The LockBit ransomware group has claimed responsibility for the alleged China Daily data breach, adding China’s first national daily English-language newspaper to its victim list.
However, the incident has not been confirmed by the organization. The official website of China Daily was accessible at the time of publishing this report.
China Daily data breach uncertain
Cybersecurity analyst Dominic Alvieri tweeted a screenshot from LockBit’s leak website that threatened to publish all the exfiltrated data from the China Daily data breach.
China Daily News owned by the Central Propaganda Department of the Chinese Communist Party has been breached by LockBit,” read Alvieri’s tweet as he posted the below image.
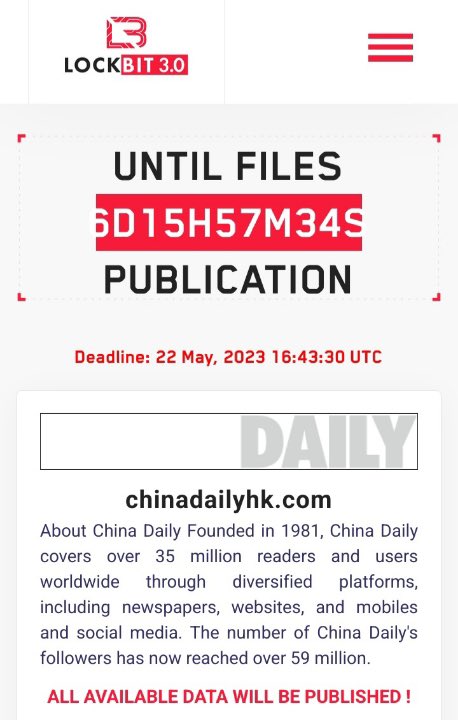
Following the alleged China Daily data breach, LockBit has set 22 May, 2023 as the deadline, indicating that the group has likely made a ransom demand for the stolen data, which they have threatened to leak next week.
The Cyber Express has reached out to the news publication for confirmation on the China Daily data breach allegation and will post an update once the response is received.
The China Daily and its popularity
China Daily is the widest circulated English-language newspaper in China. As per its annual report of 2014, China Daily is officially administered by the State Council Information Office (SCIO).
The SCIO reportedly conducts frequent sessions with China Daily’s journalists and editors to guide them on the content that should be published.
Early this May, the China Daily Hong Kong Edition bagged eight awards in five categories in the Hong Kong Awards 2022.
During the award ceremony, Chief Executive John Lee Ka-Chiu spoke about technology and development including the much talked about ChatGPT.
Lee said that human qualities like emotions, empathy, and care cannot be replicated by AI technology, at the Hong Kong News Awards.
When the hacker was hacked!
A 2022 Cyble blog disclosed a Twitter user who allegedly breached the ransomware groups’ servers. The presently suspended account of a user, who goes by the name ‘Ali Qushji’, was found leaking LockBit’s ransomware also called ‘LockBit Black.’

Ali tweeted, “Our team managed to hack several LockBit servers as a result, Builder LockBit 3.0 was found on one of the servers.” A password with a link to the builder was placed to download the hacked data of the hacker for free.
The Cyble blog further noted that the intent of the Twitter account holder was to leak the LockBit ransomware builder wherein they also answered several questions posed by readers on the social media platform.
LockBit on a hiring spree for better developers
LockBit 3.0, which is also known as LockBit Black, is the latest type of ransomware from the LockBit family. It was first detected in September 2019 and aims at organizations that can pay significant amounts of ransom money. Furthermore, it is capable of self-propagation.
This most recent variant, discovered in late 2022, uses encryption methods to steal files from compromised devices and asks for payment in exchange for their recovery. According to a report by Sophos, LockBit 3.0 retains most of the features of LockBit 2.0, but it also introduces new actions that make it more resistant to analysis.
Post the leak LockBit 3.0 builder, the group has evolved to create stronger software. The group even offered to hire developers who can test components, search for errors, and has good logical thinking.
The ransomware group has also been working to attack mac OS devices which made headlines in April, this year.

The ransomware group has left no sector untouched from cyberattacks. A Cyble blog published this March illustrated how the group hacked most systems related to professional services followed by construction, transportation and logistics sector.
“The ransomware group has been targeting several industries across these countries, with most attacks on entities from the services industry. Healthcare, BFSI, and Government organizations are also among the worst-hit sectors,” concluded the Cyble blog.
In some cases, affiliates must use a 32-character password to launch the ransomware binary. The attack process typically involves infecting a targeted device, encrypting files, deleting particular services, and altering the wallpaper.
If the ransom is not paid, the stolen data may be sold on the dark web. LockBit 3.0 is notorious for exploiting Windows Defender to deploy Cobalt Strike, a penetration testing tool, resulting in a series of malware infections.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.