The cybersecurity company Proofpoint has found a new operation using the SugarGh0st Remote Access Trojan (RAT) that is going after AI research organizations in the United States.
The operation, linked to a threat cluster known as UNK_SweetSpecter, went after businesses, universities, and government agencies.
Attack Method: Emails with AI-themed bait
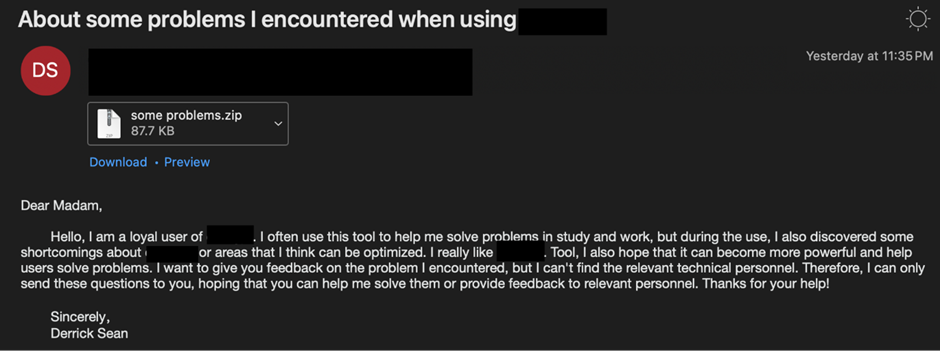
UNK_SweetSpecter’s campaign in May 2024 used a free email account to send emails with AI-themed traps to people who might be victims. These emails had a zip archive file to get people to open it.
The zip file dropped an LNK shortcut file that used a JavaScript dropper as soon as it was launched.
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
This dropper is then put in the SugarGh0st RAT code.
The attack chain was very similar to a method that Cisco Talos had already reported.
It included a fake document, an ActiveX tool for sideloading, and a base64-encrypted binary file.
The JavaScript dropper was put in a library that later let JavaScript run a multi-stage shellcode, which was what released the SugarGh0st payload.
This payload was meant for data exfiltration, command and control (C2) heartbeat protocol, and keylogging.
Analysis of Networks and Attribution
Proofpoint’s study of the network showed that UNK_SweetSpecter had moved its C2 communications to new domains, such as accounts. gommask[.]online, which shared hosting with domains that had already been reported.
It looks like AS142032 is where the infrastructure for these activities is located.
Cisco Talos’s first look at SugarGh0st RAT suggested that it was used by threat actors who spoke Chinese.
Proofpoint’s study of earlier UNK_SweetSpecter campaigns proved these mistakes in the language.
Proofpoint isn’t sure the campaigns were directed at a specific state goal.
Still, the fact that they were very specific and focused on AI experts suggests that the government might have been trying to get private information about generative AI.
A recent Reuters story said that the U.S. government is stepping up its efforts to prevent China from using generative AI.
This campaign is happening simultaneously, which makes it more likely that cybercriminals with ties to China will target people who have access to AI technologies to help them reach their growth goals.
Why it’s important
Enterprise defenders must monitor specific threat actors, which is difficult but necessary.
This campaign shows how important it is to set baselines to detect malicious behavior, even if the threat isn’t currently part of an organization’s threat model.
The fact that common tools are used as the first step in highly targeted spearphishing campaigns shows how important it is to be careful and have strong cybersecurity means in place.
The Yahoo! Paranoids Advanced Cyber Threats Team and Proofpoint’s collaboration was very helpful in locating this operation.
As cyber threats change, partnerships like these and thorough threat research will continue to be essential for protecting against complex attacks.
Indicators of compromise
| Indicator | Description | First Observed |
| da749785033087ca5d47ee65aef2818d4ed81ef217bfd4bc07be2d0bf105b1bf | SHA256 some problems.zip |
2024-05-08 |
| 71f5ce42714289658200739ce0bbe439f6ef6fe77a5f6757b1cf21200fc59af7 | SHA256 some problems.lnk |
2024-05-08 |
| fc779f02a40948568321d7f11b5432676e2be65f037acfed344b36cc3dac16fc | SHA2256 ~235232302.js |
2024-05-08 |
| 4ef3a6703abc6b2b8e2cac3031c1e5b86fe8b377fde92737349ee52bd2604379 | SHA256 libeay32.dll |
2022-02-18 |
| feae7b2b79c533a522343ac9e1aa7f8a2cdf38691fbd333537cb15dd2ee9397e | SHA256 some_problems.docx |
2024-05-08 |
| account.gommask[.]online | SugarGh0st RAT C2 Domain | 2024-05-08 |
| 43.242.203[.]115 | SugarGh0st RAT C2 IP | 2024-05-08 |
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
