The Shai-Hulud 2.0 supply chain attack has proven to be one of the most persistent and destructive malware campaigns targeting the developer ecosystem.
Since the incident first emerged on November 24, 2025, Wiz Research and Wiz CIRT have been tracking the active spread, which continues to evolve, even as infection rates have slowed to a more manageable but still concerning pace.
The attack’s scope is staggering. Across the corpus of compromised repositories, Wiz researchers recovered approximately 24,000 unique environment.json files containing critical system and credential information.
The malware successfully compromised more than 30,000 total repositories, with roughly 70 percent containing distinct contents representing individual victim environments.
Among the most damaging artifacts discovered were over 500 GitHub usernames and tokens exfiltrated from contents.json files.
As a result, our response paired the GitHub API with GHArchive, leaving us with one of the most comprehensive data sets on this incident.
Credentials represent direct access points for further attacks and demonstrate the worm’s sophisticated capability to harvest authentication materials across multiple GitHub accounts and organizations.
Shai-Hulud 2.0 Cyberattack
What distinguishes Shai-Hulud 2.0 from previous supply chain worms like s1ngularity and Shai-Hulud 1.0 is its remarkable persistence. Six days after initial detection, new repositories continued to be created at a reduced but steady rate.
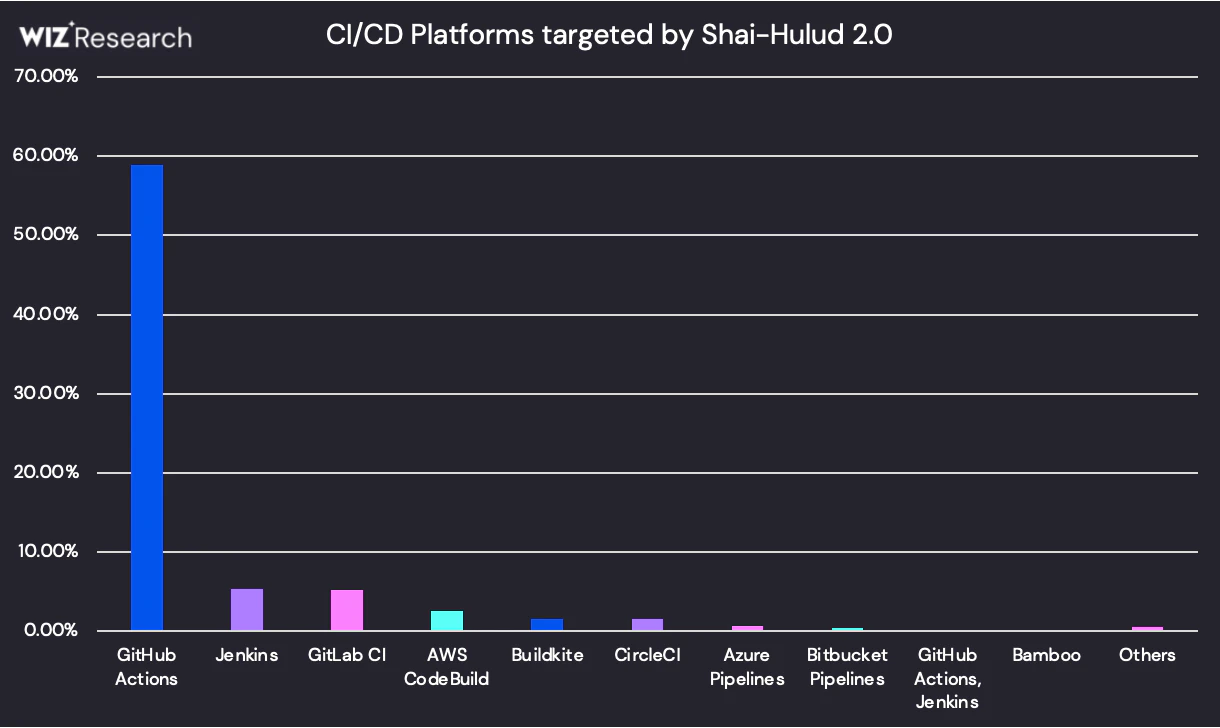
Specifically on CI/CD runners, GitHub Actions is the leading platform with Jenkins, GitLab CI, and AWS CodeBuild coming distant second, third, and fourth.
A significant resurgence occurred on December 1, 2025, when researchers observed over 200 new infected repositories in just 12 hours, suggesting the attack may experience renewed waves of activity.
The malware’s infection methodology reveals strategic sophistication. When unable to locate GitHub credentials locally, the worm searches for previously compromised accounts and uses stolen credentials to upload repositories containing data from new victims.
This cross-victim exfiltration approach creates a cascading compromise effect that complicates incident response and attribution.
While the attack primarily leveraged the npm ecosystem through malicious packages like @postman/tunnel-agent and @asyncapi/specs, the compromise extended to multiple software delivery channels.
AsyncAPI disclosed that attackers exfiltrated not only npm tokens but also an OpenVSX API key, successfully infecting the AsyncAPI IDE extension and establishing footholds in the OpenVSX ecosystem.
The malware’s reach extended into the Java/Maven ecosystem through automated mirroring mechanisms.
Researchers identified the org.mvnpm:posthog-node:4.18.1 package as a vector, though active worm spread was not observed in Maven Central or OpenVSX at the time of analysis.
Leaked Credentials Pose Active Risk
The volume of stolen credentials represents an immediate threat vector for downstream attacks.
Analysis revealed that approximately 60 percent of leaked npm tokens remain valid, creating opportunities for attackers to launch additional supply chain campaigns.
While truffleSecrets.json files contained up to 400,000 unique secrets, the analysis indicates only about 2.5 percent were verified by the malware, with roughly 25 JWT tokens retaining validity.
More troubling is that the threat landscape continues to evolve. Companies have documented confirmed infections through compromised packages, and community response has highlighted persistent confusion about GitHub Actions security controls.
Wiz researchers predict continued attacks leveraging similar tactics and procedures, particularly given the vast credential trove already harvested.
The Shai-Hulud 2.0 incident underscores critical vulnerabilities in supply chain security practices.
Organizations must prioritize hardening GitHub Actions configurations, implementing comprehensive secret management strategies, and maintaining vigilant monitoring for compromised credentials.
The threat remains active, and the credential cache accumulated during this attack represents a persistent risk for months to come.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
