As cybercrime continues to evolve, new adversaries and innovative tactics challenge defenders daily. The recently emerged threat group TA585 exemplifies this shift, deploying sophisticated malware campaigns that highlight the changing nature of the cybercrime landscape.
TA585’s operational strategy, infrastructure control, and malware preferences set it apart—particularly in its use of the advanced MonsterV2 malware.
TA585 distinguishes itself by managing each stage of its attack chain in-house. Instead of relying on established cybercrime services such as traffic distribution networks or initial access brokers, the group controls its own infrastructure for delivering malware like MonsterV2—a recently surfaced remote access trojan (RAT), stealer, and loader.
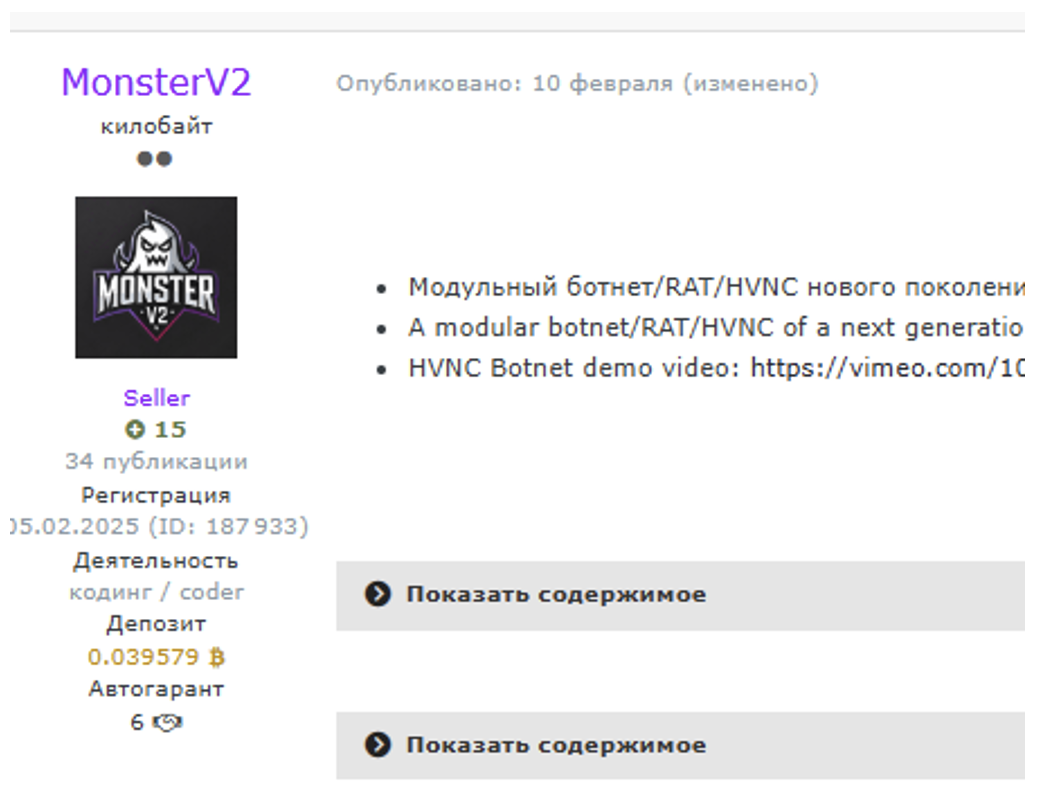
MonsterV2 first appeared in cybercriminal forums in February 2025 and quickly gained notoriety for its high cost and feature-rich toolset that appeals to well-resourced actors.
MonsterV2, sold primarily as a malware-as-a-service (MaaS) offering, stands out with its ability to exfiltrate sensitive data, provide remote desktop access (HVNC), execute arbitrary commands, and operate as both a loader and info-stealer.
