In recent cybersecurity news, the infamous SiegedSec hacker group has made headlines once more by announcing a fresh cyber assault on the Pemalang region of Indonesia.
The dark web hacker group, renowned for their audacious tactics, has claimed responsibility for the breach, boldly declaring their intent to expose two databases pilfered from the targeted region.
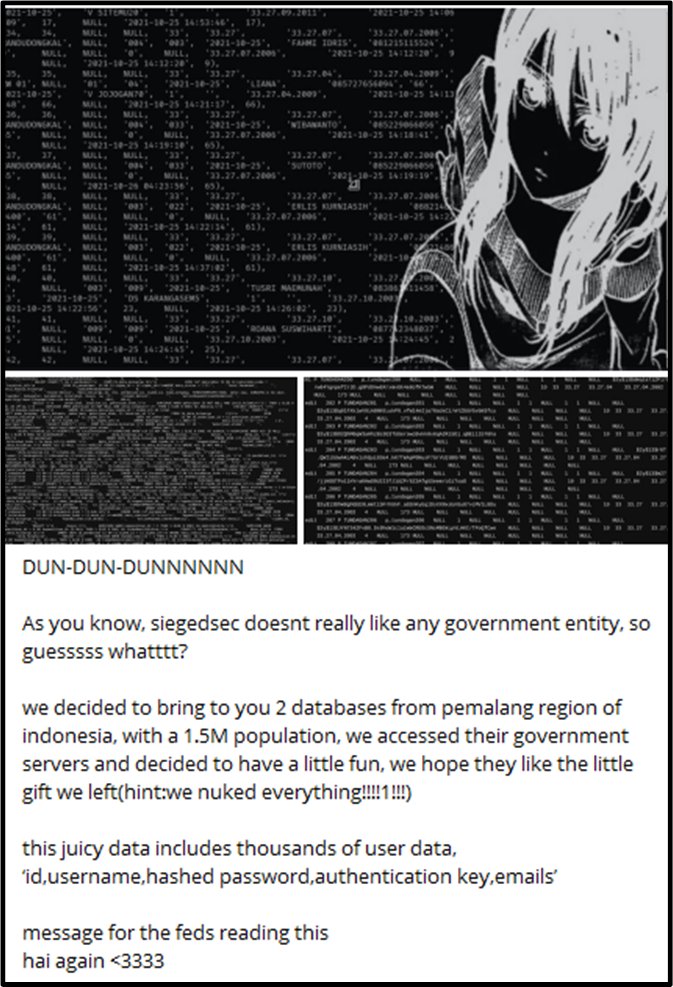
The message disseminated by the threat actor explains that they “doesn’t really like any government entity”, and the reason they have attacked the Pemalang region of Indonesia is the same.
In their post, the threat actor claims to have access to 2 databases from the region, and the alleged data includes “thousands of user data: ‘id, username, hashed password, authentication key, emails.’”
SiegedSec hacker group hacking spree
Apart from this alleged cyber attack on the Pemalang region of Indonesia, the threat actor has claimed many high-profile cyber attacks in the past.
