The newly established hacktivist group known as “Five Families” has publicly claimed responsibility for orchestrating a cyber attack targeting a computer hardware accessories manufacturer.
The manufacturer, Biostar, operates globally and has its headquarters in Taiwan. As a result of the Biostar cyber attack, Five Families managed to illicitly obtain sensitive data belonging to both customers and employees.
Nevertheless, the Biostar cyber attack remains unconfirmed at this time. The Cyber Express has initiated contact with the company and will provide an update to this report once their response is received.
Biostar Cyber Attack, What the Hackers Have Claimed
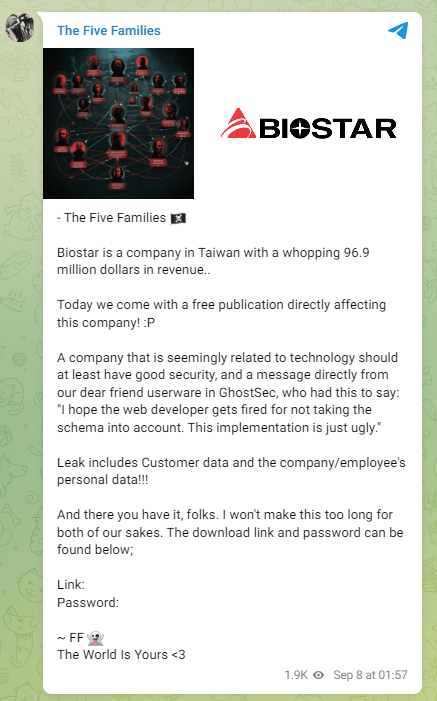
“The Five Families hackers collective claimed to have unauthorized access to the database from BIOSTAR (http://biostar.com.tw)…,” tweeted the Threat Intelligence platform Falcon Feeds. They shared a screenshot of the Telegram announcement made by Five Families claiming the Biostar cyber attack.

The hacktivist collective first talked about the revenue generated by Biostar which was mentioned to be $96.9 million. Making fun of the cyber attack on Biostar they wrote, “Today we come with a free publication directly affecting this company!”
They challenged the cybersecurity infrastructure of the company which is into technology. While admitting the involvement of another cybercriminal group GhostSec in the Biostar cyber attack, they made derogatory remarks about the security measures missed from being implemented by the company’s web developers.
They concluded the message on Telegram by posting two links including the download URL for the exfiltrated data from the Biostar cyber attack and the password for accessing the same. The post received 1.9k views at the time of reporting the Biostar security breach by Falcon Feeds.
The website of Biostar was accessible at the time of writing when checked by The Cyber Express.
Biostar has a global presence with its branches in China, the Netherlands, and Latin America. The company designs desktops, motherboards, industrial personal computers, video cards, thermal grease, and system-on-chips among other products.
Cyber Attacks by Five Families
Five Families was formed in August 2023 with the main members of five cybercriminal groups collaborating to collectively launch massive cyber attacks.
Leaders from ThreatSec, GhostSec, SiegedSec, Stormous, and Blackforums formed the Five Families.
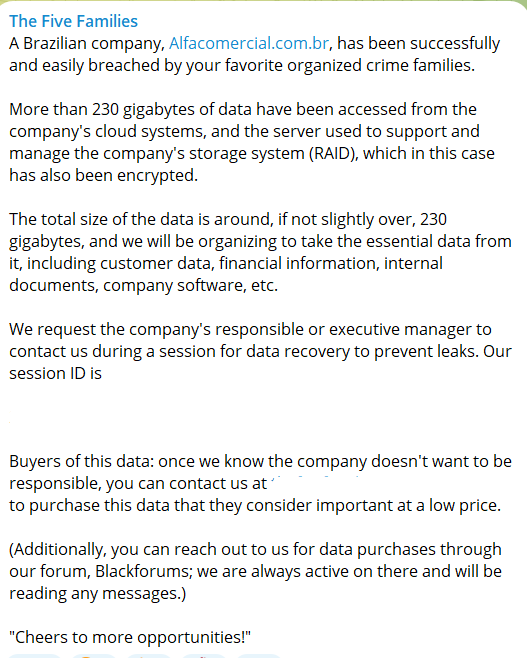
After announcing the Five Families with the intention of ‘better unity and connections for everyone in the underground world,’ they claimed a cyber attack.
A cyber attack on Alpha Automation based in Brazil was targeted by them.
