A sophisticated, multi-stage espionage campaign targeting Indian residents through phishing emails impersonating the Income Tax Department.
The attack chain, tracked as the “SyncFuture Espionage Campaign,” weaponizes legitimate enterprise security software as its final payload, demonstrating how threat actors repurpose trusted commercial tools to establish persistent, undetectable access to victim systems.
The campaign begins with targeted phishing emails disguised as tax penalty notices, using URL shorteners to redirect victims to malicious archives hosted on the attacker’s infrastructure.
The initial infection leverages DLL side-loading a technique where legitimate, signed Microsoft applications load malicious payloads to evade detection.
The first-stage loader incorporates sophisticated anti-debugging checks, including process environment block (PEB) manipulation, API hooking detection, and timing-based sandbox evasion mechanisms.
Upon passing these defenses, the malware establishes communication with Command-and-Control servers to download a packed shellcode.
The eSentire Threat Response Unit (TRU) identified an ongoing campaign deploying a sophisticated, multi-stage backdoor for the likely purpose of long-term espionage.
This second stage executes a dual-pronged attack: it bypasses Windows User Account Control (UAC) using a COM-based elevation technique and modifies its process properties to masquerade as the legitimate Windows explorer.exe application, effectively hiding from endpoint monitoring tools.
A striking feature of this campaign is its targeted evasion of Avast Free Antivirus. When Avast is detected, the malware deploys Blackmoona banking trojan variant that uses automated mouse simulation to navigate Avast’s GUI and add malicious files to the antivirus exclusion list.
This hands-off automation demonstrates the attackers’ technical sophistication and understanding of security software interfaces.
The infection progresses through subsequent stages that establish persistent access via custom batch scripts and Windows services configured to survive Safe Mode reboots.
The final payload, however, is where this campaign becomes exceptional: instead of a generic backdoor, threat actors deploy SyncFuture TSM (Terminal Security Management System), a commercial data security product developed by China-based Nanjing Zhongke Huasai Technology Co., Ltd.
