Threat intelligence researchers at CloudSEK have uncovered a sophisticated phishing campaign targeting Indian entities using Income Tax-themed lures, attributed to the Chinese-aligned Silver Fox APT group.
The campaign employs an advanced multi-stage malware chain delivering Valley RAT, a modular remote access trojan with capabilities for long-term persistence and dynamic payload delivery.
The discovery notes the first public attribution of this particular campaign to Silver Fox, making accurate threat actor identification critical for Indian defenders.
Previous misattribution of similar phishing lures to India-aligned threat groups like SideWinder would fundamentally contradict the campaign’s victimology and operational patterns.
Attribution accuracy directly impacts incident response effectiveness organizations misled about threat actor identity will deploy countermeasures against the wrong adversary while the actual attacker remains undetected within their networks.
The campaign leverages visually authentic Income Tax Department documents as decoys, with malicious PDFs hosted on spoofed infrastructure designed to appear legitimate to potential victims.
Once clicked, the attack chain initiates automatically, displaying sophisticated evasion techniques and anti-analysis procedures that prevent detection by security researchers and sandbox environments.
Technical Kill Chain Analysis
The initial access vector relies on malicious email attachments containing a specially crafted PDF impersonating official Income Tax correspondence.
Upon user interaction, the PDF triggers automatic downloads of “tax affairs.exe” a Nullsoft Scriptable Install System (NSIS) installer containing the first stage of the attack payload.
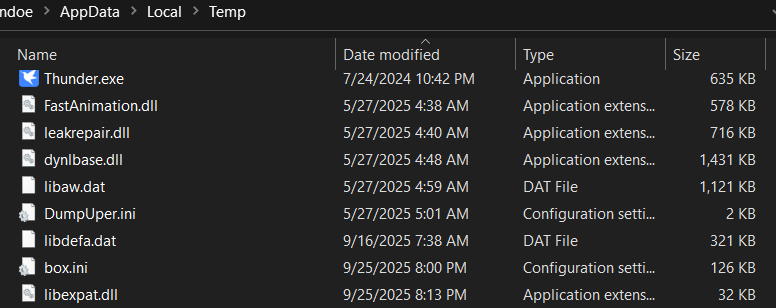
The installer employs DLL hijacking against Thunder.exe, a legitimate executable from the Xunlei download manager distributed with the malicious libexpat.dll.
When Thunder.exe executes from the temporary directory, Windows default DLL search order ensures libexpat.dll loads first, executing the malware’s core logic entirely in memory.
The libexpat.dll payload implements extensive anti-analysis techniques, including process enumeration to detect debugging tools and sandbox environment verification.
After confirming execution in a legitimate environment, it disables Windows Update services, decrypts a payload from box.ini, and injects this shellcode into explorer.exe using process hollowing a technique that maintains stealth while establishing persistent code execution.
The final payload deploys Valley RAT, a sophisticated remote access trojan configured with three-tier C2 failover infrastructure.
The malware implements dynamic beaconing with configurable sleep intervals, reducing detection likelihood through noise reduction.
Critically, Silver Fox operators can push updated C2 addresses through Windows registry manipulation without redeploying binaries or regaining initial access.
Valley RAT’s plugin architecture enables post-exploitation capability deployment on-demand.
Downloaded modules such as advanced keylogging, credential harvesters, or lateral movement tools are stored as registry REG_BINARY values for automatic persistence across system reboots. This design allows attackers to customize compromises based on victim value, delivering specialized espionage capabilities only when needed.
Defensive Implications
The campaign demonstrates sophisticated threat actor maturity through infrastructure compartmentalization, with primary C2 infrastructure (b.yuxuanow.top) supported by rotating secondary domains.
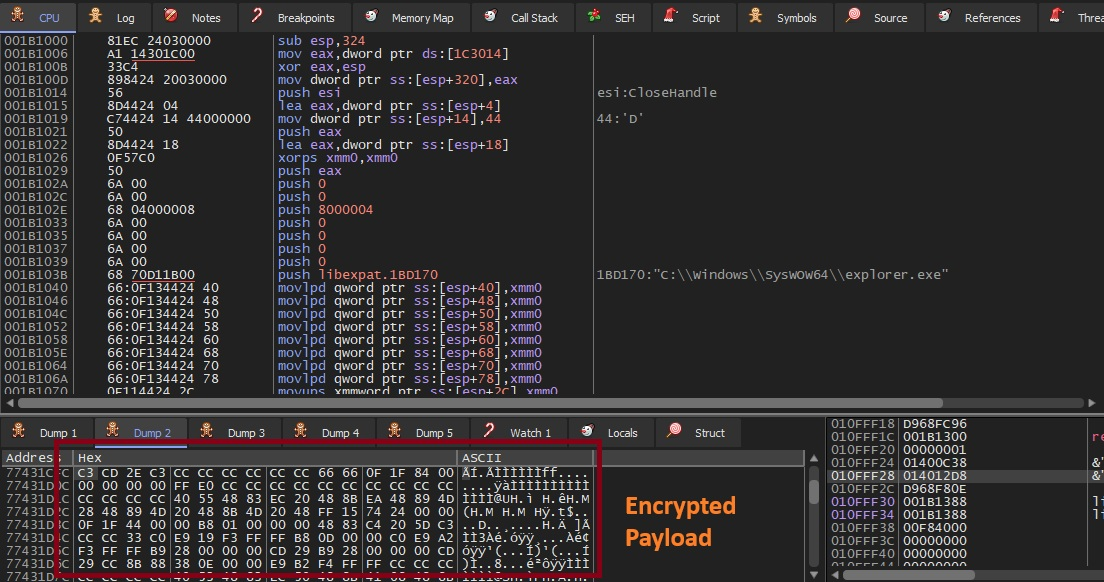
The injected payload can be dumped by attaching a debugger to the hollowed explorer.exe process and monitoring the memory region allocated via VirtualAllocEx.
Organizations should implement detection strategies focusing on behavioral signatures rather than static indicators: monitor registry anomalies under non-standard paths, detect multi-tier C2 retry patterns, and alert on signed binary execution from temporary directories paired with unusual DLL loads.
Memory-resident execution combined with registry-based persistence significantly complicates incident response and malware eradication efforts.
Given the threat’s ability to remain undetected during long infection periods, proactive hunting for RAT feature enablement particularly keylogging API activation provides crucial early warning before data exfiltration occurs.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
