A newly discovered information-stealing malware, SolyxImmortal, has emerged as a persistent surveillance threat targeting Windows users.
Distributed through underground Telegram channels, this Python-based implant combines credential theft, document harvesting, keystroke logging, and screen capture capabilities into a continuously running surveillance framework that operates silently in the background.
First detected in January 2026, the malware prioritizes long-term access over rapid execution, leveraging Discord webhooks for command-and-control communication to evade traditional network detection mechanisms.
SolyxImmortal arrives as a 10.29 KB Python script named “Lethalcompany.py” with the SHA-256 hash 5a1b440861ef652cc207158e7e129f0b3a22ed5ef5d2ea5968e1d9eff33017bc.
Upon execution, the malware establishes persistence by copying itself into the user’s AppData directory under a Windows-like filename, marking it as hidden and system-protected to avoid casual detection.
It registers itself under the current user’s Run registry key to ensure automatic execution on every login without requiring administrative privileges. This persistence mechanism enables continuous monitoring across system reboots while remaining entirely in user space.
The malware hardcodes two distinct Discord webhook URLs directly into its source code, one for structured data exfiltration including credentials and compressed document archives, and another dedicated solely to screenshot transmission.
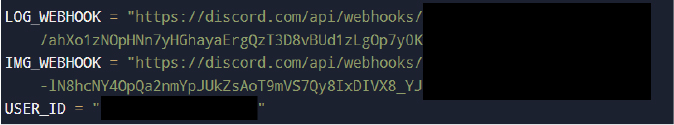
A hardcoded Discord user ID enables direct operator mentions for high-value authentication events, ensuring immediate notification when users access banking portals or email services.
This design reflects confidence that Discord’s HTTPS infrastructure and reputation will shield malicious traffic from network-based detection systems.
Credential Harvesting and Surveillance
SolyxImmortal addressed Chromium-based browsers including Chrome, Edge, and Brave by accessing their known profile directory paths.
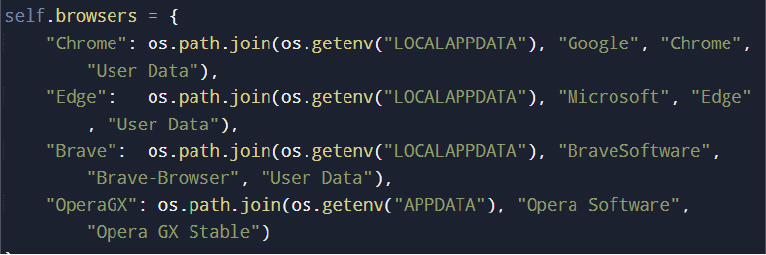
It extracts the master encryption key from each browser’s Local State file and uses Windows Data Protection API to decrypt it within the current user context.
Saved login credentials are then retrieved from browser SQLite databases and decrypted using AES-GCM, producing plaintext username-password pairs that are aggregated for exfiltration without further obfuscation.
Beyond credential theft, the malware recursively scans the user’s home directory for documents with extensions including DOC, DOCX, PDF, TXT, and XLSX while filtering files based on size thresholds to balance data collection with operational efficiency.
All harvested content is staged in the system’s temporary directory and compressed into ZIP archives before transmission, reducing network transfer size and consolidating exfiltration into fewer outbound connections that are less likely to trigger anomaly detection.
Keystroke capture operates through a persistent keyboard hook that appends captured keystrokes to an in-memory buffer rather than transmitting them immediately.
A dedicated background thread periodically exfiltrates buffered data at fixed intervals, reducing the frequency of network communication.
Simultaneously, the malware monitors the active foreground window title against predefined keyword lists associated with authentication, financial services, or account management platforms.
When trigger words are detected, SolyxImmortal captures an immediate screenshot and transmits it through its dedicated webhook channel, supplemented by routine screenshots taken at fixed intervals for continuous visual surveillance.
Intelligence collected during analysis indicates that SolyxImmortal was initially distributed via an underground Telegram channel commonly associated with commodity malware sharing and builder-based tooling.
The malware’s codebase contains linguistic artifacts, naming conventions, and variable patterns consistent with Turkish-speaking threat actors previously observed in hacktivist underground communities.
Mitigations
Defensive opportunities exist primarily in behavioural indicators rather than static signatures. Security teams should monitor for process execution originating from user-writable paths such as AppData and TEMP directories, particularly when accessing browser credential stores or invoking Windows DPAPI for decryption.
After successful data exfiltration, the malware removes temporary directories and files used for staging collected data.
Unauthorized registry modifications to user-level Run keys combined with file compression followed by outbound HTTPS connections represent high-confidence detection opportunities.
Organizations should enforce application allowlisting to prevent execution of unauthorized binaries from user-writable directories and implement network monitoring for repeated HTTPS POST requests to webhook-based services initiated by background or non-interactive processes.
Browser credential protection mechanisms and regular hunting for executables masquerading as legitimate system components within user profile directories further strengthen defensive posture against this class of threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
