Russian nation-state actor Star Blizzard has been running a new spear-phishing campaign to compromise WhatsApp accounts of targets in government, diplomacy, defense policy, international relations, and Ukraine aid organizations.
According to a Microsoft Threat Intelligence report, the campaign was observed in mid-November 2024 and represents a tactical shift for Star Blizzard as a response to the recent exposure of the threat actor’s tactics, techniques, and procedures.
Malicious WhatsApp invitation
Star Blizzard starts the attack by impersonating a U.S. government official in email messages to the target. The lure is an invitation to join a WhatsApp group related to non-governmental initiatives supporting Ukraine.
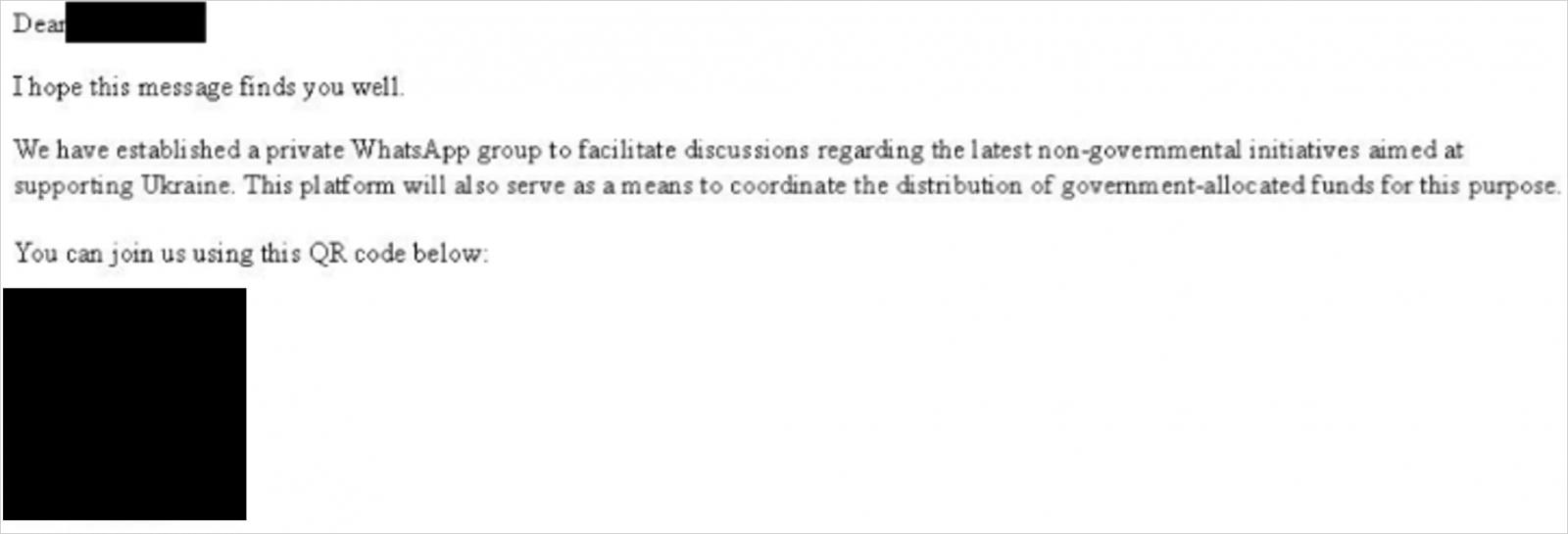
Source: Microsoft
The email contains a purposefully broken QR code, in an attempt to force a reply from the recipient requesting an alternative link.
If the victim responds, Star Blizzard sends another email with a ‘t.ly’ short link, which directs them to a fake webpage that mimics a legitimate WhatsApp invitation page with a new QR code.
.jpg)
Source: Microsoft
However, the new QR code is to link a new device, the attacker’s, to the victim’s WhatsApp account.
“If the target follows the instructions on this page, the threat actor can gain access to the messages in their WhatsApp account and have the capability to exfiltrate this data using existing browser plugins, which are designed for exporting WhatsApp messages from an account accessed via WhatsApp Web,” explains Microsoft.
As the attack relies solely on social engineering and there’s no malware involved for antivirus tools to detect, users should be wary of unsolicited communications and exercise extra caution when receiving invitations to join groups.
It is also a good idea to check the devices linked to your WhatsApp account. This is possible from the “Linked devices” options in the application on the mobile device (iPhone or Android) and log out any device you don’t recognize.
This phishing campaign shows that Star Blizzard’s activity disruption in October 2024, when Microsoft and the U.S. Department of Justice seized or took down more than 180 domains used by the Russian threat group, did not have a long-term impact and the hackers continued their operations by exploring other attack vectors.




