Every so often the sextortion emails that start with “Hello pervert” get a redesign.
You may have received one yourself: The emails claim that the sender has been watching your online behavior and caught you red-handed doing activities that you would like to keep private.
The email usually starts with “Hello pervert” and then goes on to claim that you have been watching porn. The sender often says they have footage of what you were watching and what you were doing while watching it.
To stop the sender from spreading the incriminating footage to your email contact list, you are asked to pay them money. The overall tone is threatening, manipulative, and designed to provoke fear and urgency.
We know these emails are a big problem. We see thousands of people visiting our website a week looking to find information on sextortion emails like these. And now we’re seeing a new version with some features we haven’t seen in the past. Interestingly, just as the cost of food, travel, and—well—living has gone up, so has the amount of money that the scammers ask for in the email.
This most recent email we’ve seen also gives away the probable origin of the emails.
With all that we thought it would be interesting to take a closer look.
“Hello pervert, I’ve sent thіs message from your Microsoft account.
I want to іnform you about a very bad sіtuatіon for you. However, you can benefіt from іt, іf you wіll act wіsely.
Have you heard of Pegasus? Thіs іs a spyware program that іnstalls on computers and smartphones and allows hackers to monіtor the actіvіty of devіce owners. It provіdes access to your webcam, messengers, emaіls, call records, etc. It works well on Androіd, іOS, macOS and Wіndows. I guess, you already fіgured out where I’m gettіng at.
It’s been a few months sіnce I іnstalled іt on all your devісes because you were not quіte choosy about what lіnks to clіck on the іnternet. Durіng thіs perіod, I’ve learned about all aspects of your prіvate lіfe, but one іs of specіal sіgnіfіcance to me.
I’ve recorded many vіdeos of you jerkіng off to hіghly controversіal рorn vіdeos. Gіven that the “questіonable” genre іs almost always the same, I can conclude that you have sіck рerversіon.
I doubt you’d want your frіends, famіly and co-workers to know about іt. However, I can do іt іn a few clіcks.
Every number іn your contact Iіst wіll suddenly receіve these vіdeos – on WhatsApp, on Telegram, on Instagram, on Facebook, on emaіl – everywhere. It іs goіng to be a tsunamі that wіll sweep away everythіng іn іts path, and fіrst of all, your former lіfe.
Don’t thіnk of yourself as an іnnocent vіctіm. No one knows where your рerversіon mіght lead іn the future, so consіder thіs a kіnd of deserved рunіshment to stop you.
I’m some kіnd of God who sees everythіng. However, don’t panіc. As we know, God іs mercіful and forgіvіng, and so do I. But my merсy іs not free.
Transfer 1650$ to my Lіtecoіn (LTC) wallet: {redacted}
Once I receіve confіrmatіon of the transactіon, I wіll рermanently delete all vіdeos compromіsіng you, unіnstall Pegasus from all of your devіces, and dіsappear from your lіfe. You can be sure – my benefіt іs only money. Otherwіse, I wouldn’t be wrіtіng to you, but destroy your lіfe wіthout a word іn a second.
I’ll be notіfіed when you open my emaіl, and from that moment you have exactly 48 hours to send the money. If cryptocurrencіes are unchartered waters for you, don’t worry, іt’s very sіmple. Just google “crypto exchange” or “buy Litecoin” and then іt wіll be no harder than buyіng some useless stuff on Amazon.
I strongly warn you agaіnst the followіng:
* Do not reply to thіs emaіl. I’ve sent іt from your Mіcrosoft account.* Do not contact the polіce. I have access to all your devісes, and as soon as I fіnd out you ran to the cops, vіdeos wіll be publіshed.
* Don’t try to reset or destroy your devісes. As I mentіoned above: I’m monіtorіng all your actіvіty, so you eіther agree to my terms or the vіdeos are рublіshed.
Also, don’t forget that cryptocurrencіes are anonymous, so іt’s іmpossіble to іdentіfy me usіng the provіded address.
Good luck, my perverted frіend. I hope thіs іs the last tіme we hear from each other.
And some frіendly advіce: from now on, don’t be so careless about your onlіne securіty.”
Spoofing your email address
One clever trick the scammers use is saying they’ve sent the email from your Microsoft account. The sender spoofs your email address, in the hope that it makes you think your device may indeed be compromised.
