I am looking for a way to reach more people and help them improve their security. Hopefully the cheat sheets I’m about to create are useful and will be shared outside the information security bubble.
The idea of the cheat sheets is that they are concise and give people actionable steps to improve their security. But I’m well aware that the limited info on the cheat sheets might not be detailed enough.
That’s why each sheet has a QR code that links to an accompanying blog.
So if you came here after scanning the QR code on the below sheet cheat, I hope this blog helps to learn more about secure account creation.
Regardless how you landed on this page, I hope you find this cheat sheet useful for yourself or to share with others.
You can find the latest version of this and future cheat sheets on this page.
Ok, let’s take a closer look at the different steps now.
Use unique, random and long passwords
Secure password management means your passwords must be strong.
Strong means random, sufficiently long and unique for every account. For more detail about how random passwords look and what sufficiently long means and how you can create such passwords read this post.
Store them in a password manager or a password book
In that same post you can also read how a password manager can help you to generate and store strong passwords in a secure way. Or if a password manager is not suitable for you a password book might be the way to go to store your passwords securely.
Enable multi-factor authentication
If you protect an account with a password only, miscreants can gain access to your account when they get hold of your password. That’s where multi-factor authentication can help and pose an extra barrier for attackers that know or guess your password.
If you don’t know what multi-factor authentication is and how to get started, no worries. I wrote a blog that explains it in a very simple way. Make sure to also read the follow up blog to understand the subtleties of enabling multi-factor authentication such that you don’t lose access to your accounts.
Leave optional fields empty
At account registration you get often asked for a lot of personal information. All the data you provide end up somewhere on a server. Unfortunately websites and their underlying servers and databases get hacked and the customer data gets stolen. The less data you provide the less data that can get stolen, so leave optional fields empty.
Enter fake data in mandatory fields whenever possible
Some websites ask for personal data that they actually don’t need in order to provide the service they offer. Typical examples are date of birth, your physical address or phone number. So enter fake data in mandatory fields whenever the data doesn’t have to be correct. Of course when you’re using an online shopping site, you need to specify an actual address where they can deliver the purchased goods, but they don’t need to know your date of birth to deliver the package.

Give fake answers to security questions, treat them like passwords
You probably know the kind of security questions that you need to answer at account registration and are used for account recovery purposes. Questions like “What’s the name of the high school where you studied?”. The answer to this kind of questions is easily publicly retrievable, so being honest is no secure option here. If you want to know how to answer these questions securely, read this blog.
Restrict privacy settings after account creation
When you have followed the previous tips and created your account in a safe way don’t forget to check the privacy settings. Often by default a lot of data used by a website or app is accessible by or shared with third parties. By restricting the sharing to a strict minimum you minimize the risk of your data getting abused by or stolen from these third parties.
Some additional tips
Two additional tips that didn’t make the cheat sheet because one is a bit “advanced” and the other one could do more harm than good without the right nuance.
Using email aliases
Analysing a new breach and out of curiosity, looked at the prevalence of sub-addressing / plus-aliasing in email addresses. 0.008% of accounts use it, and this is a more techie audience. People that use it love it, but it’s extraordinarily rare. More: https://t.co/9yRMLLTb3N
— Troy Hunt (@troyhunt) October 6, 2021
Most popular email providers foresee a way to create email aliases by using the ‘+’ sign. But how does that work and why would you use it?
Let’s say Alice want to register a Twitter account with her gmail address. Instead of using [email protected] she uses [email protected] Gmail (and a lot of other email providers) ignore everything behind the ‘+’ and mails directed at [email protected] will still arrive in Alice’s [email protected] mailbox.
But why would Alice bother to use this alias?
First of all there’s a small security benefit. A lot of attacks against passwords are successful because people use the same email address (and unfortunately also the same password). This particular type of attacks wouldn’t be trivial anymore when using specific aliases for every account.
Another small benefit is that Alice can detect when companies share her data without consent. For instance when she gets unsolicited mail on a particular alias or when she learns a specific alias is compromised in a data breach of a site for which she didn’t register with that specific alias.
If you find this too hard, no worries. It’s a trick with relative small security benefits. If you apply the other tips you’re doing a great job already!