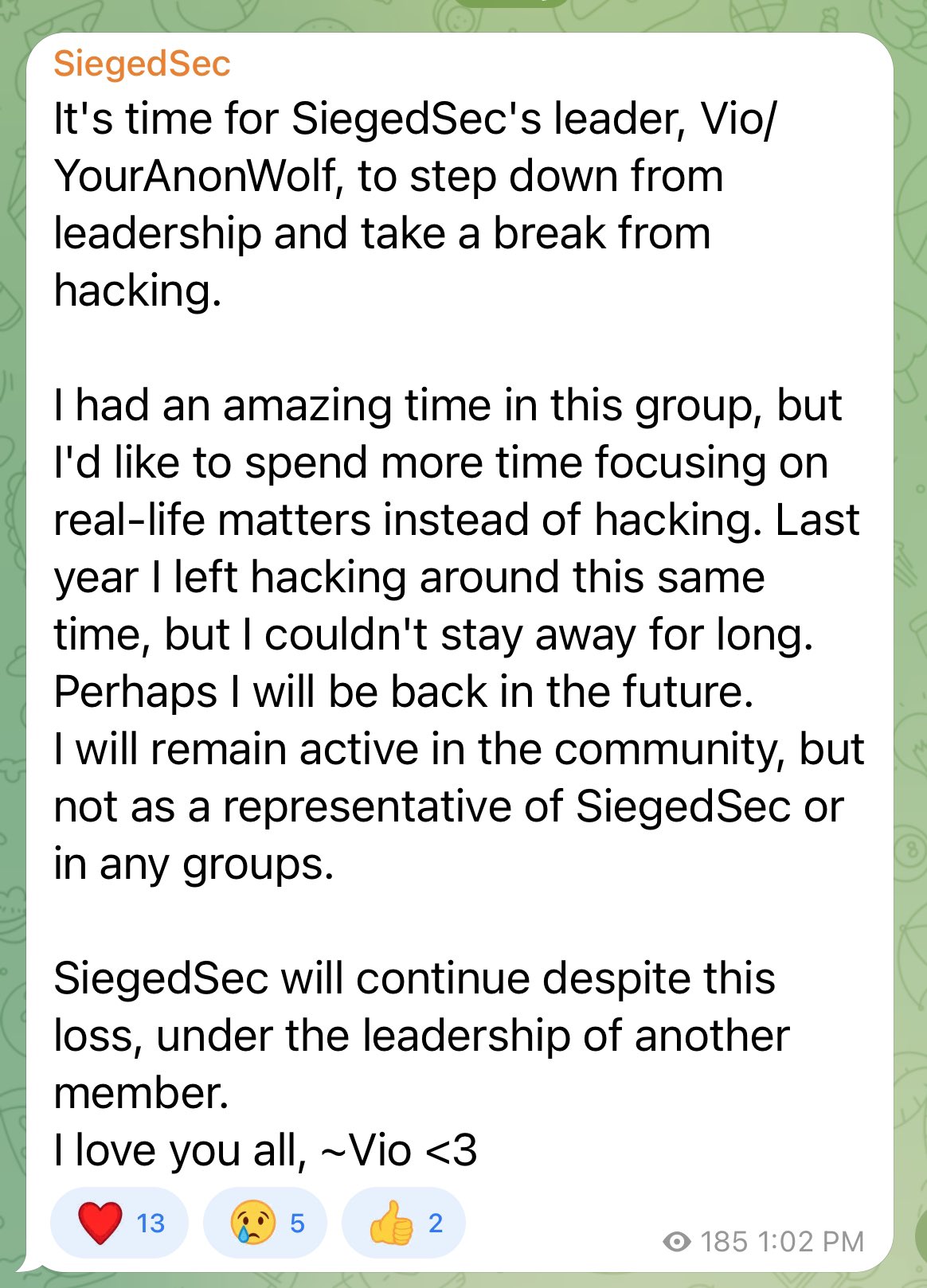
On September 7, the group announced about a member leaving the Five Families.
The member from the group SiegedSec, Vio/ YourAnonWolf decided to quit the Five Families. They also took a break from hacking, read the Telegram post.
Addressing the need to change focus away from hacking, AnonWolf wrote, “..I’d like to spend more time focusing on real-life matters instead of hacking. Last year I left hacking around this same time, but I couldn’t stay away for long.”
The hacker declared their intent to remain within the hacking community. However, they emphasized that they will not affiliate with any groups, including SiegedSec or any others.
Most of the arrested hackers including Arion Kurtaj from the Lapsus group and his accomplice who was not named because of their age were found to be teenagers. Despite the skill to impact the most sophisticated security, they remain attached to crime forums.
Arion Kurtaj, 18, was also assessed unfit for trial by a team of psychiatrists. Kurtaj breached the systems of Uber, Revolut, Rockstar Games, and Nvidia Corp among others. He was charged on the counts of blackmail, fraud, and computer misuse act.
Kurtaj was also reported to have recruited office insiders to gain access to the organization’s systems. While he was capable of committing all the crimes including buying the Doxbin website in 2019 to gain access to the data dumped on it when he was younger, he was deemed unfit for trial.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.