Cybersecurity researchers have observed a significant uptick in phishing campaigns that leverage domains designed to impersonate Microsoft SharePoint, employing highly structured naming conventions to evade detection.
These malicious domains, which have proliferated since June 26, 2025, follow predictable patterns, including a fixed 29-character prefix in the third-level domain, variations in numeric segments, and a consistent “-mysharepoint” suffix, all under the .org top-level domain.
For instance, domains such as 9yusq7ngwdm365cj87v39gs5do8we-mysharepoint.tahofire[.]org and 2yusq7ngwdm835cj87v63gs5do8we-mysharepoint.fencecorps[.]org mimic legitimate U.S.-based organizations like tahoelivingwithfire.com and fencecorp.us, blending alphanumeric strings with organizational names to appear authentic.
This structured approach not only facilitates mass generation of deceptive domains but also enables threat actors to target users with phishing lures that exploit trust in familiar platforms.
Emerging Patterns in Domain Spoofing
Analysis of public sandbox data reveals over 40 associated sessions, with domain appearances and related tasks surging noticeably through July 9, 2025, indicating a coordinated and persistent campaign.
The invariant elements in these domains such as the recurring string “yusq7ngwdm” followed by variable digits and “cj87v” patterns provide key indicators for proactive threat hunting, allowing security teams to craft targeted queries like domainName:”?yusq7ngwdm??5cj87v??gs5do8we-mysharepoint.*.org” in threat intelligence lookup tools to identify and mitigate emerging threats.
Compounding the issue is the rampant exploitation of legitimate hosting services, particularly Alboompro.com, a platform for creating online portfolios that allows user-defined subdomains.
Threat actors have increasingly abused this feature to host phishing content, with over 250 sandbox tasks and 130 subdomains linked to alboompro.com since May 2025 exhibiting malicious indicators.
Abuse of Hosting Platforms
In a typical case analyzed via the ANY.RUN sandbox (task ID: 6f152a2b-b8de-4156-9970-2cf77e36f6df), a phishing email impersonates a U.S. company like midwesthose.com, directing victims to a spoofed subdomain such as midwesthose-specialty[.]alboompro.com.
This lure prompts users to access a purportedly protected PDF, redirecting them to a domain like 2yusq7ngwdm385cj87v68gs5do8we-mysharepoint.capernos[.]org, where a CAPTCHA challenge precedes a credential-harvesting page.
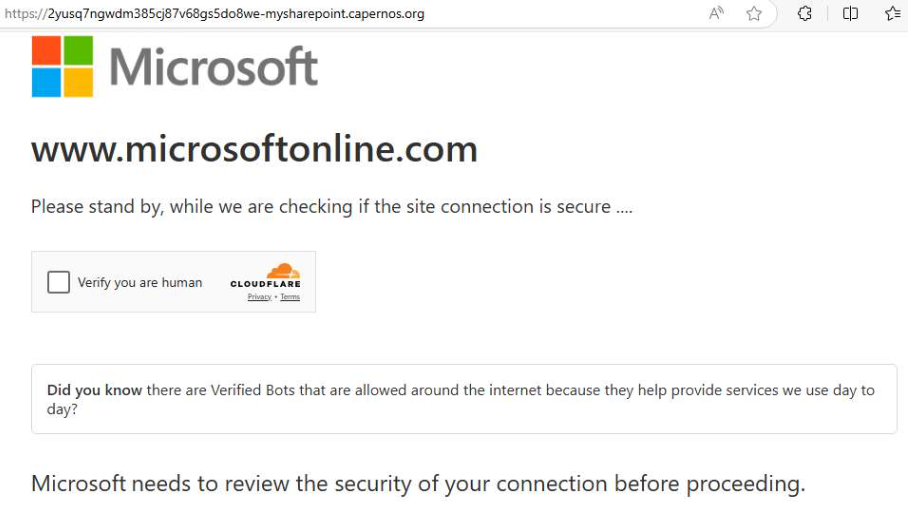
Classified as a Sneaky2FA attack, this tactic proxies the legitimate Microsoft login interface through an attacker-controlled server, intercepting credentials while maintaining an authentic appearance to bypass user suspicion and two-factor authentication prompts.
Such methods underscore the sophistication of these campaigns, where victims unwittingly interact with official content funneled via malicious infrastructure, enabling real-time credential theft.
Queries like domainName:”*.alboompro.com” in threat intelligence platforms have uncovered widespread abuse, highlighting how attackers repurpose benign services for scalable phishing operations.
This surge in spoofed SharePoint domains and Alboompro exploitation reflects evolving phishing tactics that demand enhanced monitoring of domain patterns and service misuse.
Security practitioners are urged to integrate these indicators into detection workflows, leveraging threat intelligence lookups to preemptively address the growing volume of such attacks, which continue to target organizational credentials with increasing frequency and technical finesse.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!




