Serbian authorities have reportedly used an Android zero-day exploit chain developed by Cellebrite to unlock the device of a student activist in the country and attempt to install spyware.
Cellebrite is an Israeli digital forensics company that develops tools used by law enforcement, intelligence agencies, and private companies to extract data from smartphones and other digital devices.
Companies like Cellebrite commonly utilize zero-day exploits to access and extract data usually protected on locked phones.
The use of this Android exploit was found by Amnesty International’s Security Lab in mid-2024 during forensic research on the logs of the impacted device.
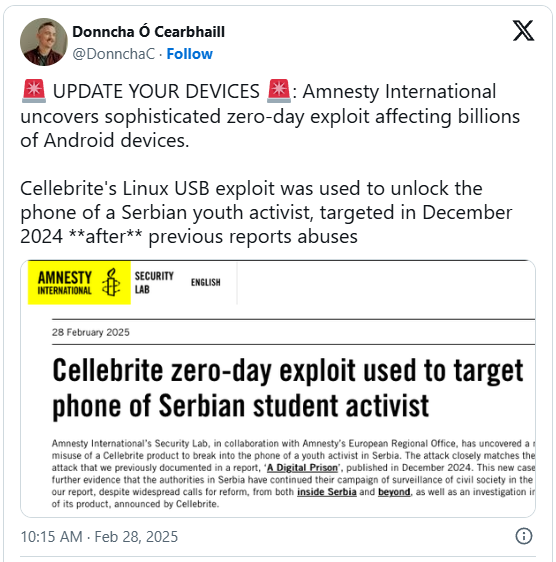
The organization previously reported on cases of privacy rights abuse in Serbia in December 2024. In response to the revelations, Cellebrite announced it blocked access to its tools for the country’s security services (BIA) earlier this week.
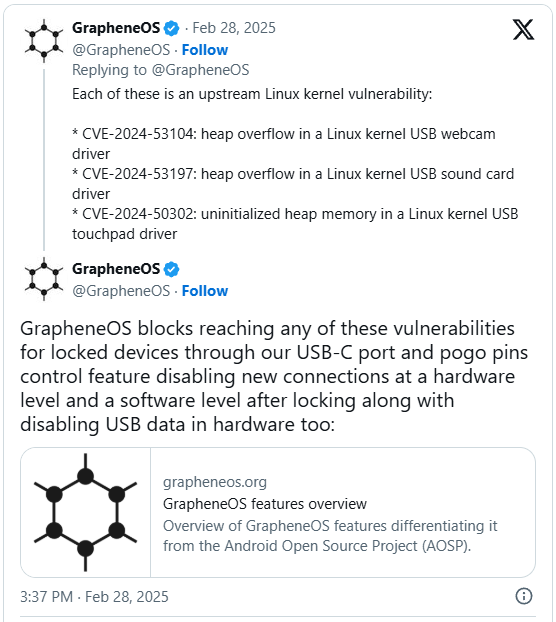
After Amnesty shared its findings with Google’s Threat Analysis Group (TAG), Google’s researchers were able to pinpoint three vulnerabilities in the Linux kernel USB drivers, also used in Android, that were exploited as zero-days.
The three flaws are:
- CVE-2024-53104 (USB Video Class exploit)
- CVE-2024-53197 (ALSA USB-sound driver exploit)
- CVE-2024-50302 (USB HID device exploit)
The first flaw was patched in Google’s February 2025 Android security updates, marked as “under limited, targeted exploitation.”
The other two flaws have not been announced as fixed in any Android security update bulletins yet, and depending on the device model and how often manufacturers update its kernel, it might take a while.
Head of Security Lab at Amnesty, Donncha O’Cearbhaill, told BleepingComputer that patching CVE-2024-53104 might be enough to disrupt the whole exploitation chain, although they cannot be certain about it yet.
GrapheneOS told BleepingComputer that their Android distribution already has patches for CVE-2024-53197 and CVE-2024-50302 because they regularly update the latest Linux kernel.
BleepingComputer asked Google when fixes for the two flaws would become available to all Android users, but we are still awaiting a response.
USB drivers under fire
USB exploits commonly take advantage of vulnerabilities in a device’s USB system, such as the drivers, firmware, or kernel components, to gain unauthorized access or control over the system.
The exploit may achieve memory corruption for arbitrary code execution, inject malicious commands, or bypass lock screens.
One mitigating factor is that they require physical access to the target device. In this case, and many other similar cases, this requirement was easily fulfilled by the police detaining the person and confiscating their device.
In April 2024, Google fixed two zero-day flaws (CVE-2024-29745 and CVE-2024-29748) forensic firms exploited to unlock phones without a PIN, implementing memory zeroing before USB is enabled.
Earlier this month, Apple fixed a zero day (CVE-2025-24200) Cellebrite and GrayKey leveraged for bypassing USB Restricted Mode to extract data from iPhones.
Stock Android does not have a direct equivalent to Apple’s USB Restricted Mode. However, users can still mitigate the threat by turning off USB debugging (ADB), setting the cable connectivity mode to “Charge Only,” and enabling Full Disk Encryption (Settings → Security & privacy → More security & privacy → Encryption & credentials → Encrypt phone).