Analysis of dropped files reveals the attackers’ meticulous attention to operational security. Multiple executables carry valid code-signing certificates spanning 2019-2024, suggesting abuse of legitimate software distribution channels.
SyncFuture TSM is marketed as a legitimate enterprise solution with Remote Monitoring and Management capabilities.
Data theft and lateral movement
Yet in this campaign, it serves as an all-in-one espionage framework. The deployed system includes transparent data encryption capabilities, extensive surveillance features that log file operations and website visits, screen recording functionality, and remote control mechanisms that grant operators complete desktop access.
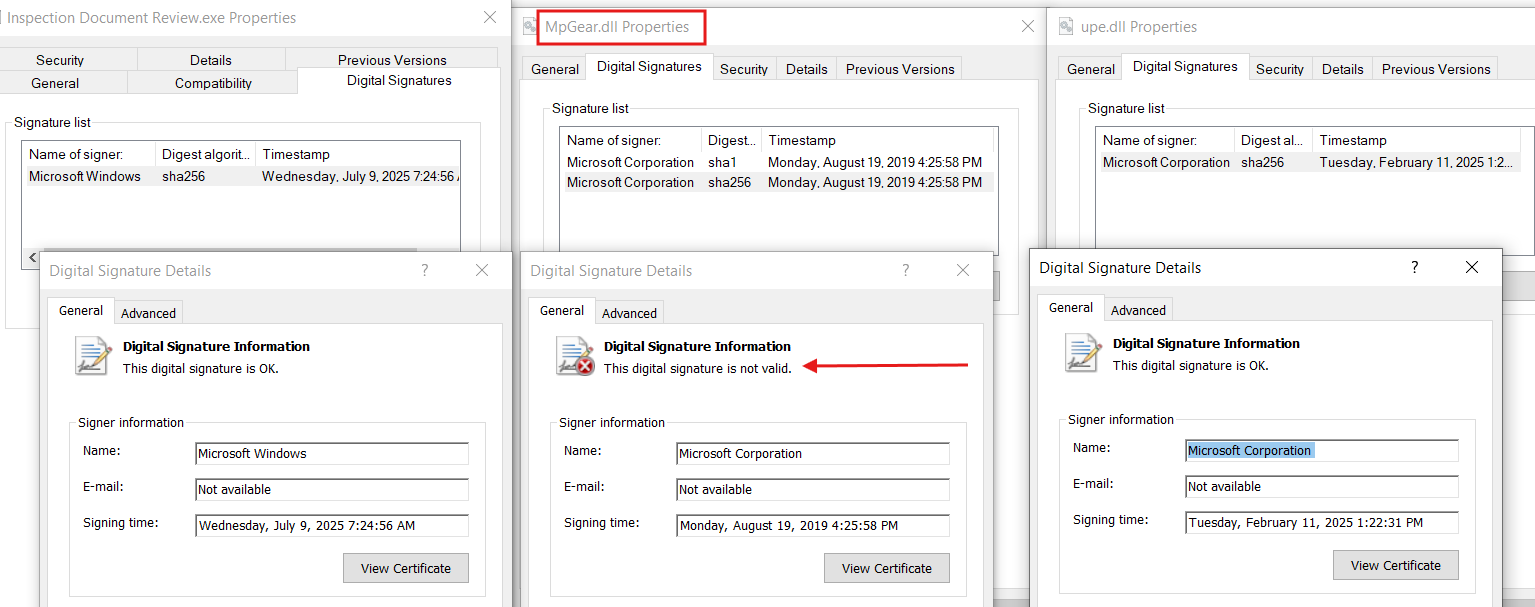
MpGear.dll revealed that the threat actors likely employed specialized tools to clone a legitimate Microsoft binary’s digital signature into MpGear.dll.
Organizations should prioritize EDR deployment, security awareness training focused on phishing, and strict policies against unauthorized third-party software to defend against similar campaigns.
This transformation of enterprise security software into an espionage tool represents the culmination of a multi-stage intrusion designed for long-term surveillance rather than quick financial gain.
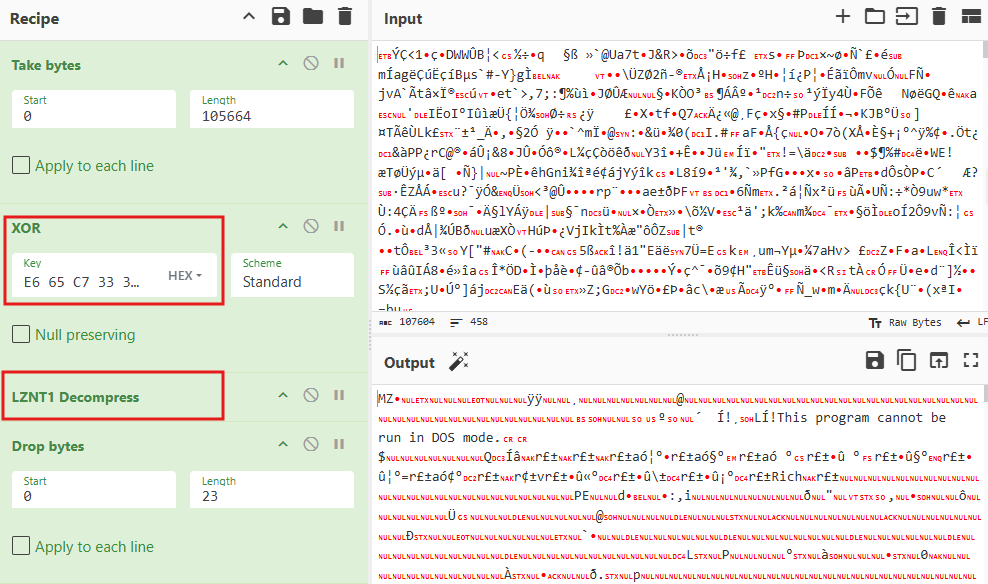
The data that results from the XOR decryption is not the final executable, but rather a compressed data blob that is decompressed using the RtlDecompressBuffer API.
Kernel-mode drivers signed by “Nanjing Yangtu Information Technology Co., Ltd.” indicate deep integration with system-level access.
Supporting batch scripts manipulate system Access Control Lists to weaken security, enable Windows Test Mode to load unsigned drivers, and establish directories with elevated permissions for sustained malware operations.
This campaign demonstrates advanced persistent threat characteristics consistent with state-sponsored activity.
By exploiting legitimate enterprise software, evading antivirus detection through automated GUI interaction, and establishing multi-layered persistence mechanisms, the threat actors have created an intrusion framework capable of sustained espionage.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
