By Toby Bussa, VP of Product Marketing, ThreatConnect
Introduction
In an era where cyber threats loom larger and are more complex than ever, it is vitally important for organizations to have a cyber threat intelligence (CTI) program and implement threat intelligence operations (TI Ops) to bolster their defenses. TI Ops is a strategic necessity that maximizes the impact and value of threat intelligence investments, enabling organizations to be prepared to defend against their most relevant threats.
The Essential Characteristics of Threat Intelligence Operations
TI Ops is characterized by foundational “tenets,” each serving as a pillar that supports and guides the effective implementation and operationalization of a threat intelligence program. These tenets underscore the need for a proactive, focused, and business-aligned approach to managing and mitigating cyber threats, emphasizing the importance of understanding and countering adversaries with insights and precision. The tenets are:
- Elevate threat intelligence to a mandatory, critical security operations role.
- Leverage an Evolved Threat Intelligence Lifecycle, one that emphasizes the planning and requirements and the use of threat intel by consumers.
- Align and focus threat intel on the most critical risks to the business through a living set of requirements.
- Focus not solely on indicators of compromise, but also on the motivations, tactics, techniques, trends, tools, and infrastructure patterns of threat actors.
- Automate the work of the TI Ops team.
- Integrate and automate threat intel into every aspect of security and cyber risk management.
- Create measures of effectiveness and success for produced and consumed threat intel that are understandable and relevant to the business.
Let’s dig into some of these characteristics in more detail.
The Need for Evolved Tradecraft
TI Ops needs an Evolved Threat Intelligence Lifecycle approach. The traditional Cyber Threat Intel Lifecycle focuses on intel production, but there is little focus on consumers and stakeholders. The Evolved Lifecycle addresses those shortcomings. For example, it focuses on both the production and consumption of CTI and includes “connective tissue” phases between the two activities – Dissemination and Integration, and Feedback and Validation. The Evolved Lifecycle underpins how TI Ops should function.
| Traditional Threat Intel Lifecycle | The Evolved Threat Intel Lifecycle |
Figure 1
Analysts in the Spotlight
Analysts are the heart of TI Ops. Analysts are encouraged to adopt an intel consumer-centric mentality and ensure their activities are guided by clearly defined, documented intel requirements. This approach not only elevates the role of analysts but also enhances the overall quality and relevance of threat intelligence outputs.
The Role of AI and Automation
TI Ops places an emphasis on AI and automation. AI is a potential game changer for cybersecurity. AI has been employed for several years, e.g., using machine learning for identifying domain generation algorithms (DGAs) and in user and entity behavior analytics (UEBA). More recently, natural language processing (NLP) and generative AI (GenAI) have emerged as additional capabilities to help ease the burden on analysts.
Automation is a key enabler that streamlines work, allowing analysts to dedicate their efforts to higher-value activities, like intel analysis and production. It facilitates the dissemination of threat intelligence across security operations and cyber risk management, enhances the efficiency and effectiveness in identifying, assessing, and responding to threats, bolsters defenses, and helps make organizations more resilient to attacks.
Employing Threat Intel
Adopting and using threat intelligence in every appropriate aspect of an organization’s cybersecurity activities is crucial. This is called Intelligence-Powered Security Operations.
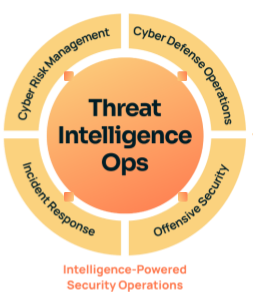
Figure 2
This approach puts cyber threat intel at the center of security operations and cyber risk programs where unified threat intelligence is leveraged to inform, direct, and provide context. For example, strategic threat intelligence is used to inform cybersecurity strategy, like where to focus enhancements to security controls to improve defenses. Threat intelligence also aids and benefits from cyber risk management. Prioritizing vulnerabilities is a continual challenge between security operations and IT. TI Ops will determine the vulnerabilities (e.g., CVEs) that are being exploited by threat actors and alert IT and asset owners. When cyber risks to business critical assets are quantified in financial terms (i.e., through cyber risk quantification), it makes prioritization very precise. Mitigation decisions can be made weighing the financial impact to an asset if it was impacted by a threat, rather than using qualitative approaches like critically defined as high, medium, or low.
Measuring the Value of Threat Intelligence
Having metrics and getting feedback from stakeholders is imperative for creating measures of effectiveness and success that are both understandable and directly relevant to the business. Such metrics are crucial for demonstrating the tangible value of threat intelligence investments and efforts and ensuring alignment with organizational objectives.
The Need for a Modern Platform
Adopting a modern threat intelligence operations platform is central to TI Ops. Such a platform is a nexus that combines human analysis with AI-powered analytics, automation, visualizations, and integrations. It should also offer capabilities like easy access to threat intel data, mechanisms for defining and actioning intelligence requirements, comprehensive built-in reporting capabilities, and the ability to generate metrics and calculate the ROI of threat intel investments.
Conclusion
By embracing TI Ops, leaders can significantly enhance their cybersecurity effectiveness, improve response times to emerging threats, and deliver measurable value to their organizations. TI Ops is not just another method for managing threat intelligence but a transformative approach that redefines how organizations combat cyber threats.
Cybersecurity leaders need to embrace the strategic importance of TI Ops and incorporate it into the fabric of an organization’s security functions and strategies. By adhering to the principles and practices covered here, CISOs and CTI leaders can elevate the organization’s security posture and ensure it remains resilient in the face of an ever-evolving cyber threat landscape.
About the Author
 Toby Bussa is VP of Product Marketing at ThreatConnect. He has over 20 years of experience in cybersecurity as a practitioner and leader. He recently was a VP Analyst at Gartner where he covered security operations topics, including SIEM, SOAR, MDR, DFIR and SOCs. He previously led IT security operations, data protection, security architecture and engineering, and 3rd party risk management for a FTSE100 enterprise, and the EMEA SOC threat detection team for a global MSSP. He can be reached at our company website http://www.threatconnect.com
Toby Bussa is VP of Product Marketing at ThreatConnect. He has over 20 years of experience in cybersecurity as a practitioner and leader. He recently was a VP Analyst at Gartner where he covered security operations topics, including SIEM, SOAR, MDR, DFIR and SOCs. He previously led IT security operations, data protection, security architecture and engineering, and 3rd party risk management for a FTSE100 enterprise, and the EMEA SOC threat detection team for a global MSSP. He can be reached at our company website http://www.threatconnect.com




