A suspected cyber criminal believed to have extorted companies under the name “DESORDEN Group” or “ALTDOS” has been arrested in Thailand for leaking the stolen data of over 90 organizations worldwide.
The suspect was arrested in Bangkok through a law enforcement operation by the Royal Thai Police and the Singapore Police Force, with the help of experts from Group-IB.
The cybercriminal, who operated since 2020 under multiple aliases such as ALTDOS, DESORDEN, GHOSTR, and 0mid16B, stole and leaked/sold over 13TB of personal data from the organizations.
Group-IB says the hacker was “one of the most active cybercriminals in the Asia-Pacific since 2021,” targeting entities primarily in Thailand, Singapore, Malaysia, Indonesia, and India.
The cybercriminal also impacted companies in Europe and North America, with 20 data leaks concerning organizations in those regions.
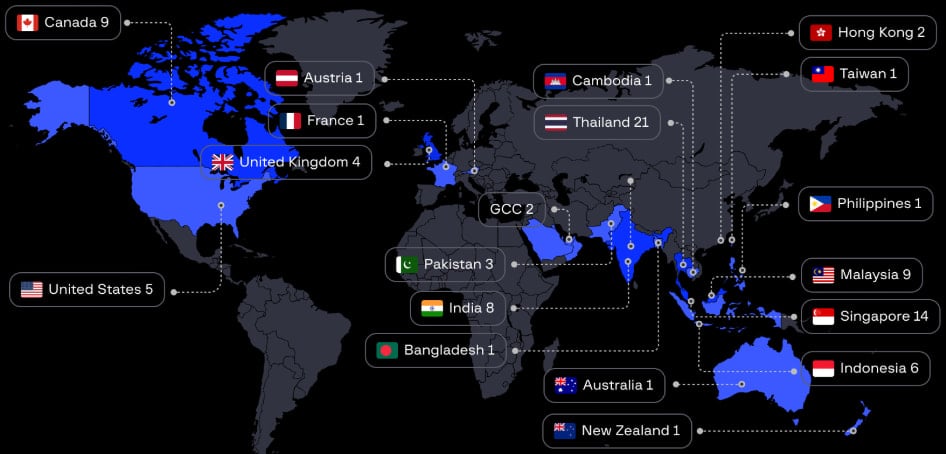
Source: Group-IB
The cybersecurity firm noted that the threat actor was particularly evasive, and his practice of switching to new aliases and online personas so often complicated investigations and delayed his tracking down.
Group-IB says the hacker’s modus operandi was heavily focused on high-level blackmail, often contacting the press for maximum pressure on the victims.
“The main goal of his attacks was to exfiltrate the compromised databases containing personal data and to demand payment for not disclosing it to the public,” reads the Group-IB press release.
“If the victim refused to pay, he did not announce the leaks on dark web forums. Instead, he notified the media or personal data protection regulators, with the aim of inflicting greater reputational and financial damage on his victims.”
The hacker also resorted to emailing his victims’ customers and, in rare cases, even encrypted the compromised firm’s databases.
One notable case from when the hacker operated under the ‘Desorden’ persona is the hack and data theft on Taiwanese computer giant Acer.
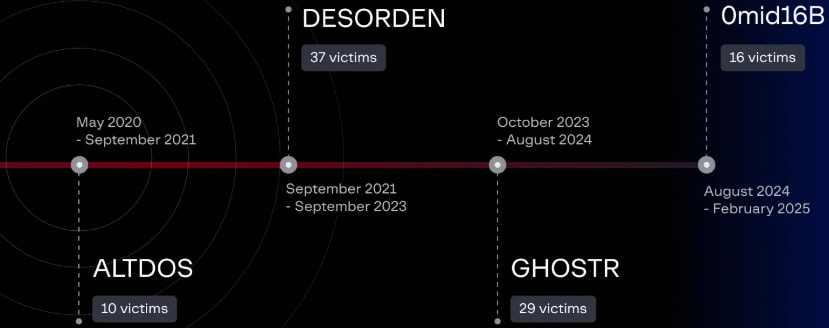
Source: Group-IB
To breach corporate networks, the cybercriminal used ‘sqlmap’ for SQL injection attacks and exploited vulnerable Remote Desktop Protocol (RDP) servers to drop CobaltStrike beacons in the victim’s environment.
CobaltStrike is a legitimate but broadly abused penetration testing suite, with cracked versions used by cybercriminals to conduct malicious activities in breached environments.
Despite the large number of breaches, Group-IB says the hacker did not perform significant lateral movement, instead focusing on quick data exfiltration onto cloud servers and victim extortion.
The Thai Police’s raid on the hacker’s premises resulted in the confiscation of multiple items, including laptops and luxury goods believed to have been purchased with cybercrime proceeds.

Source: Group-IB
Thai news outlet The Nation reports that the suspect is a 39-year-old man named Chia, who was arrested yesterday in Bangkok.
According to the same outlet, Chia has already admitted his guilt, claiming that he worked alone, selling stolen data to buyers for $10,000.
The suspect now faces multiple charges, including unauthorized access to protected computer systems and data, attempted extortion, and illegal residence.