Use of public mailboxes
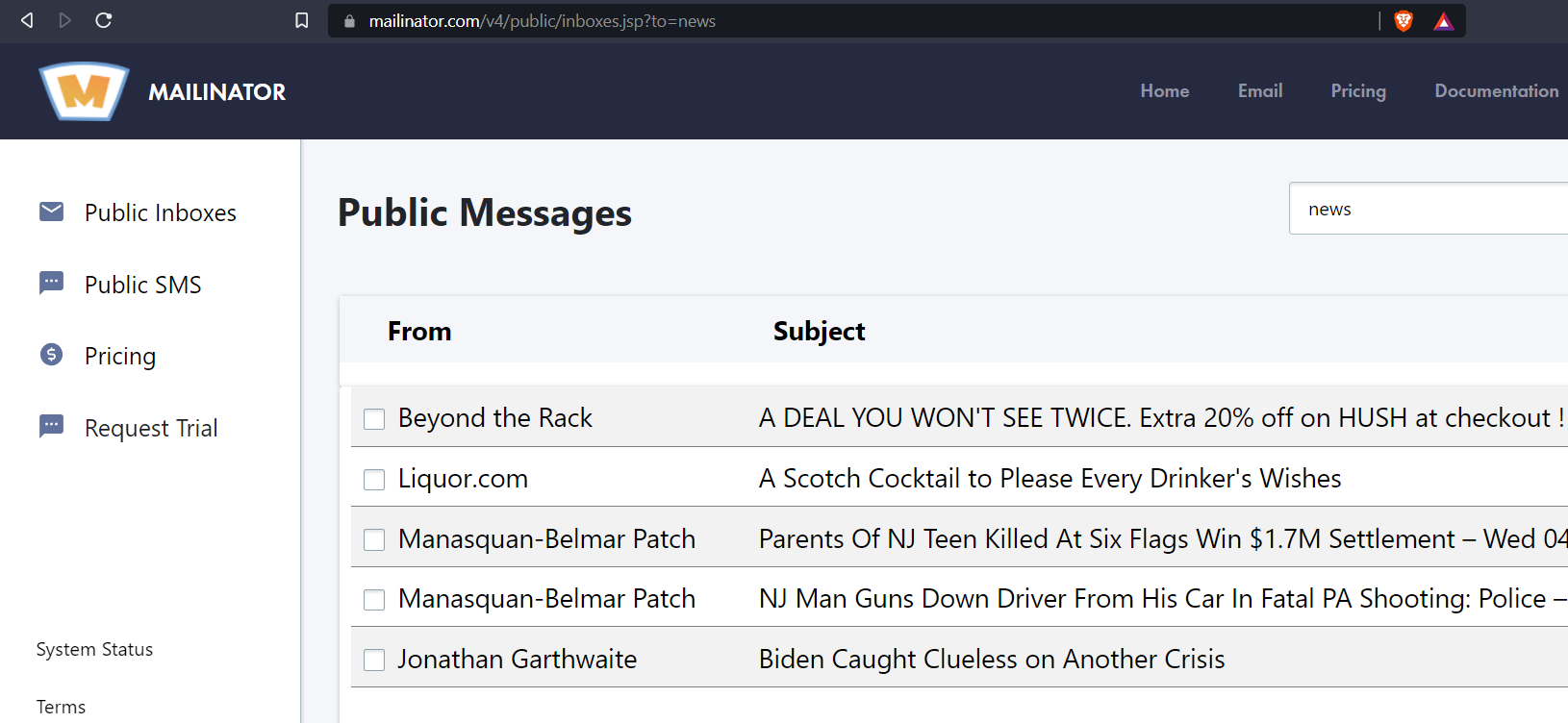
Public mailboxes like Mailinator can be handy in certain cases. For instance if you want to read a news article but you need to create an account first you could use such a public mailbox.
In this case the account is only necessary to bypass the barrier to read the article and the news site doesn’t need any of your personal data to be able to show you the article.
You can just come up with a name, let’s say [email protected] and use that for account registration.
IMPORTANT: only use a public mailbox at account registration when you can enter fake data on all mandatory fields. Everyone that wants can access the [email protected] mailbox and will have access to your account registration emails and thus indirectly to all information provided at account registration.
There’s more to come
If you’re interested in these cheat sheets or my other articles, you can subscribe to my blog and you’ll be notified when I publish them. Or you can follow me on Twitter.
Feel free to share these cheat sheets with your co-workers, family or friends. I would like to hear back from you if you used the cheat sheet or shared it and whether it was any helpful. Other feedback also welcome of course!