An extortion group has launched a new data leak site to publicly extort dozens of companies impacted by a wave of Salesforce breaches, leaking samples of data stolen in the attacks.
The threat actors responsible for these attacks claim to be part of the ShinyHunters, Scattered Spider, and Lapsus$ groups, collectively referring to themselves as “Scattered Lapsus$ Hunters.”
Today, they launched a new data leak site containing 39 companies impacted by the attacks. Each entry includes samples of data allegedly stolen from victims’ Salesforce instances, and warns the victims to reach out to “prevent public disclosure” of their data before the October 10 deadline is reached.
The companies being extorted on the data leak site include well-known brands and organizations, including FedEx, Disney/Hulu, Home Depot, Marriott, Google, Cisco, Toyota, Gap, McDonald’s, Walgreens, Instacart, Cartier, Adidas, Sake Fifth Avenue, Air France & KLM, Transunion, HBO MAX, UPS, Chanel, and IKEA.
“All of them have been contacted long ago, they saw the email because I saw them download the samples multiple times. Most of them chose to not disclose and ignore,” ShinyHunters told BleepingComputer.
“We highly advise you proceed into the right decision, your organisation can prevent the release of this data, regain control over the situation and all operations remain stable as always. We highly recommend a decision-maker to get involved as we are presenting a clear and mutually beneficial opportunity to resolve this matter,” they warned on the leak site.
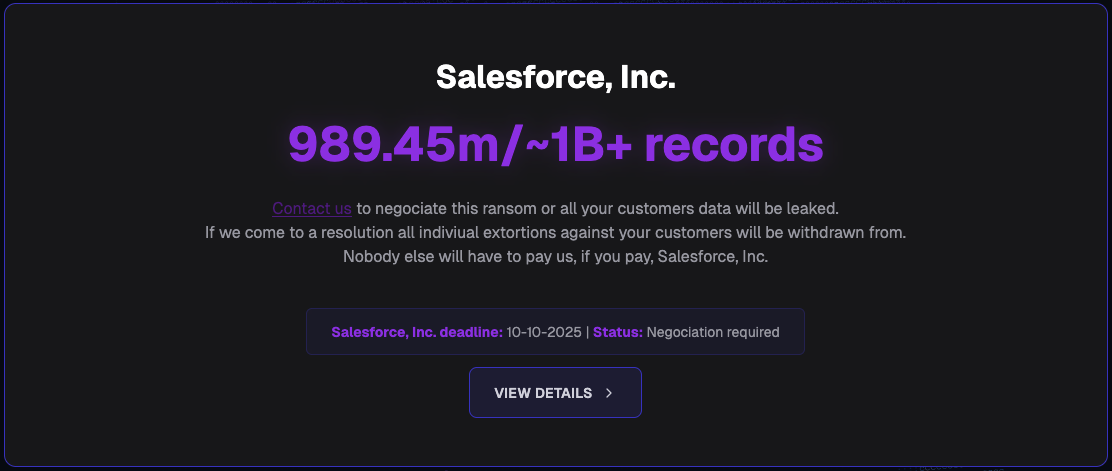
The threat actors also added a separate entry requesting that Salesforce pay a ransom to prevent all impacted customers’ data (approximately 1 billion records containing personal information) from being leaked.
“Should you comply, we will withdraw from any active or pending negotiation indiviually from your customers. Your customers will not be attacked again nor will they face a ransom from us again, should you pay,” they added.
The extortion group also threatened the company, stating that it would help law firms pursue civil and commercial lawsuits against Salesforce following the data breaches and warned that the company had also failed to protect customers’ data as required by the European General Data Protection Regulation (GDPR).
Scattered Lapsus$ Hunters have been targeting Salesforce customers with voice phishing attacks since the beginning of the year, leading to breaches that have impacted companies such as Google, Cisco, Qantas, Adidas, Allianz Life, Farmers Insurance, Workday, as well as LVMH subsidiaries, including Dior, Louis Vuitton, and Tiffany & Co.
In these attacks, the threat actors tricked employees into linking a malicious OAuth app to their company’s Salesforce instance. Once connected, the attackers stole company databases and used the data to extort victims via email.
These extortion emails were signed by ShinyHunters, a notorious extortion group linked to a long string of high-profile breaches in recent years, including the Snowflake attacks and those against AT&T and PowerSchool.
ShinyHunters also claimed to have used stolen OAuth tokens for Salesloft’s Drift AI chat integration with Salesforce to steal sensitive information, including passwords, AWS access keys, and Snowflake tokens, from customers’ Salesforce instances.
These attacks were tracked by Mandiant under a separate threat cluster named “UNC6395” as they have been unable to formally link the breaches to this group.
On a Telegram channel associated with the extortion group, the threat actors claim that they will begin extorting companies affected by the Salesloft Drift attacks on a separate data leak site launching on October 10th.
ShinyHunters previously told BleepingComputer that the Salesloft data theft attacks impacted approximately 760 companies and resulted in the theft of 1.5 billion Salesforce records.
The Salesloft attacks are known to have impacted Google, Palo Alto Networks, CyberArk, Cloudflare, Rubrik, Elastic, BeyondTrust, Proofpoint, JFrog, Zscaler, Tenable, Nutanix, Qualys, Cato Networks, and many more.

Join the Breach and Attack Simulation Summit and experience the future of security validation. Hear from top experts and see how AI-powered BAS is transforming breach and attack simulation.
Don’t miss the event that will shape the future of your security strategy
