Software supply chain attacks hit levels in October that were more than 30% higher than any previous month.
Threat actors on dark web data leak sites claimed 41 supply chain attacks in October, 10 more than the previous high seen in April 2025, Cyble reported today in a blog post.
Supply chain attacks have more than doubled since April, averaging more than 28 a month compared to the 13 attacks per month seen between early 2024 and March 2025, Cyble said (chart below).

Reasons Behind the Record Supply Chain Attacks
The threat intelligence company cited several reasons for the increase in attacks.
The primary drivers of the surge in supply chain attacks have been a “combination of critical and zero-day IT vulnerabilities and threat actors actively targeting SaaS and IT service providers,” the blog post said, noting that “the sustained increase suggests that the risk of supply chain attacks may remain elevated going forward.”
Cloud security threats and AI-based phishing campaigns are other causes cited by Cyble, although voice phishing (vishing) also played a large role in recent Scattered LAPSUS$ Hunters Salesforce breaches.
IT Companies Hit Hardest as Ransomware Groups Lead Attacks
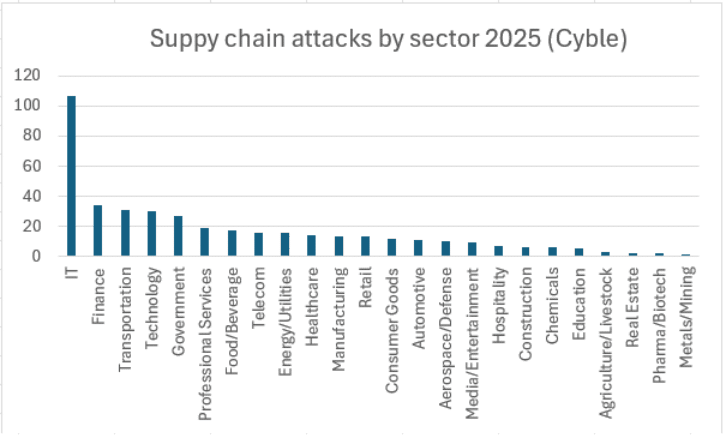
All 24 industry sectors tracked by Cyble have been hit by a supply chain attack this year, but IT and IT services companies have been by far the biggest target because of “the rich target they represent and their downstream customer reach.” The 107 supply chain attacks targeting IT companies so far this year have been more than triple those of the next nearest sectors, which include financial services, transportation, technology and government (chart below).

Ransomware groups have been some of the biggest contributors to the increase in supply chain attacks.
Qilin and Akira have been the top two ransomware groups so far this year, and the two have also claimed “an above-average share of supply chain attacks,” Cyble said.
Akira’s recent victims have included an unnamed “major open-source software project,” the threat researchers said, and the 23GB of data stolen by the group includes “internal confidential files, and reports related to software issues and internal operations,” among other information.
Akira and Qilin have also claimed a number of attacks on IT companies, including some serving sensitive sectors such as government, intelligence, defense, law enforcement agencies, healthcare, industrial and energy companies, and payment processing and financial infrastructure solutions. In one incident, Qilin claimed to have stolen source code for proprietary software products used by law enforcement, criminal justice, public safety, and security organizations.
In one case, Qilin claimed to have breached customers of a U.S.-based cybersecurity and cloud services provider for healthcare and dental organizations through “clear-text credentials stored in Word and Excel documents hosted on the company’s systems.”
Kyber, a new ransomware group, leaked more than 141GB of project files, internal builds, databases, and backup archives allegedly stolen from “a major U.S.-based defense and aerospace contractor that provides communication, surveillance, and electronic warfare systems.”
Cl0p ransomware group exploits of Oracle E-Business Suite vulnerabilities a Red Hat GitLab breach were among the other major incidents in October.
Protecting Against Supply Chain Risks
The Cyble researchers said that guarding against supply chain attacks ”can be challenging because these partners and suppliers are, by nature, trusted, but security audits and assessing third-party risk should become standard cybersecurity practices.”
The researchers outlined several steps security teams can take to better protect their organizations.
“The most effective place to control software supply chain risks is in the continuous integration and development (CI/CD) process, so carefully vetting partners and suppliers and requiring good security controls in contracts are essential for improving third-party security,” the threat researchers added.
