Cybersecurity researchers unveiled a sophisticated scam operation, “Savvy Seahorse,” exploiting victims through advanced DNS manipulation techniques.
This operation, active since at least August 2021, has flown under the radar by leveraging DNS canonical name (CNAME) records to create a dynamic and elusive traffic distribution system (TDS) for financial scam campaigns.
A Novel Approach to Cybercrime
Savvy Seahorse’s campaigns are not your typical phishing attempts. They incorporate fake ChatGPT and WhatsApp bots that provide automated responses, luring victims into providing personal information under the guise of high-return investment opportunities.
These campaigns target a wide range of language speakers, including Russian, Polish, Italian, German, Czech, Turkish, French, Spanish, and English, while excluding potential victims in Ukraine and a few other countries.
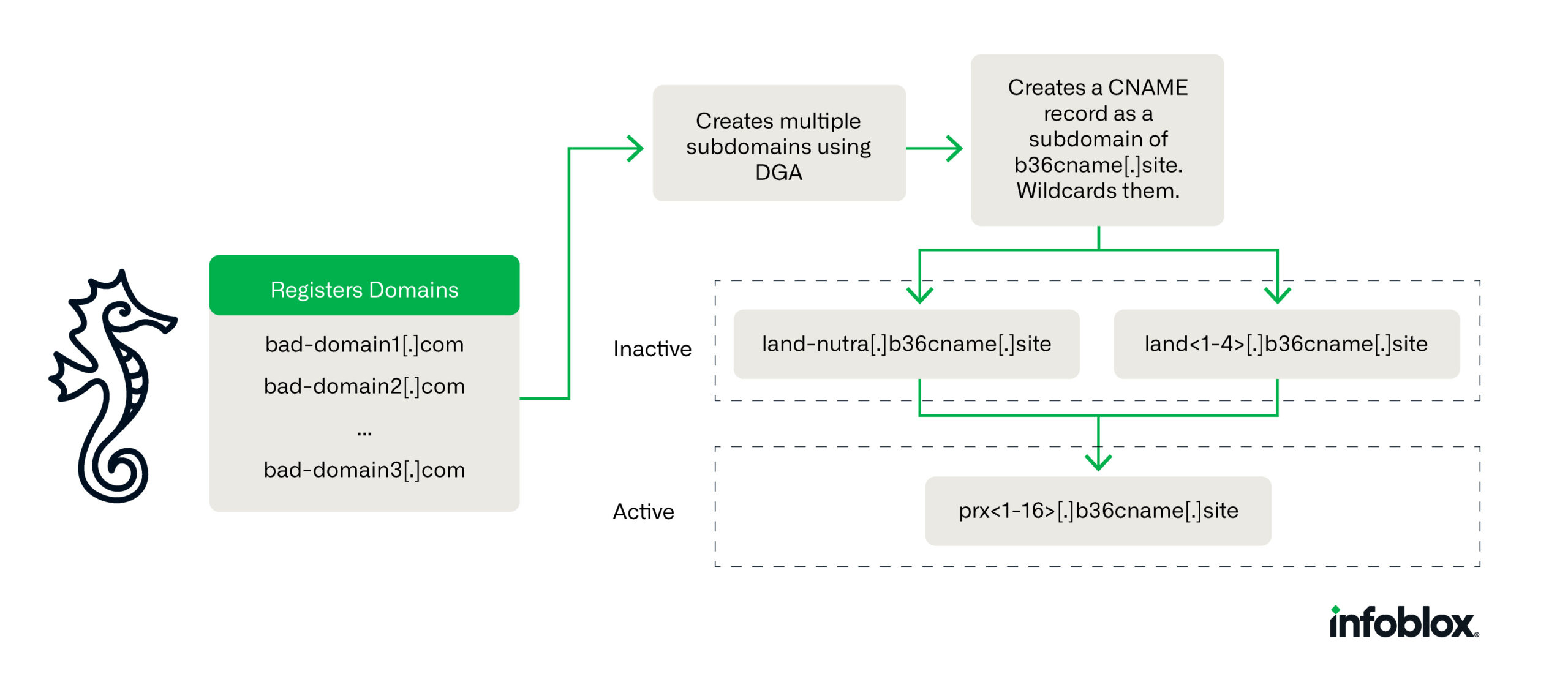
The crux of Savvy Seahorse’s strategy lies in abusing the Domain Name System (DNS).
By leveraging CNAME records, the threat actor has developed a sophisticated TDS that allows for dynamic content delivery and IP address updates, making their malicious campaigns challenging to detect and shut down, infoblox researchers said.
This technique has enabled Savvy Seahorse to evade detection by the security industry, marking the first reported use of CNAMEs for such malicious purposes.
Sophisticated Scam Operations
Savvy Seahorse’s operations are meticulously planned and executed. The campaigns are primarily delivered through Facebook advertisements, enticing victims to fake investment platforms.
Once there, victims are tricked into funding their accounts with the promise of substantial returns.
The use of dedicated hosting and regular IP address changes, coupled with short-lived individual campaigns, makes tracking and combating these operations a formidable challenge.
The operation’s infrastructure is vast, with approximately 4.2k base domains linked through a single CNAME record to a subdomain of b36cname[.]site.
This setup allows Savvy Seahorse to quickly create independent campaigns, complicating passive DNS (pDNS) analysis and evading detection efforts, reads infoblox report.
The Role of CNAME in Cybersecurity
Using CNAME records for malicious purposes highlights a significant oversight in the cybersecurity industry’s understanding of DNS’s role in cybercrime.
CNAME records, which map one domain name to another, are a fundamental part of DNS that can be exploited to manage a large, shifting group of malicious domains efficiently.
This technique allows Savvy Seahorse to scale and move operations rapidly, presenting a moving target for cybersecurity defenses.
Implications and Defense Strategies
The discovery of Savvy Seahorse’s operations underscores the need for the cybersecurity community to reassess the role of DNS in cybercrime.
By understanding the tactics, techniques, and procedures employed by threat actors like Savvy Seahorse, cybersecurity professionals can develop more effective strategies to detect and disrupt such operations.
Blocking the base domain to which the CNAME records point could be a straightforward yet practical approach to mitigating the threat posed by this and similar operations.
In conclusion, the Savvy Seahorse campaign represents a significant evolution in cybercriminal tactics, leveraging DNS in ways previously unrecognized by the security industry.
As cybersecurity professionals work to counter these sophisticated threats, the importance of continuous research and adaptation in cybersecurity strategies has never been more evident.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
