SantaStealer’s operators, Rapid7’s analysis reveals significant operational security failures.
The leaked samples contain unobfuscated code with complete symbol names and unencrypted strings, making them far from undetectable and relatively straightforward to analyze.
The premature leak of these development builds with such clear indicators suggests poor operational security that may significantly undermine the malware’s effectiveness.
To protect against SantaStealer infections, users should exercise caution with unrecognized links and email attachments, avoid fake human verification prompts or technical support instructions requesting command execution, and refrain from running unverified code from sources such as pirated software, videogame cheats, or unverified plugins and extensions.
Organizations should ensure endpoint detection systems are updated to recognize the current indicators of compromise associated with this emerging threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
