SetupHijack, an open-source research utility, has emerged as a powerful method for red teaming and security research by targeting race conditions and insecure file handling within Windows installer and update mechanisms.
By polling world-writable directories such as %TEMP%, %APPDATA%, and %USERPROFILE%Downloads, the tool intercepts installer‐dropped payloads before they execute with elevated privileges, enabling full SYSTEM or Administrator compromise without requiring elevated permissions to run.
SetupHijack continuously scans specified directories for new or modified installer files with extensions .exe, .msi, and .bat. When a target file appears, the tool atomically replaces it with a user-supplied payload, optionally preserving the original file as a .bak backup.
If the privileged process executes the substituted payload before performing integrity checks, the attacker’s code runs under elevated rights.
Unlike file system notification-based methods, SetupHijack relies on high-frequency polling to minimize race-window durations.
SetupHijack Exploits Race Conditions
Hacker House stated that the framework also subverts Authenticode code-signing and installer trust models by integrating a hacked signing process using SignToolEx.exe and SignToolExHook.dll, allowing payloads to bear valid certificates and Authenticode timestamps.
This approach increases the probability of bypassing digital signature verifications employed by many installers and OS protections.
Building the tool is straightforward with Microsoft’s build utilities:

The default execution scans common drop locations, SetupHijack.exe. Flags allow fine-tuning of scan targets:
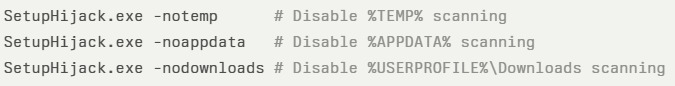
Additional modes include:
- clean: Restores .bak backups across enabled directories.
- verbose: Logs all actions, including successful payload substitutions.
For remote escalation on multi-user systems, SetupHijack can run alongside tools like shadow.exe under a compromised user account, standing by until an administrative installer process is launched.
In practice, security researchers have observed successful infections of popular applications such as Zoom (version 6.6.1), where the update binary residing in %AppData% was hijacked to inject a custom implant.
During demonstration runs, SetupHijack output logs show detailed infection events:
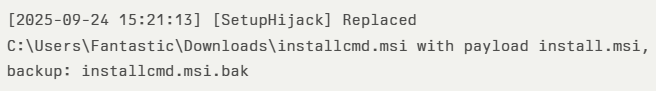
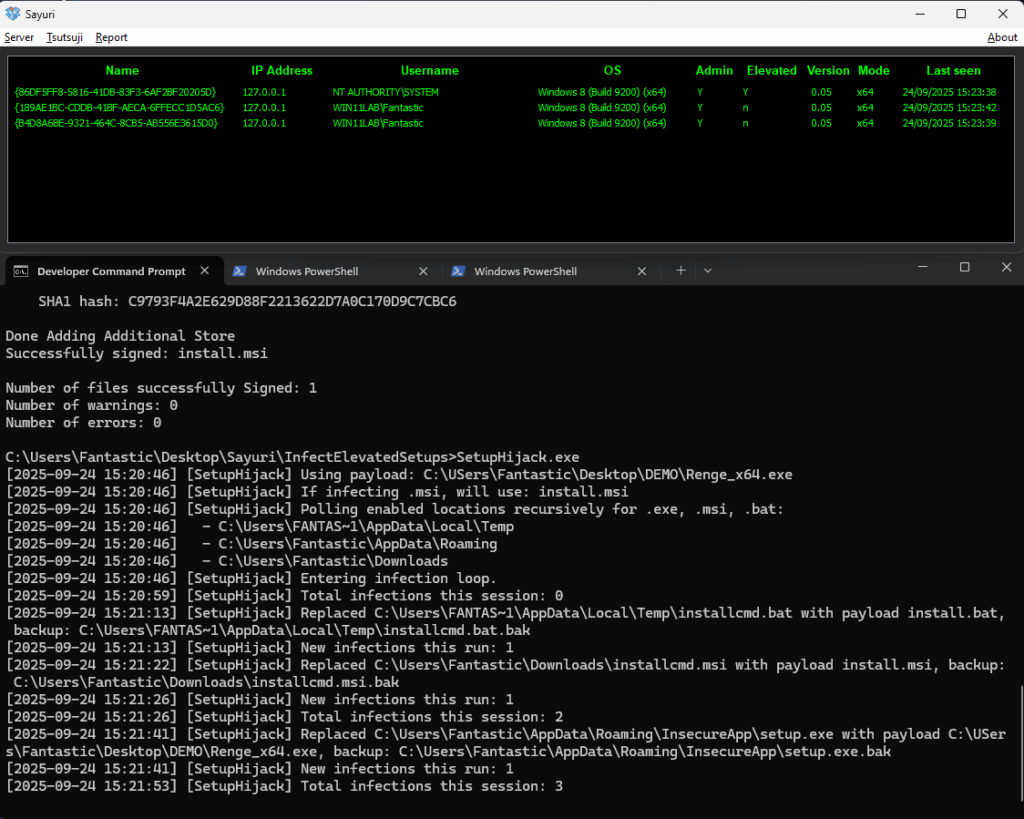
Security Implications
While SetupHijack is intended solely for authorized testing and research, it underscores a critical weakness in many Windows installer processes that trust files in world-writable directories.
Organizations should enforce stricter file-drop locations, implement robust integrity checks, and leverage secure coding practices to prevent time-of-creation/time-of-use (TOCTOU) attacks.
Additionally, signing installers with hardware-protected certificates and performing runtime signature validations can mitigate this class of exploitation.
As supply-chain and installer security become increasingly targeted, tools like SetupHijack serve as both a warning and an opportunity to harden deployment workflows against sophisticated race-condition exploits.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
