MTI Security researchers have uncovered a new, particularly advanced Android banking trojan, dubbed Sturnus, that targets users’ financial and personal data with an unprecedented level of device control and operational stealth.
Distinct from conventional mobile malware, Sturnus not only supports the typical arsenal of credential theft and whole device takeover but also demonstrates the ability to bypass the protection of encrypted messaging apps directly capturing conversations from WhatsApp, Telegram, and Signal.
What sets Sturnus apart is its strategic attack on encrypted messaging services.
Rather than attempting to break encryption protocols which remain secure in transit Sturnus leverages accessibility-based screen capture and UI event monitoring to extract content after it is decrypted and displayed by legitimate apps.
This gives attackers a real-time window into users’ private conversations, sidestepping the end-to-end encryption guarantees that users rely on for confidentiality.
Once Sturnus infects a device, it persistently monitors the foreground application. Whenever a messaging service like WhatsApp, Signal, or Telegram is opened, the malware silently activates advanced UI-tree collection and keylogging.
All message content, contacts, and even full conversation threads are siphoned off to remote attackers.
This capability undermines not just privacy but also trust in secure communication platforms any sensitive information appearing on-screen becomes accessible to threat actors.
Full-Scale Device Takeover
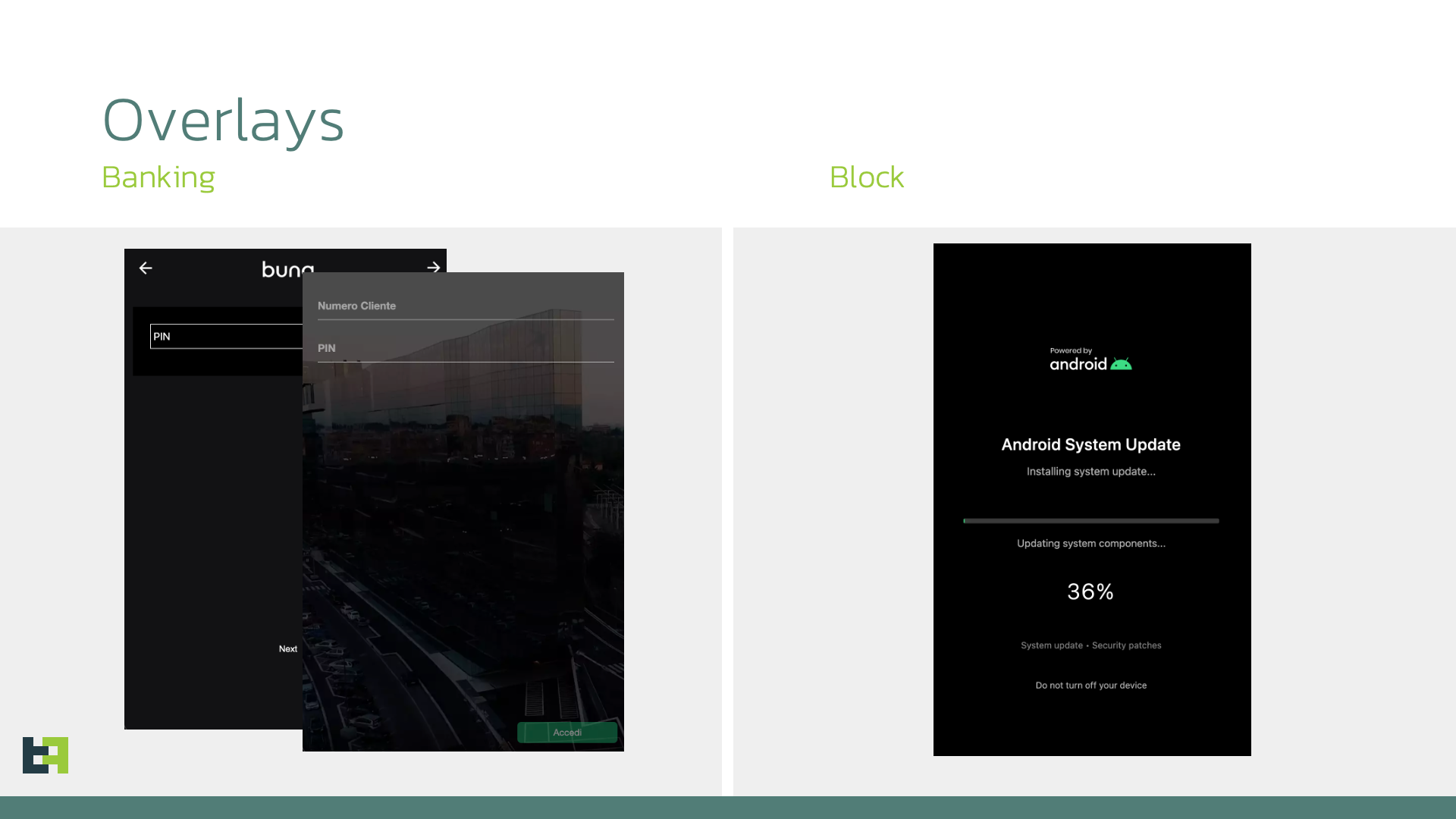
Sturnus’s capabilities extend far beyond just message monitoring. It employs convincing fake login overlays that mimic banking apps, harvesting user credentials and financial details with ease.
The exfiltration engine is driven by an HTML overlay system, deploying phishing templates tailored to targeted European institutions.
Leveraging Android’s Accessibility Service, Sturnus implements a deep keylogging and UI monitoring pipeline.
It intercepts text input, UI changes, and user interactions, allowing attackers to reconstruct user activity, steal passwords or PINs, and track everything visible on screen even if standard screen-capture methods are blocked.
Remote control is facilitated by two redundant screen streaming mechanisms: a primary display-capture framework and a secondary Accessibility-based screenshot method.
Attackers interact with the device using both pixel-based VNC sessions and a highly efficient interface mapping protocol.

Actions such as clicks, text input, swiping, app launching, and even permission granting can be executed covertly, with the option to black out the screen and conceal activity from the victim.
Communication Protocol
The name “Sturnus” reflects the malware’s unpredictable, layered communication pattern, reminiscent of the chattering starling bird.
Once credentials are captured, the malware turns off specific overlays to avoid redundant targeting and minimize suspicion.
Malware traffic shifts between plaintext and advanced encryption (RSA, AES), using a custom protocol over HTTP and WebSocket for resilient, real-time command and control.
The intricate exchange includes dynamic key generation, per-message initialization vectors, and data-wrapping that frustrates interception and analysis.
Sturnus ensures its longevity through a suite of defenses: once given Device Administrator privileges, it monitors and blocks attempts to disable its control or uninstall it, even leveraging Accessibility monitoring to evade removal.
The malware’s twelve internal receivers and constant security checks monitor system activity, network state, device integrity, and potential forensic probing, adapting as needed to evade cleanup.
While researchers note that Sturnus campaigns have so far been limited and intermittent primarily targeting financial institutions in Southern and Central Europe the depth and sophistication of its code indicate imminent potential for broader, more sustained attacks.
Threat analysts map its features to a broad segment of the MITRE ATT&CK matrix, underscoring its multi-vector approach.
Sturnus’s combination of overlay-based credential theft, encrypted messaging surveillance, comprehensive device monitoring, and robust remote-control capabilities makes it one of the most advanced mobile trojans yet observed in the wild.
Users and financial institutions in targeted regions should maintain heightened vigilance, ensure device hygiene, and scrutinize app permissions to minimize risk until further protective measures and detection strategies can be deployed.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.