Notepad++, a widely used text editor among developers, became the target of a sophisticated supply chain attack that compromised its update infrastructure for nearly 6 months.
On February 2, 2026, the developers published a statement revealing that attackers gained control of the update mechanism due to a hosting provider-level incident occurring from June to September 2025.
Despite remediation efforts, threat actors maintained access to internal services until December 2025, enabling continued malicious activity.
Between July and October 2025, attackers constantly rotated command-and-control server addresses, downloaders, and final payloads, demonstrating advanced operational security.
Kaspersky researchers analyzing telemetry data discovered an unprecedented variety of execution chains deployed throughout the attack campaign.
Three distinct infection chains were identified, targeting approximately a dozen machines belonging to individuals in Vietnam, El Salvador, and Australia, plus organizations including a government entity in the Philippines, a financial institution in El Salvador, and an IT service provider in Vietnam.
Chain #1: Late July and Early August 2025
The first malicious Notepad++ update appeared in late July 2025, hosted at hxxp://45.76.155[.]202/update/update[.]exe.
The downloaded file functioned as an NSIS installer that sent heartbeat signals containing system information to attackers.
This was accomplished by creating a directory at %appdata%ProShow, executing shell commands to collect system data, and uploading results to the temp[.]sh hosting service via curl commands.
After transmitting system information, the installer dropped multiple files, including ProShow.exe, a legitimate application that was subsequently abused to launch malicious payloads.
Rather than using the common DLL sideloading technique, attackers exploited an old ProShow software vulnerability dating to the early 2010s.
The exploit contained two shellcodes one serving as padding to confuse analysis systems, and another that decrypted a Metasploit downloader payload.
This downloader retrieved a Cobalt Strike Beacon shellcode designed to communicate with the CDNCheck.]com C2 server.
Chain #2: September 2025
Following a six-week pause, attackers resumed operations in mid-September 2025 with a modified infection chain.
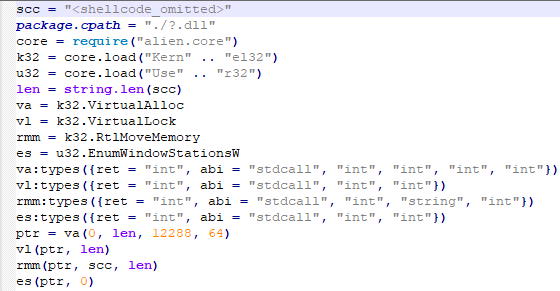
While still distributed from the same URL, the new NSIS installer was significantly smaller at 140 KB.
The revised approach changed system information collection to include more details through an expanded shell command capturing whoami, tasklist, systeminfo, and netstat data.
The next-stage payload was completely redesigned, dropping files related to the Lua interpreter to the %APPDATA%AdobeScripts directory.
Attackers launched a compiled Lua script that placed shellcode into executable memory and triggered it through the EnumWindowStationsW API function.
This shellcode again functioned as a Metasploit downloader retrieving Cobalt Strike Beacon from the cdncheck.it[.]com domain.
Chain #3: October 2025
October 2025 brought another complete overhaul, with the malicious update now hosted at hxxp://45.32.144[.]255/update/update[.]exe.
This variant dropped files to the %appdata%Bluetooth directory and relied on DLL sideloading to launch encrypted shellcode, an execution pattern commonly associated with Chinese-speaking threat actors.
The final payload was identified as the Chrysalis backdoor, a custom implant designed for espionage operations.
The attackers’ monthly rotation of infrastructure and techniques made detection challenging. Kaspersky recommends organizations hunt for NSIS installer deployments, monitor for temp[.]sh DNS resolutions, check for suspicious shell command sequences, and review network traffic for known indicators of compromise.
All three infection chains were successfully blocked by Kaspersky security solutions as attacks occurred.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




