A sophisticated cyberattack campaign targeting German organizations has been uncovered, utilizing weaponized LNK files to deploy the Sliver implant.
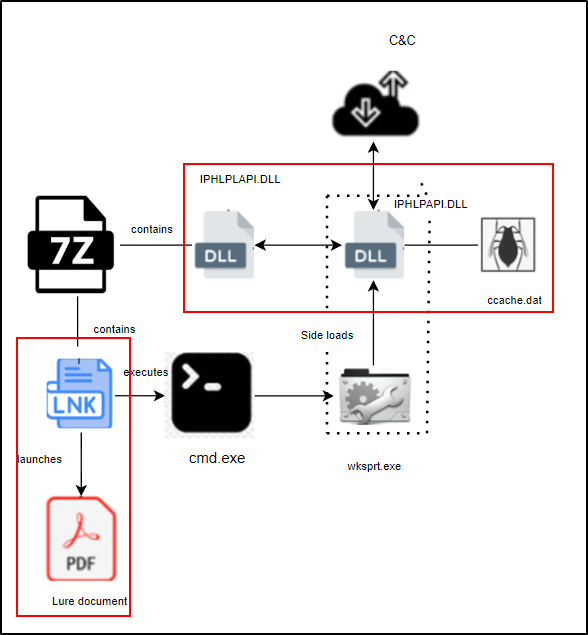
The attack begins with a deceptive archive file named “Homeoffice-Vereinbarung-2025.7z,” likely distributed via spear-phishing emails.
When extracted, the archive reveals a shortcut (.LNK) file disguised as a PDF document, exploiting user trust to initiate the infection chain.
Cybersecurity researchers at Cyble have identified this ongoing threat, which employs advanced evasion techniques to compromise systems and exfiltrate sensitive data.
Upon execution, the LNK file triggers a series of covert actions:-
- It extracts two components: a base64-encoded executable and a decoy PDF.
- The executable, obfuscated using .NET’s Confuser, is placed in the startup folder for persistence.
- A legitimate Windows executable, wksprt.exe, is copied to a newly created “Intel” directory in %localappdata%.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Technical Analysis
The malicious payload employs sophisticated techniques to evade detection:-
- DLL Sideloading: The legitimate wksprt.exe loads a malicious DLL named IPHLPAPI.dll.
- DLL Proxying: The malicious DLL forwards function calls to a renamed legitimate DLL (IPHLPLAPI.dll), maintaining normal application behavior while executing malicious code.
.webp)
The attack leverages multiple stages to deploy its final payload:-
- The malicious DLL reads and decrypts shellcode from an encrypted “ccache.dat” file.
- This shellcode is loaded directly into memory, bypassing disk-based detection methods.
- The decrypted content reveals the Sliver implant, an open-source command and control (C2) framework.
Once active, the Sliver implant establishes communication with its C2 servers:-
- hxxp://www.technikzwerg[.]de/auth/auth/authenticate/samples.html
- hxxp://www.technikzwerg[.]de/auth/auth/authenticate/samples.php
The implant uses Mutual TLS (mTLS) for secure communication, making detection more challenging. It has been observed using destination port 53, typically reserved for DNS requests, for its SSL connections.
Sliver’s capabilities include dynamic code generation, compile-time obfuscation, and support for both staged and stageless payloads.
This versatility allows attackers to conduct various malicious activities, including data exfiltration and further system compromise.
While attribution remains uncertain, the attack’s sophistication and targeting of German entities suggest a well-resourced threat actor.
The use of Sliver, previously associated with APT groups, indicates a potential shift in tooling among advanced persistent threats.
To defend against this threat, organizations should:-
- Implement strong email filtering systems to prevent malicious attachments.
- Use application whitelisting to block unauthorized LNK file execution.
- Deploy Endpoint Detection and Response (EDR) solutions to identify DLL sideloading and shellcode injection.
- Monitor for anomalous network activities, especially unexpected outbound connections on non-standard ports.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
