The commodity infostealer landscape has a new entrant in Raven Stealer, a compact Delphi/C++ binary that hijacks Telegram’s bot API to spirit away victims’ browser secrets.
First seen in mid-July 2025 on a GitHub repository operated by the self-styled ZeroTrace Team, Raven arrives either packed as a UPX-compressed executable or bundled inside renamed attachments such as “invoice.3mf.exe”.
Once executed, the payload runs headlessly, never presenting a console window, and immediately prepares the ground for covert exfiltration.
Attack chains observed in the wild rely on convincing social-engineering lures that funnel targets to GitHub releases or direct Telegram messages containing the builder’s output.
Within seconds of execution, the stub enumerates installed Chromium-based browsers, decrypts saved passwords and cookies, and scoops cryptocurrency wallets and autofill data into a tidy folder hierarchy.
Cyfirma analysts noted the stealer’s disciplined directory structure—%Local%\RavenStealer\Chrome, Edge, and Crypto Wallets—which simplifies post-infection triage for threat actors.
The ramifications are severe: a single infection yields domain credentials, payment card details, and persistent session cookies that bypass MFA.
Compounding the threat, exfiltration leverages Telegram’s /sendDocument endpoint, allowing operators to receive ZIP archives over an encrypted channel that most corporate firewalls permit by default.
.webp)
This dashboard shows Raven’s resulting archive, whose filename embeds the victim’s username for effortless cataloguing.
Infection Mechanism: Reflective Process Hollowing inside Chromium
Raven’s most striking trick lies in its in-memory DLL injection chain. After unpacking itself (entropy >7 confirms UPX), the dropper decrypts an embedded DLL stored under resource ID 101 and harvests the Telegram bot_token and chat_id from resources 102 and 103.
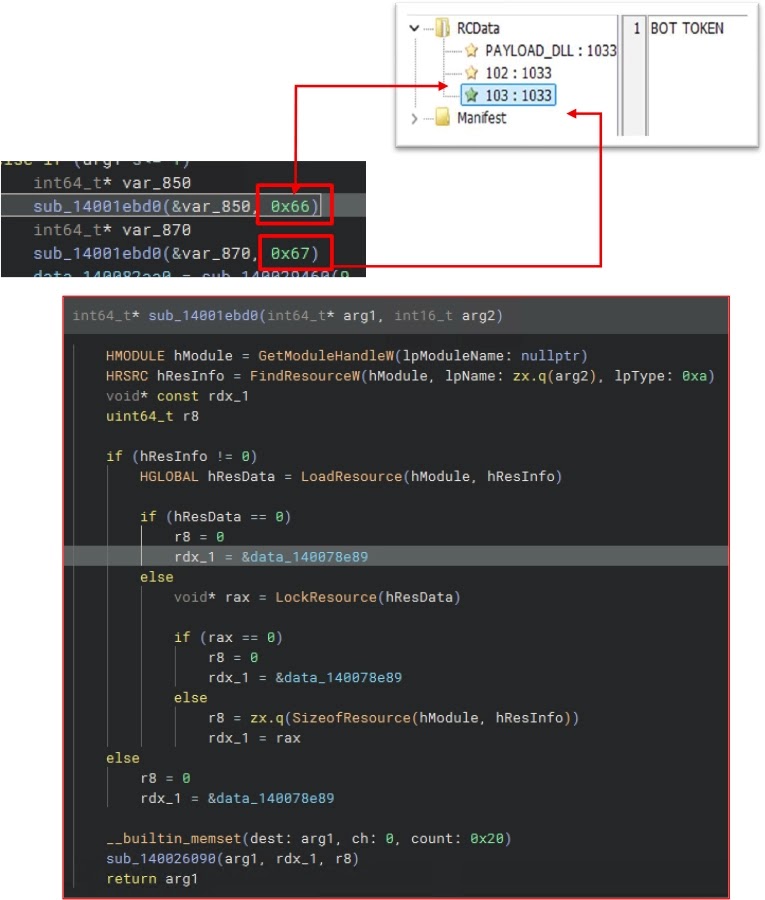.webp)
It then spawns chrome.exe in a suspended state with --headless --disable-gpu --no-sandbox, allocates memory via NtAllocateVirtualMemory, and maps the DLL into the new process—bypassing user-land hooks and hiding behind the browser’s legitimate signature.
A fragment of the resource-extraction routine illustrates Raven’s low-level style:-
HRSRC hRes = FindResourceW(NULL, MAKEINTRESOURCE(102), RT_RCDATA);
DWORD sz = SizeofResource(NULL, hRes);
BYTE* pBuf = (BYTE*)LockResource(LoadResource(NULL, hRes));
// pBuf now holds the Telegram bot token in plain textOnce collection finishes, PowerShell compresses %Local%\RavenStealer into %TEMP%\_RavenStealer.zip, and curl.exe pushes the file to https://api.telegram.org/bot/sendDocument.
A minimal YARA rule released by Cyfirma pinpoints the threat by matching strings such as “passwords.txt”, “api.telegram.org”, and the SHA-256 hash 28d6fbbd...55 embedded in older builds:-
$s1 = "api.telegram.org" nocase
$s2 = "%Local%\RavenStealer\Chrome" nocase
condition: 3 of ($s*)By intertwining stealth packing, syscall-level injection, and Telegram C2, Raven Stealer underscores how little expertise is now required to mount high-yield credential-theft campaigns.
Experience faster, more accurate phishing detection and enhanced protection for your business with real-time sandbox analysis-> Try ANY.RUN now
