The activities of the Chinese threat actor group known as Sharp Dragon (formerly Sharp Panda) have been meticulously documented.
Since 2021, this group has been involved in highly targeted phishing campaigns, primarily focusing on Southeast Asia.
However, recent developments indicate a significant shift in their operations, with the group now targeting governmental organizations in Africa and the Caribbean.
Historical Context
Checkpoint Blog shows Sharp Dragon has a history of deploying various payloads, including VictoryDLL and the Soul framework, through sophisticated phishing emails.
Their modus operandi has remained consistent, with a focus on high-profile targets.
However, the group’s recent activities mark a notable expansion in their geographical focus.
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
Shift to Africa and the Caribbean
Starting in November 2023, Sharp Dragon began targeting governmental entities in Africa and the Caribbean.
This shift was facilitated by exploiting previously compromised entities in Southeast Asia.
The group used highly tailored lures related to intergovernmental relations to establish footholds in these new regions.
Cyber Activities in Africa
The first identified phishing attack targeting Africa was sent from a Southeast Asian country to an African country in November 2023.
The lure document, which appeared to be an authentic correspondence about industrial relations, was used to deploy the Cobalt Strike Beacon.
By January 2024, direct targeting within Africa was observed, indicating successful phishing attempts.

Cyber Activities in the Caribbean
Similarly, in December 2023, Sharp Dragon targeted a Caribbean country using a lure related to a Caribbean Commonwealth meeting.
By January 2024, compromised email infrastructure in the Caribbean was used to launch a large-scale phishing campaign targeting multiple regional governments.

Technical Analysis
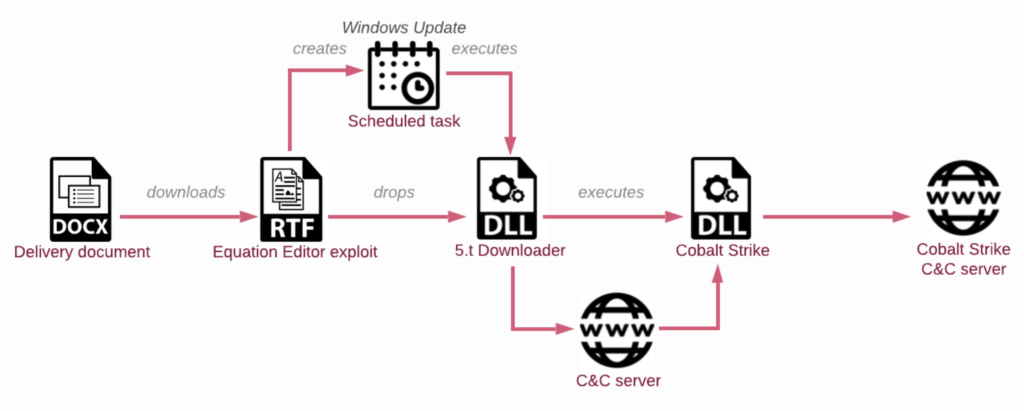
Sharp Dragon’s infection chain has evolved since May 2023, reflecting a more careful target selection and increased operational security (OPSEC) awareness.
The group’s 5.t downloader now conducts thorough reconnaissance on target systems, examining process lists and enumerating folders to select potential victims more discerningly.
Cobalt Strike Payload
Sharp Dragon’s primary payload is now Cobalt Strike Beacon, which provides backdoor functionalities such as C2 communication and command execution.
This shift to publicly available tools like Cobalt Strike indicates a refined approach to minimizing exposure.
{
"config_type": "static",
"spawnto_x64": "%windir%\sysnative\Locator.exe",
"spawnto_x86": "%windir%\syswow64\Locator.exe",
"uses_cookies": "True",
"bstagecleanup": "True",
"crypto_scheme": 0,
"proxy_behavior": "Use IE settings",
"server,get-uri": "103.146.78.152,/ajax/libs/json2/20160511/json_parse_state.js",
"http_get_header": [
"Const_header Accept: application/*, image/*, text/html",
"Const_header Accept-Language: es",
"Const_header Accept-Encoding: compress, br",
"Build Metadata",
"XOR mask w/ random key",
"Base64 URL-safe decode",
"Prepend JV6_IB4QESMW4TOIQLJRX69Q7LPGNXW594C5=",
"Build End",
"Header Cookie"
]
}
Sharp Dragon has also introduced EXE-based 5.t loader samples, deviating from the usual DLL-based loaders. This change underscores the dynamic nature of their evolving strategies.
The new infection chain involves executables disguised as documents, which write and execute the 5.t DLL loader, creating a scheduled task for persistence.
Compromised Infrastructure
Sharp Dragon has shifted from using dedicated servers to compromised servers as C&C servers.
During a campaign in May 2023, the group exploited the CVE-2023-0669 vulnerability in the GoAnywhere platform, allowing for pre-authentication command injection.
The data collected from affected machines was sent to addresses masquerading as belonging to the GoAnywhere service.
Sharp Dragon’s strategic shift towards Africa and the Caribbean suggests a broader effort by Chinese cyber actors to enhance their presence and influence in these regions.
This move, coupled with refined tactics and publicly available tools, highlights the evolving nature of Chinese threat actors.
The findings underscore the importance of robust cybersecurity measures to protect high-profile organizations from such sophisticated threats.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
