A sophisticated supply chain attack targeting cryptocurrency developers through the compromise of ETHcode, a legitimate Visual Studio Code extension with nearly 6,000 installations.
The attack, executed through a malicious GitHub pull request, demonstrates how threat actors can weaponize trusted development tools using minimal code changes, raising serious concerns about open-source software security in the blockchain ecosystem.
The compromise began on June 17, 2024, when a newly created GitHub account named Airez299 submitted a pull request to the ETHcode repository with the seemingly benign message “Modernize codebase with viem integration and testing framework.”
The timing was strategic, as the extension had been dormant for over six months since its last update in September 2024, making the apparent maintenance contribution appear legitimate and valuable.
ETHcode, developed by the 7finney organization, serves as a crucial development tool for Ethereum smart contract developers, providing testing, debugging, and deployment capabilities across EVM-based blockchains.
The extension’s legitimate status and active user base made it an attractive target for cybercriminals seeking to infiltrate the cryptocurrency development community.
The pull request contained 43 commits with approximately 4,000 lines of code changes, creating a substantial review burden that helped obscure the malicious elements.
Both human reviewers from the 7finney organization and GitHub’s Copilot AI reviewer examined the code, requesting minor changes but failing to detect the embedded threats.
This review process highlighted the challenges of identifying sophisticated supply chain attacks within legitimate-looking code contributions.
Supply Chain Attack
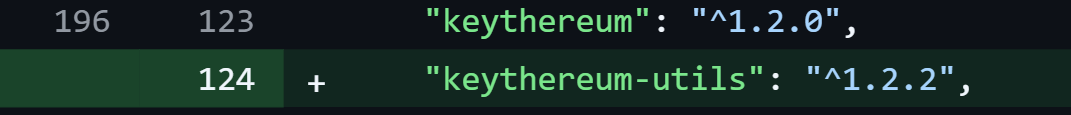
The entire compromise hinged on just two strategically placed lines of code. The first line introduced a new dependency called “keythereum-utils,” carefully named to mimic the existing “keythereum” package with an added “-utils” suffix.
This naming convention was designed to appear as a legitimate helper library, avoiding suspicion during code reviews.
The second malicious line invoked Node.js “require” function to load and execute the newly introduced dependency.
This simple call activated the malicious payload, demonstrating how minimal code changes can have devastating consequences in software supply chains.
When researchers analyzed the keythereum-utils package, they discovered heavily obfuscated JavaScript code.
After deobfuscation, the code revealed its true purpose: spawning a hidden PowerShell process that downloads and executes a batch script from a public file-hosting service.
ReversingLabs recommends implementing stricter review processes for new dependencies and utilizing security tools like Spectra Assure to detect anomalous behavior in software packages.

While the complete functionality of the second-stage payload remains under investigation, researchers suspect it targets cryptocurrency assets or compromises Ethereum smart contracts under development.
Security Vulnerabilities
The attack’s success was amplified by Visual Studio Code’s automatic extension update feature, which is enabled by default for most users.
This mechanism potentially distributed the malicious code to thousands of developer systems without user awareness or intervention, significantly expanding the attack’s reach and impact.
According to Report, Microsoft’s Visual Studio Marketplace removed the compromised extension on June 26, 2024, while the original developers at 7finney released a clean version (0.5.1) on July 1st.
However, the incident exposed critical vulnerabilities in the open-source development ecosystem, particularly affecting cryptocurrency developers who represent high-value targets for cybercriminals.
The attack underscores the importance of rigorous dependency management, contributor verification, and automated security scanning in modern software development.
ReversingLabs recommends implementing stricter review processes for new dependencies and utilizing security tools like Spectra Assure to detect anomalous behavior in software packages.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.
