A supply chain attack on the widely used ‘tj-actions/changed-files’ GitHub Action, used by 23,000 repositories, potentially allowed threat actors to steal CI/CD secrets from GitHub Actions build logs.
The GitHub Action is a very popular automation tool designed for GitHub Actions workflows. It allows developers to identify files changed in a pull request or commit and take actions based on those changes, generally used in testing, workflow triggering, and automated code linting and validation.
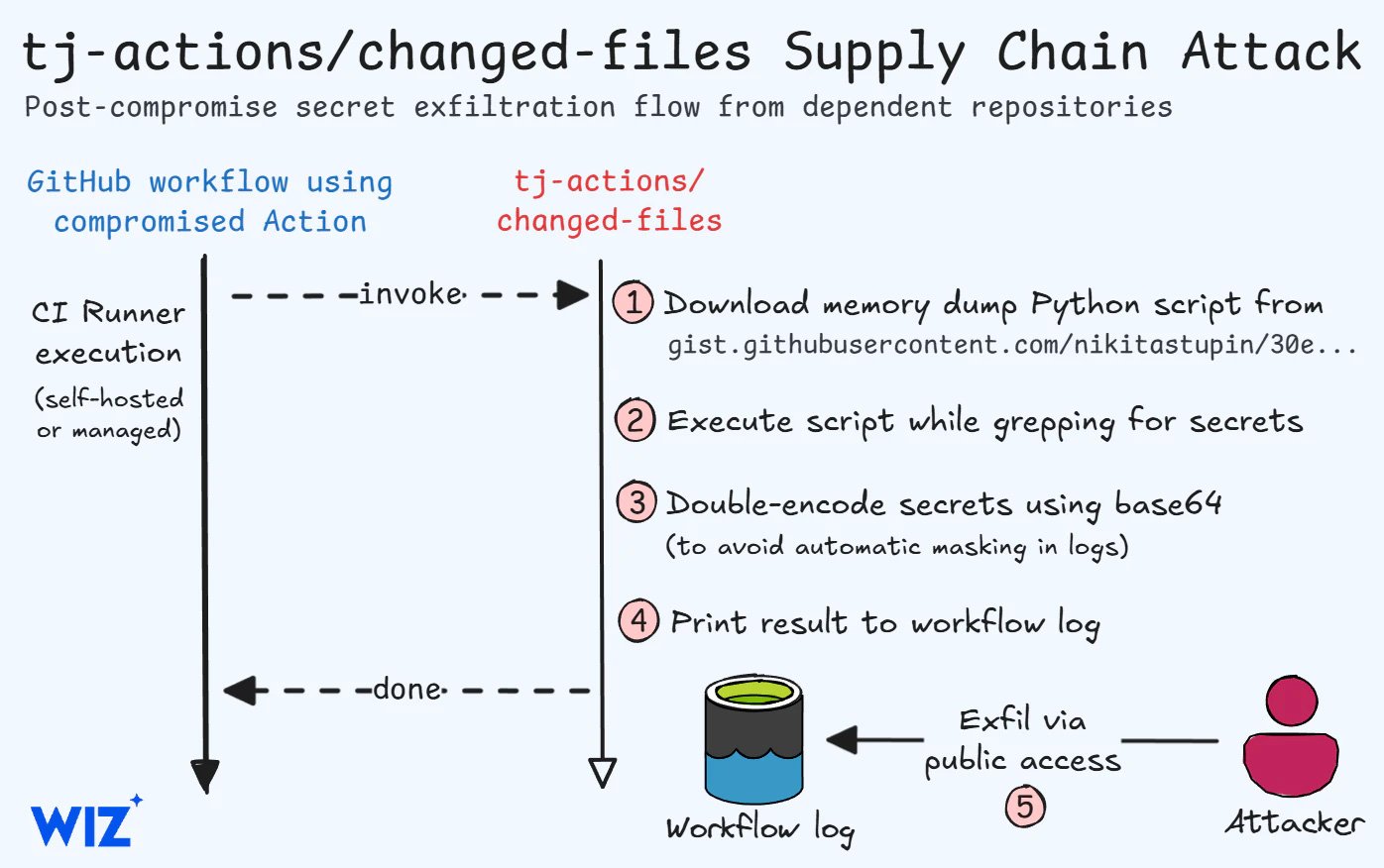
As first reported by StepSecurity, attackers added a malicious commit to the tool on March 14, 2025, at 4:00 PM UTC, that dumped CI/CD secrets from the Runner Worker process to the repository of any projects using the action. As a result, if workflow logs were publicly accessible, anyone could read and steal exposed secrets.
Attackers modified the action’s code and retroactively updated multiple version tags to reference a malicious commit, so all versions of the tool were compromised.
As per the latest update by the developers, the attacker compromised a GitHub personal access token (PAT) used by a bot (@tj-actions-bot), which had privileged access to the tool’s repository. However, it is currently unclear how exactly the PAT was compromised.
On March 15, 2:00 PM UTC, GitHub removed the compromised action, and at 10:00 PM UTC on the same day, the repository was restored with the malicious code having been removed.
However, the compromise has lasting repercussions for impacted software projects, so a CVE ID (CVE-2025-30066) was assigned to the incident for tracking.
Strangely, the malicious code did not exfiltrate the memory output to a remote server, instead only making it visible in publicly accessible repositories.
“The compromised action injected malicious code into any CI workflows using it, dumping the CI runner memory containing the workflow secrets,” explains Wiz in a write-up on the incident.
“On public repositories, the secrets would then be visible to everyone as part of the workflow logs, though obfuscated as a double-encoded base64 payload.”
Source: Wiz
The restored tj-actions repository was updated earlier today to include instructions on what potentially impacted users need to do, which include:
- Rotate any secrets used during the attack’s timeframe (March 14-15)
- Review Workflows to unexpected output under the ‘changed-files’ section
- If your workflows reference the compromised commit by SHA, update them immediately.
- Make sure you are now using a tagged version (e.g., v35, v44.5.1)
To prevent secrets from being exposed to similar compromises in the future, it is GitHub recommends that all GitHub Actions be pinged to specific commit hashes instead of version tags.
Also, GitHub offers allow-listing functionality that can be leveraged to block unauthorized/non-trusted GitHub Actions.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
