Group-IB’s cybersecurity researchers made a significant discovery, revealing undisclosed attack infrastructure employed by the highly active state-sponsored group SideWinder. Their targets mainly encompassed entities situated in:-
In a collaborative report, cybersecurity firms Group-IB and Bridewell disclosed the existence of a comprehensive network consisting of 55 domains and IP addresses exploited by the malicious actor.
While the phishing domains that the researchers identify mimic many organizations from various sectors, including the following:-
- News
- Government
- Telecommunications
- Financial
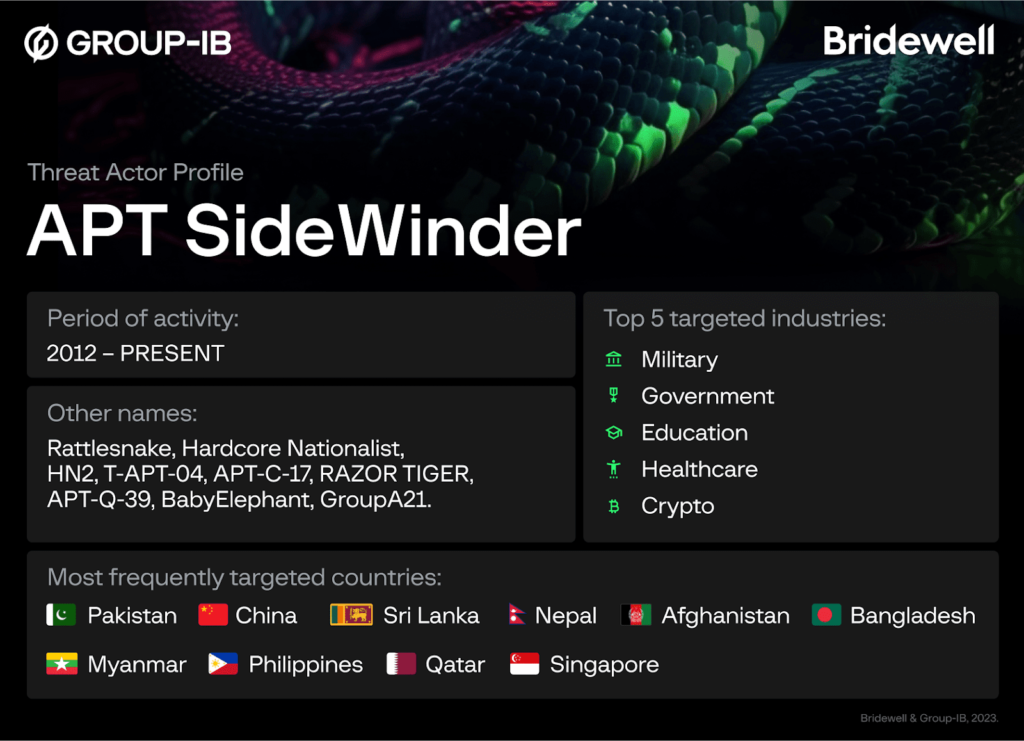
Operating since 2012, SideWinder is a long-standing threat actor known for its persistent activity. Their attack strategies heavily rely on spear-phishing techniques to gain unauthorized access to targeted systems.

SideWinder effectively establishes a foothold within the desired environments by employing spear-phishing as a primary intrusion method.
The group’s target range is widely associated with espionage activities linked to India’s interests, indicating a strong connection.
Targeted Nations
Here below, we have mentioned all the nations that the operators of this APT group frequently target:-
- Pakistan
- China
- Sri Lanka
- Afghanistan
- Bangladesh
- Myanmar
- Philippines
- Qatar
- Singapore
Infrastructre of SideWinder Hacker Group
In February of this year, Group-IB revealed compelling evidence pointing toward SideWinder’s potential involvement in targeting over 61 organizations in Asia.
The affected entities encompassed government, military, law enforcement, and various other sectors. The timeframe for these attacks spanned from June to November 2021, highlighting the extent and duration of SideWinder’s campaign.

While recently, it has been observed that SideWinder evasively attacked Pakistani government organizations by using server-based polymorphism.
In the following countries, the government organizations were mimicked by the domains that were identified recently:-
The WHOIS records of all these domains show identical values with registration details. These domains contain deceptive government-themed files aimed at downloading a subsequent undisclosed payload.
Most of these files originating from Pakistan were uploaded to VirusTotal in March 2023. One of the files is a Microsoft Word document allegedly originating from the Pakistan Navy War College (PNWC).

In late November 2022, a Windows shortcut (LNK) file was discovered and uploaded to VirusTotal from Beijing.
The LNK file is designed to execute an HTA file from a remote server, impersonating the email system of Tsinghua University. It serves the purpose of running an HTML application.
It has been discovered that SideWinder’s infrastructure is laced with a malicious Android APK file (226617) discovered during the further investigation and disguised as “Ludo Game.”
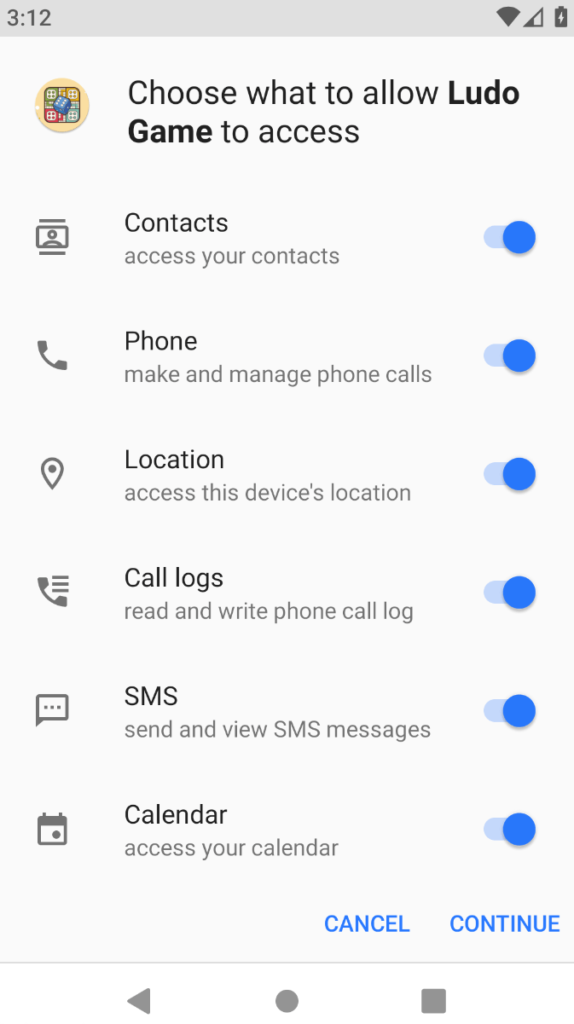
Upon successful installation of this malicious app, it asks users for the following access on their device:-
- Contacts
- Location
- Phone logs
- SMS messages
- Calendar
Threat actors could easily monitor the device and harvest sensitive user data by gaining access to such permissions on the Android device.
Organizations should prioritize implementing business email protection solutions to counter SideWinder’s reliance on targeted spear-phishing effectively.

Utilizing threat intelligence solutions proves to be a more practical approach to enhancing indicators of compromise and staying informed about pertinent threats.
By deploying such solutions, organizations can effectively safeguard their systems and networks from the initial vectors employed by SideWinder.
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus





