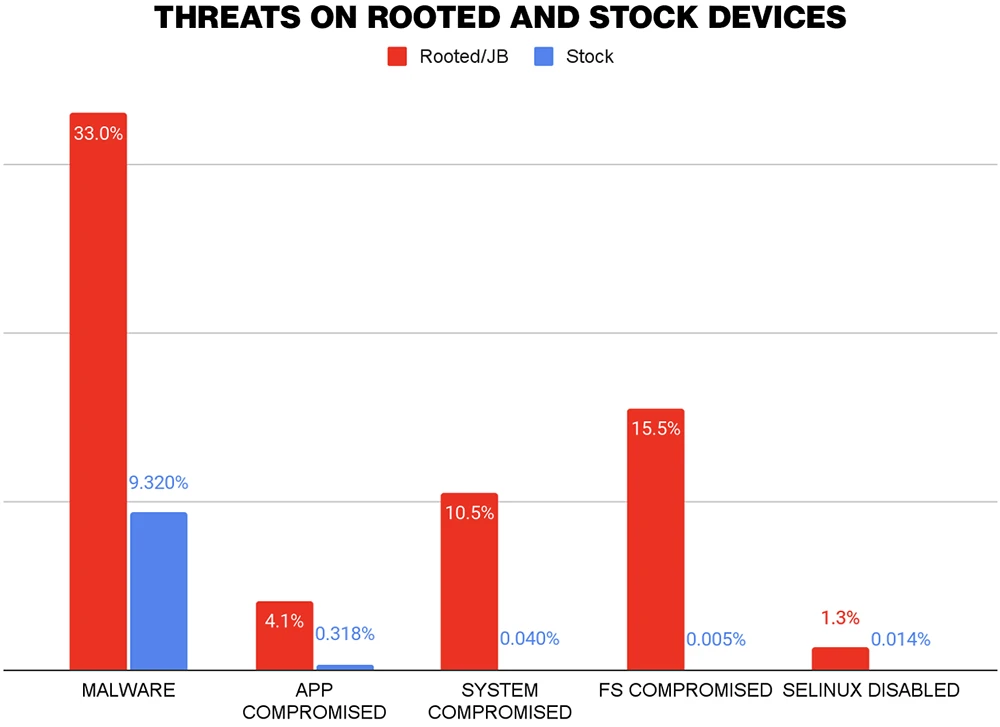
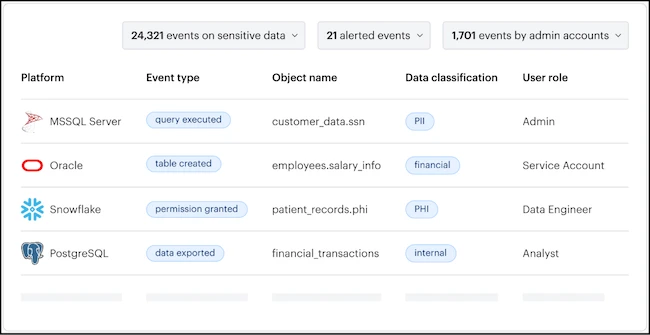
In this Help, Net Security interview, Michael Oberlaender, ex-CISO, and book author, discusses how to strike the right balance between security and operational efficiency.
Oberlaender advises companies starting their cybersecurity journey and stresses the importance of aligning with various frameworks. He also introduces his latest book, which provides insights into the CISO role and effective cybersecurity leadership.
How do you balance the need for security with operational efficiency and flexibility in an organization’s cybersecurity strategy?
It is essential to understand that while security is indeed paramount for any company, it also needs to blend into the overall business processes and operational efficiency – so, instead of becoming a roadblock in every single undertaking, ensure that security is becoming part of the process. Imagine a road with three lanes: the one on the far left (the fast lane, if you’re not in England or Australia etc.) is the one you can imagine the business is on without any security controls, fast, but risky. Any crash will lead to not only, but total disruption on the highway for ling periods of time when a crash occurs.
On the opposite side, the far right lane (truck lane, again, if not in left-hand traffic) is where security is overburdened, many controls, not all of them making sense, poor implementation, and slowing down all following traffic). Now, imagine the middle lane: here, you have security controls, allowing you to move faster while still in a controlled fashion; you can do faster when needed and fall back into slower mode when needed.
Security supports the business, the controls are aligned and make perfect sense, their implementation is smooth, they are behind the scenes, and you can always get help quickly. In case of an accident, you can move to either the left, or the right, so you actually have more options than on any of the other lanes, so this is quite flexible as well. You can see where I am going with this, right?
Similarly you need to be flexible with your cybersecurity strategy – develop your long term strategy, and start executing it – but use tactics to do so – when it aligns well with a business opportunity, the chances to succeed are far greater than when to do so during the middle of a business disruption. Learn to leverage the upcoming situations as great opportunities for your long-term advancement of the security strategy.
What advice would you give organizations beginning to develop a cybersecurity strategy from scratch?
Well, that is what I have done almost as often as I have previously served as CISO. Here are a couple of important points:
1. Every company is a target and will be hacked; it is just a function of time and opportunity.
2. You can’t become a falcon from a chick in one flight; there will be middle steps, and you need to start building the foundational platform before you reach the eagle’s nest. So, you need to establish solid disaster recovery (DR) plans, then business continuity plans (BCP), and operational capabilities (like measuring your IT, measuring your problems, measuring your security issues/impacts).
Then take it one (or a few) steps at a time, tighten the screws. Establish your security operations center (SOC), perform consistent, immutable backups (on non-online systems), rollout some antimalware features, get your identity and access management (IAM) in order, build your fortress with firewalls, DMZs, zero trust networks, cloud security zones, develop your encryption vision, key management systems, activate the encryption and perform key rotation. Stabilize, optimize, and then next rounds of upgrades.
This sort of staggered approach will help the companies to not get overwhelmed while also establishing important capabilities fast. One last item: especially such companies that never did security: you will face a breach, don’t drop your newly created efforts for security, instead, understand that this is part of the game. If you continue to ignore security, there will come a time when you will cease to exist.
How can organizations align their cybersecurity strategies with national and international cybersecurity frameworks and guidelines?
It is important to understand that there are plenty such frameworks, and guidelines – just imagine in a short blast: ISO27XXX, NIST-800-XXX, NIST CSF, CIS, COBIT, COSO, ITIL, PCI, OWASP, plus a plethora of others, plus all the regulations. Further, the majority of these frameworks are quite similar when you actually break them down, with quite some overlap, but also serious gaps otherwise.
You need to start picking one or two, and let them guide you in your efforts. Understand that you have not to religiously follow every single piece, but instead the overall subject. When you do think you have really gotten something, do an independent audit (against that framework) and you will most likely find some gaps. Fix them, next audit. Then pick up an additional one… similar. The learning curve will be steeper and you will be settled for the next round faster.
You recently released “Premier Ciso – Board & C-suite: Raising the Bar for Cybersecurity”, can you introduce the book to our audience?
This book is truly written for CISOs, and I have served this industry for 30 years in eight CISO roles. That expertise manifests itself in the breadth and depth of topics that are covered in this book. I do not only share an overview of the current industry status, but also provide information about conversations that should happen before someone takes on that role, during that time, as well as while on the job – and even how to communicate afterwards.
Further, I provide a suumarized compensation overview, before an in-depth definition, description, analysis, and guidance for the CISO skills and characteristics is shared. So far, I am not aware of any such work – plenty of companies have hired CISOs, but no one could actually tell what it means or requires to be a CISO – this book is aiming to change that. As mentioned above, I also dive deep into the most important conversations amongst the C-suite and the board that the CISO must hold to be successful.
The book then describes “the rise of the CISO“, before it guides you into the latest subjects in cybersecurity, such as quantum computing and AI. My 30 years expertise will serve well for all that either want to become a CISO or are currently a CISO and want to sharpen their saw (skills and know-how) – or for anyone in the C-suite, board, or other groups that wants to understand more about CISOs and how to work with them.