Scripted Sparrow, a prolific Business Email Compromise (BEC) collective with members spanning three continents, has raised significant concerns among cybersecurity researchers due to the sophisticated automation infrastructure underlying their large-scale fraudulent operations.
Recent analysis by Fortra’s Intelligence and Research Experts (FIRE) reveals that the group’s staggering operational scale estimated at 3 million highly targeted messages monthly is only achievable through robust automation systems for both message generation and distribution.
The group’s modus operandi centers on impersonating executive coaching and leadership training consultancies.
Attack messages target members of victim organizations’ Accounts Payable teams and typically include spoofed reply chains between fictional consultancies and company executives, along with two PDF attachments: fraudulent invoices requesting amounts just under $50,000 and completed W-9 forms.
What distinguishes Scripted Sparrow from conventional BEC operators is its systematic approach to scaling these campaigns through automated processes.
Evolution of Automation Tactics
Scripted Sparrow’s automation strategy has evolved considerably since their first observed activity in June 2024.
Early versions of their campaigns employed generic language such as “Dear Customer” rather than personalized executive names.
The group has progressively refined their automated systems to generate more convincing messages with complex, multi-message spoofed reply chains that appear natural and contextually appropriate.
An exceptionally sophisticated development emerged in their recent tactics: the group now intentionally omits promised PDF attachments from initial messages.
This calculated approach forces potential victims to respond requesting the missing documents, effectively filtering for susceptible targets before exposing their operational email accounts.
This two-stage process demonstrates refined automation logic that prioritizes victim vetting over raw message volume.
The scope of Scripted Sparrow’s operations underscores their reliance on automation infrastructure.
Fortra researchers identified 496 unique engagements through their Suspicious Email Analysis service.
However, by extrapolating from a single registered domain (kornferry.ws) that generated activity across 23 organizations targeting 70 users, researchers conservatively estimate that for each message captured, Scripted Sparrow sends approximately 70,000 messages.
The September 2025 activity peak, representing 94 engagements, likely corresponded to roughly 6.6 million targeted messages.
To sustain this operational pace, Scripted Sparrow leverages a diverse infrastructure combining free webmail addresses, newly registered domains, and compromised legitimate organizational mailboxes.
A threat actor who switched IP addresses on their device on November 4th at 1:50pm UTC and managed to change their GPS location from the San Francisco Bay Area to a Toronto suburb in less than 5 seconds.
Researchers anticipate the group will eventually incorporate generative AI technologies to enhance message personalization and authenticity further, potentially making their automated attacks even more convincing to target recipients.
Geographical Distribution and OpSec
Active defense engagements revealed that Scripted Sparrow members operate across Nigeria, South Africa, Türkiye, Canada, and the United States.
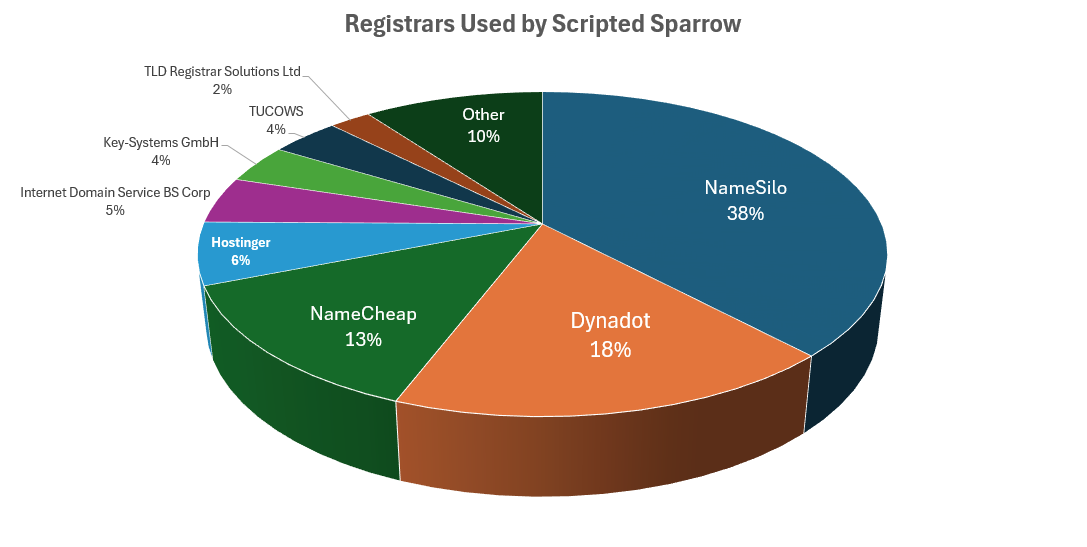
The group overwhelmingly favors NameSilo and Dynadot registrars for domain procurement. Analysis of 734 PDF attachments revealed that approximately 76 percent were generated using Skia, suggesting the use of standardized, automated PDF generation tools.
Notably, the collective employs multiple operational security measures including VPN usage, location spoofing via browser plugins, and Remote Desktop Protocol implementations.
Evidence of Telegram usage for internal group communication further indicates organized coordination systems.
As Scripted Sparrow continues expanding internationally evidenced by their first observed non-English message in Swedish requesting €9,905 the group shows no signs of slowing operations.
Organizations must implement rigorous payment approval protocols and verify all expenses through official communication channels rather than relying on email reply chains, as these remain trivially spoofable regardless of sophistication level.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
