Security researchers at Bishop Fox have published complete exploitation details for the CVE-2024-53704 vulnerability that allows bypassing the authentication mechanism in certain versions of the SonicOS SSLVPN application.
The vendor warned about the high exploitation possibility of the flaw in a bulletin on January 7, urging administrators to upgrade their SonicOS firewalls’ firmware to address the problem.
“We have identified a firewall vulnerability that is susceptible to actual exploitation for customers with SSL VPN or SSH management enabled, and that should be mitigated immediately by upgrading to the latest firmware,” warned SonicWall in an email sent to customers at the time.
The flaw allows a remote attacker to hijack active SSL VPN sessions without authentication, granting them unauthorized access to the victim’s network.
On January 22 Bishop Fox researchers announced that they had developed an exploit for CVE-2024-53704 after a “significant reverse-engineering effort,” confirming SonicWall’s fears about the exploitation potential of the vulnerability.
Source: Bishop Fox
After allowing some time for system administrators to apply the available patches, Bishop Fox released the full exploitation details on Monday.
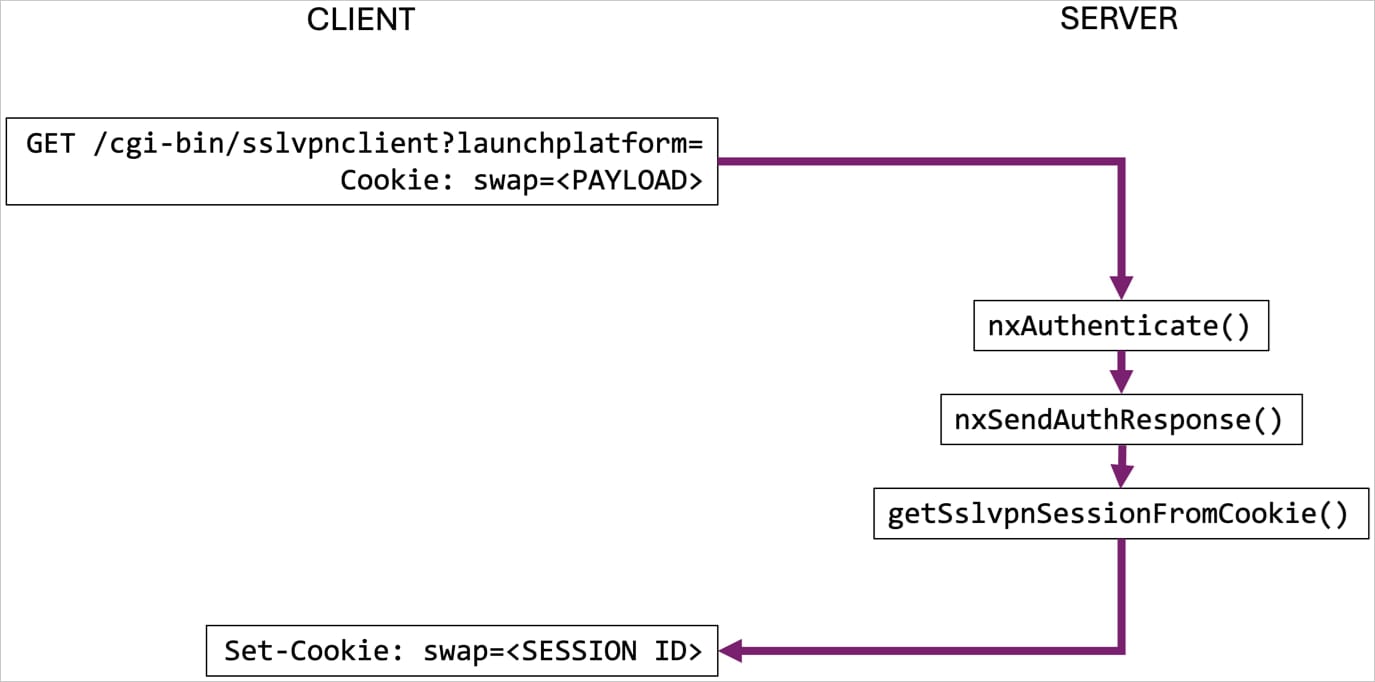
The exploit works by sending a specially crafted session cookie containing a base64-encoded string of null bytes to the SSL VPN authentication endpoint at ‘/cgi-bin/sslvpnclient.’
This triggers an incorrect validation of the session, as the mechanism assumes that the request is associated with an active VPN session.
This logs out the victim and gives the attacker access to the session, allowing them to read the user’s Virtual Office bookmarks, obtain VPN client configuration settings, open a VPN tunnel to the internal network, and provides access to private network resources.
Source: Bishop Fox
The researchers put the validity of their analysis to the test and created a proof-of-concept exploit code to simulate an authentication bypass attack. The response headers showed that they had successfully hijacked an active session.
“With that, we were able to identify the username and domain of the hijacked session, along with private routes the user was able to access through the SSL VPN,” the researchers said.
Security updates available
The issue impacts SonicOS versions 7.1.x (up to 7.1.1-7058), 7.1.2-7019, and 8.0.0-8035. These versions run in multiple models of Gen 6 and Gen 7 firewalls, as well as SOHO series devices.
Fixes were made available in SonicOS 8.0.0-8037 and later, 7.0.1-5165 and higher, 7.1.3-7015 and higher, and 6.5.5.1-6n and higher. For model-specific information, check out SonicWall’s bulletin here.
Bishop Fox says that internet scans as of February 7 show roughly 4,500 internet-exposed SonicWall SSL VPN servers without the security updates fixing CVE-2024-53705.
With a working proof-of-concept exploit now publicly available, admins should apply the updates as soon as possible because the exploitation risk for CVE-2024-53705 has increased significantly.