However, it’s easy for scammers to spoof (use a fake) email address because the email system doesn’t check if the sender is real. That’s why it’s important to be cautious. Even if an email looks like it’s from someone you know, or even yourself, it could be from a scammer.
If you’re technically savvy, taking one look at the authentication results in the email header would reveal that the email failed because the IP address does not match the domain.
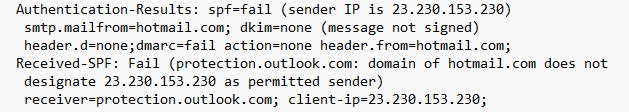
However, we can assume that most people receiving the email wouldn’t think to do this, and so the email spoofing might well work to add legitimacy to the email.
Encoding errors
Looking at the source of the email, we got a little insight into its origin.
The intro of the email shows the repeated use of “=D1=96” and some other encoding errors. In fact, the whole text is riddled with encoding errors, which typically appear when Cyrillic or other non-Latin characters are misinterpreted as UTF-8 or quoted-printable, or when text is generated or processed by automated systems not properly handling character sets.
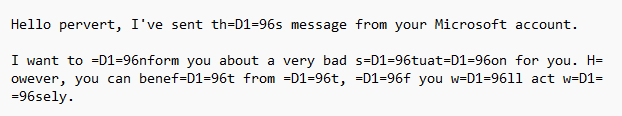
The sequence =D1=96 is the quoted-printable encoding for the Unicode character U+0456, which is the Cyrillic letter “i”. This encoding error strongly points towards the writer’s native language being one that uses the Cyrillic script, which is predominantly used in Eastern European and Central Asian countries, with Russian being the most prominent language using it.
These errors also tell us that this scammer doesn’t use the most sophisticated tools. Although the awkward sentence structures and repetitive language are consistent with automated text generation or translation, they are classic signs of a low-effort, high-volume campaign—not the kind where an AI has been used to add personalization or a more natural voice.
Price hike
Back in April, the price that scammers were asking victims to pay for being a “pervert” was $1200, and in May it was $1450.

This time we’re asked to pay no less than $1650.
There could be several reasons for this. Maybe the costs of the operation have gone up. Or the scammers feel the value of their threat and its consequences have increased.
Scammers often start with what seems a “reasonable amount” to them and, if successful, incrementally increase it for future victims. This allows them to gauge the maximum amount that people are willing to pay to avoid the threatened consequences.
I’m happy to report that both the mentioned Litecoin wallets are empty. Let’s keep it that way.
How to spot a sextortion email
Once you’re aware of them, it’s easy to recognize these emails. Remember that not all of the below characteristics might be included in the email you receive, but all of them are red flags in their own right.
- They often look as if they were sent from your own email address.
- The scammer accuses you of inappropriate behavior and claims to have footage of that behavior.
- In the email the scammer claims to have used Pegasus or some Trojan to spy on you through your own computer.
- The scammer says they know your password and may even offer one as “proof”. This password is likely to have been stolen in a separate data breach and is unrelated to the sextortion email itself.
- You are urged to pay up quickly or the so-called footage will be spread to all your contacts. Often you’re only allowed one day to pay.
- The actual message often arrives as an image or a pdf attachment. Scammers do this to bypass phishing filters.
How to react to sextortion emails
First and foremost, never reply to emails of this kind. It may tell the sender that someone is reading the emails sent to that address and so they will repeatedly try other methods to defraud you.
- Don’t let yourself get rushed into action or decisions. Scammers rely on the fact that you will not take the time to think this through and subsequently make mistakes.
- Do not open unsolicited attachments. Especially when the sender’s address is suspicious or even your own.
- If the email includes a password, make sure you are not using it anymore and if you are, change it as soon as possible.
- If you are having trouble organizing your passwords, have a look at a password manager.
- For your ease of mind, turn off your webcam or buy a webcam cover so you can cover it when you’re not using the webcam.
Sextortion emails often contain passwords that have been stolen in another data breach and posted online. If you want to find out what personal data of yours has been exposed online, you can use our free Digital Footprint scan. Fill in the email address you’re curious about (it’s best to submit the one you most frequently use) and you’ll get a free report.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