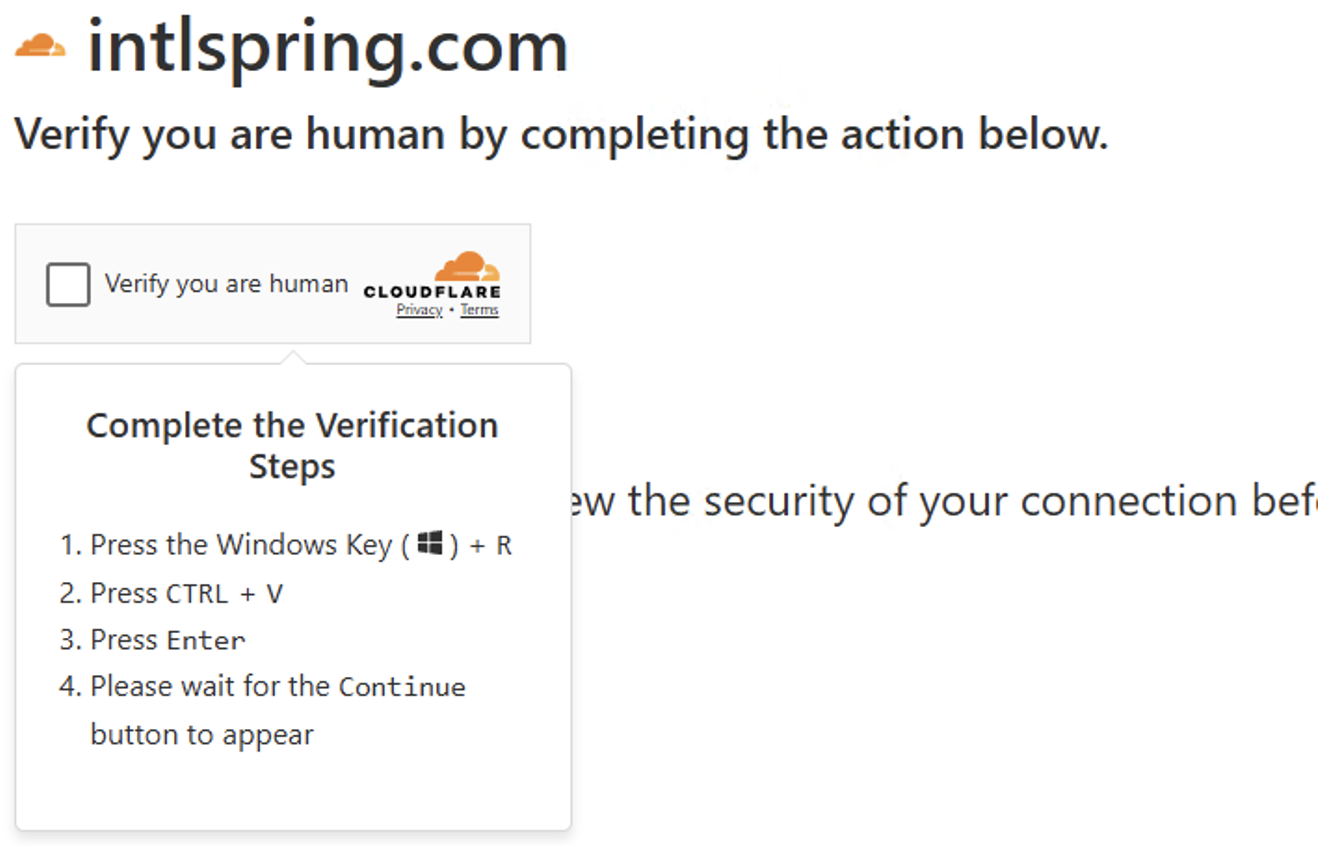
“Win+R” activity from the user with an actual “reaction” from the website upon completing it. Once the user clicks the “Verify you are human” they are prompted to complete the “Win+R” action.
Unlike some malware families that rely on mass distribution, MonsterV2’s use in the wild remains selective due to its steep price, reportedly $800 per month for the standard tier and up to $2,000 for enterprise capabilities—including loader, stealer, and advanced control modules.
Campaign Tactics
First observed by Proofpoint in February 2025, TA585 turned heads with government-themed phishing campaigns.
Targeted emails mimicked U.S. Internal Revenue Service and Small Business Administration notifications, enticing victims to open links to PDFs.
These PDFs led to booby-trapped web pages employing the so-called ClickFix technique—a novel luring method that prompts users to manually execute a PowerShell command via the Windows Run dialog or terminal.

Such techniques bypass many traditional antivirus detections by involving the victim in the infection process.
