Telerad Bangladesh Ltd, a prominent teleradiology company, has fallen victim to an alleged cyber attack.
The group behind the attack, SiegedSec, claims to have successfully breached the company’s network, gaining access to sensitive information such as documents, database files, and source code.
The news of the Telerad Bangladesh cyber attack emerged when SiegedSec posted a message boasting about their accomplishment.
The group revealed the extent of their intrusion in a mixture of playful and malicious tones. The provided sample included a report and X-rays, further highlighting the severity of the breach.
The Cyber Express team has reached out to Telerad Bangladesh Ltd for confirmation and additional details regarding the incident. However, as of now, the company is yet to respond.
Telerad Bangladesh cyber attack explained
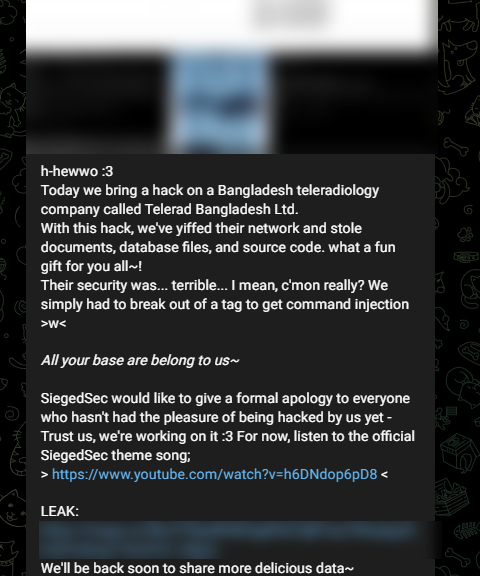
SiegedSec, known for its audacious exploits, did not shy away from showcasing its hacking prowess.
In their message for the Telerad Bangladesh cyber attack, they expressed astonishment at the lackluster security measures employed by the company.
The hacker group claimed that breaching the company’s network was effortless, pointing out specific vulnerabilities like a command injection that allowed them to penetrate the system.
“h-hewwo :3 Today, we bring a hack on a Bangladesh teleradiology company called Telerad Bangladesh Ltd. With this hack, we’ve yiffed their network and stole documents, database files, and source code. What a fun gift for you all~!” reads the threat actor’s post.
While SiegedSec took a light-hearted approach to their post, their actions cannot be taken lightly. The consequences of this Telerad Bangladesh cyber attack could be severe, both for Telerad Bangladesh Ltd and the individuals whose data may have been compromised.
The alleged leaked documents, database files, and source code pose a significant threat to the company’s and its clients’ privacy and security.
The potential misuse of this sensitive information could have far-reaching implications, including identity theft, financial fraud, and reputational damage.
The gravity of the situation was further emphasized when FalconFeedsio, a trusted source of information in the cybersecurity community, shared screenshots of the threat actor’s post on their Twitter account.
The screenshots captured the brazen nature of SiegedSec’s message, indicating the terms of the Telerad Bangladesh cyber attack.
SiegedSec and Telerad Bangladesh cyber attack
In the wake of the Telerad Bangladesh cyber attack, it is crucial for the company to take immediate action to mitigate the damage caused and bolster its cybersecurity infrastructure.
The Telerad Bangladesh cyber attack by SiegedSec is a stark reminder of the risks businesses face in the digital landscape. As technology continues to evolve, so do the methods employed by threat actors.
It is imperative for organizations to adapt and stay one step ahead by investing in robust cybersecurity measures and remaining vigilant against emerging threats.
SiegedSec emerged prior to the Russian invasion of Ukraine, with a focus on undermining the security of its victims, as implied by its name.
SiegedSec does not discriminate in terms of industries or geographical locations when selecting its victims. They have successfully targeted companies across various sectors worldwide, including healthcare, information technology, insurance, legal, and finance.
Noted recent victims of the group include Atlassian and Murphy Oil.
Since their formation in February 2022, SiegedSec has gained unauthorized access to sensitive data, leaked emails, and stolen databases from several companies.
They have shared the stolen data on various forums, but notably, they have not employed ransomware or attempted to sell the information. Due to the predominantly small business victims, few of them have publicly disclosed the cybersecurity incidents caused by SiegedSec.
Evidence suggests that SiegedSec has ties to GhostSec, as members frequently share GhostSec’s announcements on SiegedSec’s channels, note researchers.
Analysts have observed SiegedSec defacing or compromising at least 11 websites using offensive language and graphics. In April, the group claimed responsibility for defacing over 100 domains and hinted at their ongoing access. They have also been linked to the compromise of several thousand LinkedIn profiles.
In May, SiegedSec announced a successful attack on an Indian online news distribution outlet, NewsVoir. The group leaked two archives: one containing 27GB of stolen documents from the organization’s servers, and another consisting of hundreds of gigabytes of source code and API data.
Media Disclaimer
This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
