Researchers have uncovered a sophisticated phishing campaign zeroing in on Turkish enterprises, with a particular focus on the defense and aerospace industries.
Threat actors are masquerading as Turkish Aerospace Industries (TUSAŞ), a key defense contractor, to disseminate malicious emails that mimic legitimate contractual documents.
These emails carry a variant of the Snake Keylogger, an infamous information-stealing malware, concealed within files like “TEKLİF İSTEĞİ – TUSAŞ TÜRK HAVACILIK UZAY SANAYİİ_xlsx.exe.”
Phishing Targets Turkish Defense Sector
Upon execution, the malware deploys advanced persistence techniques, including PowerShell commands to exclude itself from Windows Defender scans and scheduled tasks for automatic startup, enabling it to harvest sensitive data such as credentials, cookies, and financial details from numerous browsers and email clients without detection.
This operation has been reported to Turkey’s National Computer Emergency Response Team (USOM), with ongoing collaborations to alert affected parties and curb further dissemination.
The malware’s file is a PE32 executable for MS Windows, with a SHA256 hash of 0cb819d32cb3a2f218c5a17c02bb8c06935e926ebacf1e40a746b01e960c68e4, and it exhibits suspicious behaviors like spawning processes via NtCreateUserProcess syscalls, including PowerShell invocations to add exclusions and schtasks.exe commands to establish persistence through XML-defined tasks in temporary directories.
Technical Breakdown of Malware Unpacking
Delving deeper into the technical intricacies, the Snake Keylogger sample, initially presenting as a benign .NET Windows Forms application named “vJfV.exe,” initializes a deceptive temperature conversion interface to mask its malicious intent.
Within its constructor, it leverages Activator.CreateInstance to instantiate a type loaded via Assembly.Load, effectively unpacking an embedded payload in memory.
This matryoshka-style layering is unpacked using tools like Chiron Unpacker, revealing the core malicious binary “jVf4P.bin” under the assembly name “Remington.”
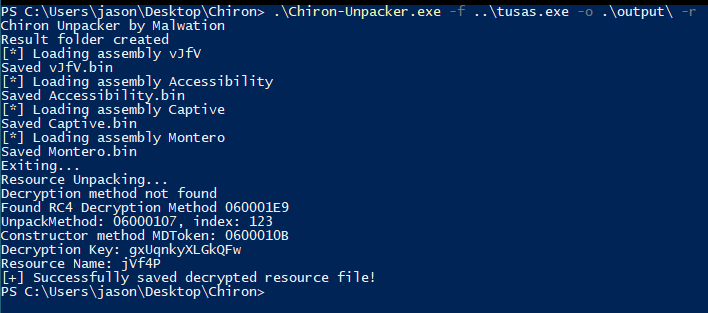
The malware incorporates empty anti-analysis routines for virtual machines, sandboxes, Windows Defender, and Task Manager, suggesting a streamlined evasion strategy.
It systematically extracts data from email clients like Outlook, FoxMail, and Thunderbird by traversing registry keys, classifying and decrypting passwords with custom functions.
Furthermore, it targets autofill, credit card, download history, top sites, and cookie data from an extensive list of browsers, including Chrome, Firefox, Brave, Vivaldi, Microsoft Edge, and niche variants like CocCoc, Orbitum, and Comodo.
Anti-bot features check against known sandbox IP addresses, while data exfiltration occurs via configurable channels such as SMTP, FTP, servers, Telegram, or Discord.
Configuration analysis reveals DES-encrypted SMTP credentials, decrypted using Python scripts that expose details like the email “[email protected],” server “mail.htcp.homes,” receiver “[email protected],” and port 587.
A custom YARA rule detects the Cassandra Protector used in the sample, flagging .NET binaries with high-entropy sections, specific libraries like System.Drawing.Bitmap, and characteristic function patterns.
Additional hashes from unpacked components include Montero (3c9cddf85962249a967b3827e3edb4acb710dc0e3088c619342e2ce6df35bfbc), vJfV (82fa8156e9d4fb47cd20908818b9172f86ed13eb683041658f242c58ce0a9cff), jVf4P (2859b8700fc6111c40b806d114c43e2e3b4faa536eeab57d604818562905b911), and Captive (11f577cc6b6af304332d47fba2122ffb193e81378662ea7093ebe971107d89d6).
Defenders are urged to deploy the provided YARA rule and monitor for these indicators to preempt similar threats.
Key Indicators of Compromise (IoCs)
| Indicator Type | Value |
|---|---|
| Filename | TEKLİF İSTEĞİ – TUSAŞ TÜRK HAVACILIK UZAY SANAYİİ_xlsx.exe |
| SHA256 (Main Sample) | 0cb819d32cb3a2f218c5a17c02bb8c06935e926ebacf1e40a746b01e960c68e4 |
| SHA256 (Montero) | 3c9cddf85962249a967b3827e3edb4acb710dc0e3088c619342e2ce6df35bfbc |
| SHA256 (vJfV) | 82fa8156e9d4fb47cd20908818b9172f86ed13eb683041658f242c58ce0a9cff |
| SHA256 (jVf4P) | 2859b8700fc6111c40b806d114c43e2e3b4faa536eeab57d604818562905b911 |
| SHA256 (Captive) | 11f577cc6b6af304332d47fba2122ffb193e81378662ea7093ebe971107d89d6 |
| SMTP Email | [email protected] |
| SMTP Server | mail.htcp.homes |
| SMTP Receiver | [email protected] |
| SMTP Port | 587 |
Get Free Ultimate SOC Requirements Checklist Before you build, buy, or switch your SOC for 2025 - Download Now
