Security researchers at Doctor Web have uncovered a sophisticated Android backdoor disguised as Telegram X that grants cybercriminals complete control over victims’ accounts and devices.
The malware, identified as Android.Backdoor.Baohuo.1.origin, has already infected more than 58,000 devices worldwide, with approximately 20,000 active infections currently being monitored.
This threat represents a significant escalation in mobile malware capabilities, introducing unprecedented control mechanisms through Redis database integration—a technique never before documented in Android threats.
The backdoor spreads primarily through malicious websites disguised as app catalogs, where users are lured by fake advertisements promising dating and video chat functionality.
Around 3,000 different models of smartphones, tablets, TV box sets, and even cars with Android-based on-board computers have been infected.
Victims encounter these deceptive banners in legitimate mobile applications, which redirect them to fraudulent sites mimicking official app stores.
The malicious websites prominently feature testimonials from supposed satisfied users discussing easy partner finding and communication features, complete with fabricated screenshots of video calling interfaces.
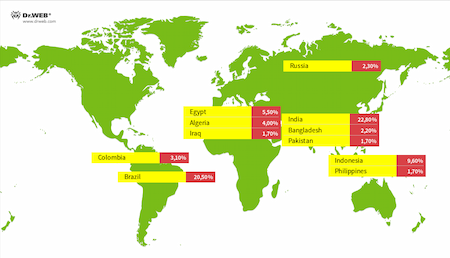
Doctor Web’s analysis reveals that cybercriminals have tailored their attack specifically for Brazilian and Indonesian markets, with malicious templates available only in Portuguese and Indonesian languages.
However, researchers warn that attackers may expand their targeting to additional countries in the future.


The compromised Telegram X versions have also surfaced on third-party app stores including APKPure, ApkSum, and AndroidP, where they’re fraudulently distributed under the official Telegram developer’s identity despite having different digital signatures from legitimate versions.
Unprecedented Capabilities
What distinguishes Android.Backdoor.Baohuo.1.origin from typical Android malware is its extraordinary level of account manipulation.
Beyond stealing credentials, chat histories, and personal data, the backdoor can surgically conceal evidence of compromise by hiding unauthorized device connections from the victim’s active sessions list.
The malware can autonomously add and remove users from Telegram channels and join chats on the victim’s behalf while hiding these actions entirely.
The backdoor operates through three distinct modification variants, ranging from direct embedding in the messenger’s main executable to dynamic loading via LSPatch tool injection.
Regardless of deployment method, the malicious messenger remains fully functional—a critical feature that prevents user suspicion while enabling complete attacker control of messaging functionality.
The malware’s command and control architecture introduces a breakthrough technique in Android threat landscape.
While earlier variants relied on traditional C2 servers, current iterations leverage Redis database infrastructure for command delivery—a unprecedented approach in mobile malware.
This dual-channel system provides operational redundancy: if the Redis connection fails, the malware automatically reverts to standard C2 server communication.
The backdoor extracts continuous data streams including SMS messages, contact lists, and clipboard contents.
Particularly alarming is clipboard interception capability, which captures sensitive information when users minimize the messenger—potentially exposing cryptocurrency wallet seeds, passwords, and confidential documents copied for legitimate purposes.
Every three minutes, the malware uploads device permissions, screen status, and Telegram authentication credentials to attacker servers.
Doctor Web’s telemetry indicates approximately 3,000 distinct Android devices have been compromised, spanning smartphones, tablets, television boxes, and even vehicles with Android-based operating systems.
While Brazil and Indonesia represent primary infection vectors, the global distribution underscores the threat’s widespread reach and the sophisticated infrastructure supporting ongoing malware evolution.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




