ShadowSyndicate, a sophisticated cybercrime cluster first identified in 2023, has evolved its infrastructure management tactics by implementing a previously unreported server transition technique.
This method involves rotating SSH fingerprints across multiple servers to obscure operational continuity. However, operational security (OPSEC) errors have allowed researchers to trace these connections.
The threat actor orchestrates large server clusters using distinctive SSH keys, with each fingerprint creating identifiable patterns across dozens of command-and-control (C2) servers.
Unlike traditional infrastructure reuse, ShadowSyndicate transfers servers between different SSH clusters to mimic legitimate ownership changes.
The server transition technique works by rotating access credentials across infrastructure nodes. When executed properly, this creates plausible deniability between “old” and “new” server controllers.
Group-IB researchers confirmed two additional SSH fingerprints linked to ShadowSyndicate operations in February 2026.
However, overlapping SSH key presence on certain servers exposed the operational links, revealing at least 20 servers functioning as C2 infrastructure for attack frameworks, including Cobalt Strike, Metasploit, Havoc, Mythic, and Sliver.
Ransomware Connections
The analyzed infrastructure maintains connections to multiple ransomware operations with varying confidence levels. Confirmed associations include Cl0p/Truebot, ALPHV/BlackCat, Black Basta, Ryuk, and Malsmoke campaigns.
During RansomHub attacks investigated between September and October 2024, Darktrace identified data exfiltration to ShadowSyndicate-associated servers via SSH protocol, with the IP address 46.161.27[.]151 specifically linked to their C2 infrastructure.
Research indicates ShadowSyndicate likely operates either as an Initial Access Broker (IAB) or bulletproof hosting (BPH) provider.
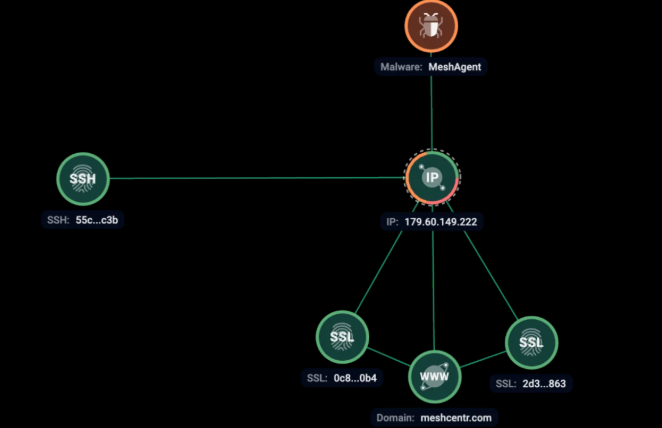
MeshAgent has been observed on 179.60.149[.]222 server at the same time with SSH fingerprint 55c658703c07d6344e325ea26cf96c3b.
Security analysts assess with moderate confidence that the group accesses a network of private European BPH providers exhibiting intelligence agency hosting characteristics, operated from Russia through offshore entities.
These providers disguise operations as VPN or proxy services using imbricated autonomous system numbers (ASNs) like AS209588 and AS209132.
Persistent Hosting Patterns
ShadowSyndicate demonstrates consistent preference for specific hosting providers across all discovered SSH fingerprint clusters.
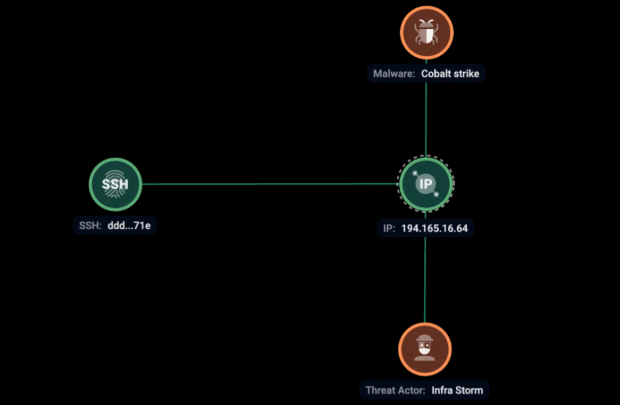
Cobalt Strike is a known commercial red-team framework with post-exploitation modules frequently used by legitimate red teams and widely abused by threat actors.
Their innovator-level sophistication, including zero-day exploitation capabilities and organization-scale resources, positions ShadowSyndicate as a hybrid infrastructure provider fueling multiple ransomware operations and potentially state-sponsored advanced persistent threats.
While servers originate from different territories and nominal owners, the repeated reliance on familiar ASNs creates predictable attribution patterns.
This consistency suggests operational comfort with particular providers and enables proactive detection through infrastructure correlation.
The threat actor’s infrastructure remains active as of February 2026, continuing to scan for vulnerabilities and deploy payloads.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