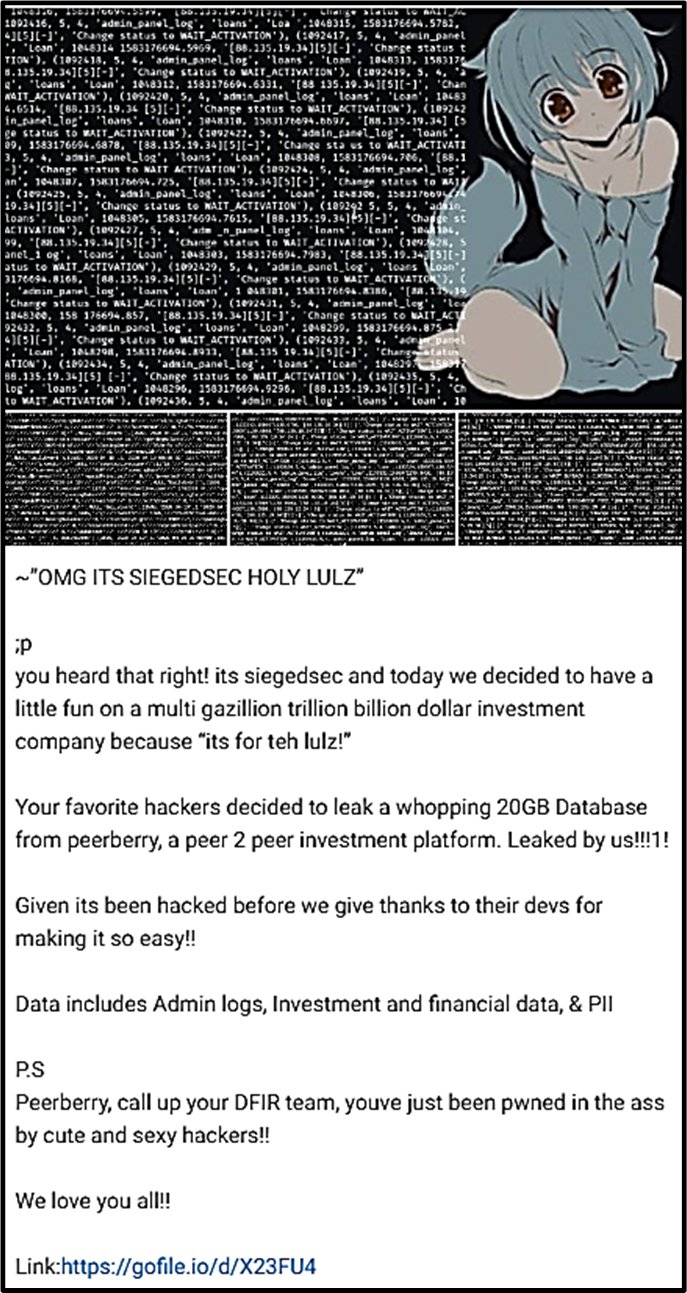
This comes hot on the heels of their previous assault on the esteemed investment platform PeerBerry. Renowned for their dark web exploits, SiegedSec revealed a massive cache of data totaling a staggering 20GB.
Within this extensive trove lie crucial records, including admin logs, personally identifiable information (PII), and sensitive financial and investment data. The breach was humorously disclosed on their dark web channel, provocatively titled “~ OMG ITS SIEGEDSEC HOLY LULZ.”
In a dark post declaration, the group cited “its for teh lulz!” as their motivation for targeting the multi-billion-dollar investment giant, PeerBerry.
They further taunted the platform, advising them to bolster their defenses while candidly expressing gratitude to the developers for what they perceived as a vulnerability.
Alongside their proclamation, the hackers provided a Gofile link, granting a glimpse into the compromised data.
However, the organization denied such claims and asserted that “cybercriminals are manipulating with an old incident.”
The dramatic emergence of the SiegedSec hacker group
In light of recent geopolitical events such as Russia’s invasion of Ukraine, a surge in new threat groups has emerged worldwide.
These groups exhibit a range of motives, from hacktivist activities aimed at disrupting operations to more sinister cyber criminal pursuits driven by personal gain.
One such group, SiegedSec, surfaced just days before the invasion, adopting the tagline “sieging their victim’s security.” Led by the hacktivist known by the alias “YourAnonWolf,” SiegedSec has rapidly expanded its operations, leaving a trail of victims in its wake.
While some posit that SiegedSec may be a faction within the Anonymous movement, it’s likened to a specialized unit within the broader hacktivist sphere.
Since its inception in late February 2022, DarkOwl analysts have documented SiegedSec’s defacement and compromise of no less than 11 websites, characterized by juvenile and crude language and graphics in the defacements.
By April, the group asserted its successful defacement of over 100+ domains, providing evidence through a chat dialogue indicating altered account passwords and corrected defacements. The group hinted at maintaining access to these domains.
Evidence suggests the group has infiltrated sensitive information and leaked emails or databases from a minimum of 30 different companies since its inception.
However, public notices of cybersecurity incidents from these companies have been notably scarce, likely due to many being smaller businesses or situated in non-English speaking regions.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.