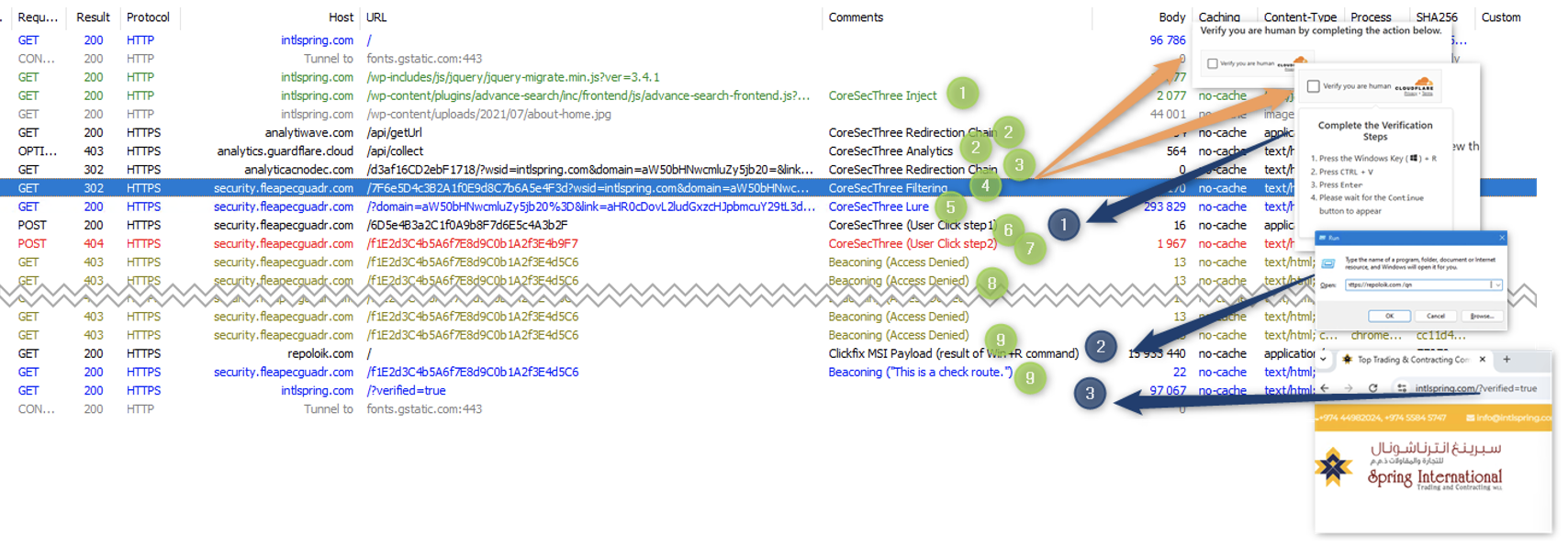
In April and May 2025, TA585 scaled operations with unique JavaScript web injects on legitimate but compromised websites. Instead of redirecting all visitors, the injected code selectively targeted victims, displaying a convincing fake CAPTCHA that instructs users to verify their identity by running a PowerShell script.
This script, when executed, fetched and installed the MonsterV2 payload on the user’s Windows machine.
Unlike campaigns that outsource visitor screening or rely on multi-layered affiliate networks, TA585 performs all filtering and payload delivery internally—the attacker’s infrastructure checks that a real person is present, not a bot or security researcher, before delivering malware.
Further campaigns of TA585 involved leveraging GitHub notifications as a delivery vector. Here, users received genuine-looking alerts triggered by the attackers tagging them in issues or security warnings with malicious links.
MonsterV2 Deep Dive
MonsterV2 boasts thorough system reconnaissance, privilege escalation attempts, data exfiltration options, and secondary payload delivery.

These phishing chains also led to payload sites with the same filtering and CAPTCHA trick, ultimately delivering MonsterV2 or its sibling, Rhadamanthys.
It collects operating system details, user and device information, IP data, and more, encoded and securely transmitted to its command-and-control (C2) infrastructure.
Proofpoint has observed that MonsterV2 is actively being maintained and updated, even with minor and “cosmetic” updates.
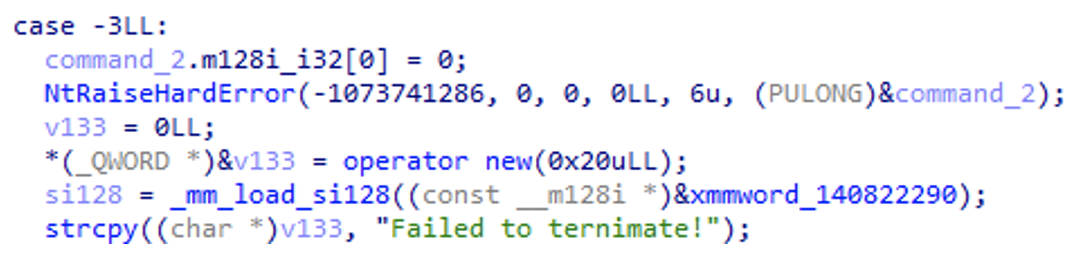

Communication and configuration files are encrypted using the ChaCha20 algorithm, followed by ZLib compression—making detection and analysis challenging.
Notably, MonsterV2 avoids infecting endpoints in several CIS countries, uses anti-debug and anti-sandbox checks, and manages persistence on compromised hosts through autorun and mutex creation.
The malware’s active maintenance and update cycle indicate a committed development team catering to sophisticated threat actors.
To counter this threat, Proofpoint advises organizations to educate users about the ClickFix technique and to restrict non-administrative PowerShell use on Windows systems.
TA585’s hands-on approach, combining precision targeting, advanced payloads, and total control of its delivery ecosystem, underscores the need for vigilant monitoring and adaptive defense in today’s cyber threat environment.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
