SonicWall warns that SonicOS bug exploited in attacks

Recently fixed access control SonicOS vulnerability, tracked as CVE-2024-40766, is potentially exploited in attacks in the wild, SonicWall warns.
SonicWall warns that a recently fixed access control flaw, tracked as CVE-2024-40766 (CVSS v3 score: 9.3), in SonicOS is now potentially exploited in attacks.
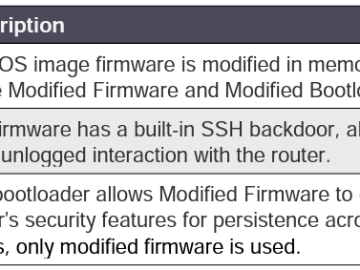
“An improper access control vulnerability has been identified in the SonicWall SonicOS management access and SSLVPN, potentially leading to unauthorized resource access and in specific conditions, causing the firewall to crash.” reads the SonicWall’s advisory.
“This issue affects SonicWall Gen 5 and Gen 6 devices, as well as Gen 7 devices running SonicOS 7.0.1-5035 and older versions. This vulnerability is potentially being exploited in the wild. Please apply the patch as soon as possible for affected products. The latest patch builds are available for download on mysonicwall.com“
“This vulnerability is potentially being exploited in the wild. Please apply the patch as soon as possible for affected products. The latest patch builds are available for download on mysonicwall.com,” warns the updated SonicWall advisory.
Threat actors can exploit the vulnerability to gain unauthorized resource access and crash the impacted firewalls.
“An improper access control vulnerability has been identified in the SonicWall SonicOS management access and SSLVPN, potentially leading to unauthorized resource access and in specific conditions, causing the firewall to crash.” reads the advisory.
The company urges customers to apply patches as soon as possible. The vendor also provided a workaround to minimize potential risks, they recommended to restrict firewall management to trusted sources or disable firewall WAN management from Internet access. Similarly, for SSLVPN, ensure that access is limited to trusted sources or disable SSLVPN access from the Internet.
Below is the list of impacted platforms:
| Impacted Platforms | Impacted Versions |
| SOHO (Gen 5) | 5.9.2.14-12o and older versions |
| Gen6 Firewalls -SOHOW, TZ 300, TZ 300W, TZ 400, TZ 400W, TZ 500, TZ 500W, TZ 600, NSA 2650,NSA 3600, NSA 3650, NSA 4600, NSA 4650, NSA 5600, NSA 5650, NSA 6600, NSA 6650, SM 9200, SM 9250,SM 9400, SM 9450, SM 9600, SM 9650, TZ 300P, TZ 600P, SOHO 250, SOHO 250W, TZ 350, TZ 350W | 6.5.4.14-109n and older versions |
| Gen7 Firewalls – TZ270, TZ270W, TZ370, TZ370W, TZ470, TZ470W, TZ570, TZ570W,TZ570P, TZ670, NSa 2700, NSa 3700,NSa 4700, NSa 5700, NSa 6700, NSsp 10700, NSsp 11700, NSsp 13700 | SonicOS build version 7.0.1-5035 and older versions. * However SonicWall recommends youinstall the latest firmware. |
“SonicWall strongly advises that customers using GEN5 and GEN6 firewalls with SSLVPN users who have locally managed accounts immediately update their passwords to enhance security and prevent unauthorized access. Users can change their passwords if the “User must change password” option is enabled on their account. Administrators must manually enable the “User must change password” option for each local account to ensure this critical security measure is enforced.” concludes the advisory.
For GEN6 Firewalls, the vendor recommends enabling MFA (TOTP or Email-based OTP) for all SSLVPN users.
In January, experts warned of two unauthenticated denial-of-service vulnerabilities, tracked as CVE-2022-22274 and CVE-2023-0656, impacting SonicWall next-generation firewall (NGFW) series 6 and 7 devices.
The flaws could potentially lead to remote code execution. Despite a proof-of-concept exploit for the flaw CVE-2023-0656 was publicly released, the vendor reported it was aware of attacks in the wild exploiting the vulnerabilities.
However, researchers from Bishop Fox used BinaryEdge source data to find SonicWall firewalls with management interfaces exposed to the internet. The experts found that 76% (178,637 of 233,984) of the Internet-facing firewalls are vulnerable to one or both issues.
The experts pointed out that the two issues are fundamentally the same, but exploitable at different HTTP URI paths due to the reuse of a vulnerable code pattern. The researchers also developed a test script to determine whether a device is vulnerable without crashing it.
This means that the impact of a large-scale attack could be severe.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
Pierluigi Paganini
(SecurityAffairs – hacking, SonicWall)